In this episode of Security & GRC Decoded, Raj Krishnamurthy sits down with Vivek Madan to unpack what it really means to run a modern GRC program inside a global cybersecurity company. Drawing from his journey across networking, security engineering, risk, and compliance, Vivek shares how GRC can function as a true business enabler—opening markets, accelerating revenue, and strengthening trust. This conversation stands out for its practical frameworks, real-world stories, and honest discussion about friction between engineering, security, auditors, and compliance teams, giving listeners a grounded view of how GRC works when it’s done right.
Key Takeaways:
- GRC works best when it is positioned as a growth enabler that unlocks new markets, not just a compliance checkbox.
- Strong governance establishes foundational rules that allow security and risk decisions to scale consistently across the business.
- Storytelling is a critical GRC skill—people align with compliance when they understand the “why,” not just the requirement.
- Common controls frameworks reduce complexity when designed intentionally across global, application-specific, and product-specific needs.
- Automation matters, but process automation is just as important as technical automation to reduce compliance friction.
What You’ll Learn:
- How GRC enables business expansion into regulated and global markets
- Why compliance resistance exists—and how to overcome it
- A practical 50–35–15 model for common controls frameworks
- How to balance continuous assurance with annual audits
- What modern GRC leaders look for when hiring talent
This podcast is brought to you by ComplianceCow — the smarter way to manage compliance. Automate evidence collection, eliminate screenshots, and scale your program with confidence.
Learn more: https://www.compliancecow.com
Watch more episodes: https://www.compliancecow.com/podcast
Connect With Our Guest:
Vivek Madan | Director of Security, Risk, and Compliance | Fortinet
Connect on LinkedIn: https://www.linkedin.com/in/vivek-madan-cissp-ccsp/
Rate, review, and share if you enjoyed the show!
Subscribe to Security & GRC Decoded wherever you get your podcasts:
Spotify: https://open.spotify.com/show/5pigcMwOrYIA6d9OOOsxqr?si=416b82ab5c474683
Apple Podcasts:https://podcasts.apple.com/us/podcast/security-grc-decoded/id1795144450
Raj Krishnamurthy (00:00)
Hey, hey, hey, welcome to another episode of Security and GRC Decoded. I’m your favorite host, Raj Krishnamurthy. And today, we are fortunate to have Vivek Madan joining us. Vivek has 18 plus years in cybersecurity, security, and compliance. He’s worked at companies like LNT, Palladian Networks, Citi, Royal Bank of Scotland, and now at Fortinet. He heads the GRC program at Fortinet. Vivek, welcome to the show.
Vivek Madan (00:00)
Thanks
Raj Krishnamurthy (00:02)
Vivek, in your current role as the leader of GRC, what excites you the most?
Vivek Madan (00:10)
Well, ⁓ there are two aspects to it. One is the role itself. I’ll come to that later. But what excites me the most is ⁓ the wonderful team that I have, you know, and that I’ve built over the last seven years. So when I joined the company, it was just me and compliance, you know, to begin with. And now we’re a team of seven people and growing. So, and the team is, you know, very diverse, multicultural, you know, people from, you know, all over.
the globe, is very, very nice. So to share this journey with all these folks and building this from scratch has been really, really good. What excites me about GRC ⁓ in general is the fact that ⁓ how it can enable a business to grow ⁓ tremendously. ⁓ While we think that compliance has been just a checklist from that, think it has built that trust over time and it acts like a currency pretty much now.
where you can ⁓ spend it and gain business and how it opens your business to different markets. I think ⁓ that’s what excites me to bring ⁓ the growth, the ⁓ escalation, sorry, ⁓ acceleration in the business growth overall. Yeah.
Raj Krishnamurthy (01:25)
You see, be GRC as a business enabler. That’s fantastic. You started as a network analyst. You became a security engineer. And then you moved into GRC. Why?
Vivek Madan (01:27)
Absolutely, 100%.
Yeah, it’s a very ⁓ interesting story actually. ⁓ Back in 2008, you’re absolutely right, I started as a network analyst and I was looking at firewalls and firewall logs and whatnot. But the story goes back a little bit more. When I was actually in college, ⁓ there was one of my uncle actually got breached. He had a Gmail account and somebody did a very simple phishing attempt on him and he was ⁓ click bait, he clicked on the link.
and they had access to his bank account. Back in 2000, I’m talking about 2005, six, I think the controls were not that stringent also. And somehow, ⁓ the hacker got access to his account and his money was stolen. And I was just fascinated by this idea that you can actually make a career out of it. So I was always back of my mind fascinated by cybersecurity in general. But when I joined L &T, ⁓ that’s what I got as my first project. Actually before that I in ISO 20,000, a quality management for a year.
And at that time I was also fascinated by auditors, so a mix of both. I faced auditors for about a year and the whole idea of you sitting in a room and your executives are sitting and the auditor comes in and is asking all kinds of questions, that kind of fascinated me. So these combination was in the back of my head. And then finally when I, on the network analyst journey also, there’s obviously a component of security layer at layer three, network layer. And with that, with those combinations,
you ⁓ know, that kind of helped me think about cybersecurity in the future. And lucky enough, I was actually, I went to UK after that for about three years. I worked in a city called Belfast in Northern Ireland. And I was ⁓ sent as a ⁓ IT lead, IT infrastructure lead with my little background on my network side. So I had to build the office kind of from scratch, set up bunch of servers and VMs and network devices and have some couple of ISPs. ⁓
backup redundancy, some sort of, know, availability that I can provide to the local people. And the client actually was Citibank. And a couple of years down the line, they saw this office was progressing from 10 people to now 50 to 100 people. And they wanted to see what kind of controls do we have. And that’s when, you know, they planned a local audit, right? So somebody flew from London. And again, that auditor phase, you know, came in front of me and I had to prepare now the entire office to set up for compliance, you know.
So I was making sure that there are access processes or badging or the data center that we had the small server room, had all kinds of controls, the CCTV, virtualization, hardening, logging, monitoring, all those controls sort of came into in front of me. ⁓ And we actually then prepared the center eventually for ISO 27001 audit also. So it was all coming and being thrown at me in flashes and ⁓ post that when I went back to India after three years spending in UK.
You know, my boss was very happy with my work and he basically said, hey, you know what department you want to go next? I’m like, I want to choose cybersecurity and he introduced me to the CISO of the company and that’s how I landed in the department and you know, the first project I did in the GR in the cybersecurity department was actually transitioning from ISO 27001 2005 version to 13 version and I acted as an internal auditor. So that whole cycle, you know, whatever.
Sometimes your envisioning comes in front of you. So I played the role of internal auditor and successfully implemented that project. And then from there, moved to US with a different role. But mainly in India, was compliance and ⁓ getting familiar with some policies at a very high level. That was ⁓ it in India. And then post that in UK.
Raj Krishnamurthy (05:26)
No, that’s a fascinating story, Vivek. And there are very few people who have sort of touched the metal, right? And I’m using the word, proverbial word, right? Setting up networks, setting up local offices, right? Managing networks and moving into a GRC space. And what is very interesting is that
You run the GRC program for a networking company. So does that have got anything to do your networking background?
Vivek Madan (05:48)
Amazing.
Yeah, no, it has nothing to do with that actually. You know, when I came to US, finally on an H1B visa, my first project actually was again for a bank. Okay, it was a Royal Bank of Scotland. So when I was working in UK, I was working for a US bank and now I’m working in US working for a UK bank, which is also interesting. Why? Because ⁓ when you work for such a large bank, heavily regulated, you pretty much work in a silo. Okay, when I was working in UK, I had no idea who was setting up the policies.
who had the governance, who was carrying that governance piece or all of that. So you’re working, I was doing that there. And then when I came here in the US, again, I had no idea who was setting up the policies. There is no interaction, no access to that team. And I was just doing risk assessment for a couple of years. They gave me a checklist. There were very critical, sensitive applications, obviously handling financial data. But my job was mainly to do risk assessments on them.
you know, coordinate penetration tests, coordinate vulnerability scanning, make sure risks are remediated and are in appetite, right? That was my main goal. And also do some risk assessments on very heavy applications, you third-party integrations, integrations, local integrations, system-to-system integrations, all of that. And ⁓ then one fine day, I was not even looking for a job, to be honest. You know, a LinkedIn message, ⁓ you know, came in my inbox that, are you looking for a change? And we’re on the West Coast.
So idea of California Silicon Valley always sort of excited me. I thought, you know, let’s give it a try. And I gave that interview. And here you go. I was here at Fortinet and I’ve been working with them for the last seven, eight years. And I don’t think they audited me on network security at all, like network domain per se. Right. The idea was I was actually a risk and compliance manager when I was hired and they basically asked, Hey, can you build the program, you know, from ground up? That was the idea. So that’s how I landed here.
Raj Krishnamurthy (07:29)
Okay.
Makes sense. And
maybe this is an obvious question Vivek, but I want to get your perspectives. What is your opinion of G, R and C, particularly what we call as the second line of defense? How do you see that fitting in?
Vivek Madan (07:55)
Yeah, no, I the ultimate objective of GRC is to somehow provide security, right? Ultimately, also enable business. But basically,
If I remember, you one of the examples back in 1906, okay, there was a novel written by, I think Mr. Sinclair was his name. It’s used to, it’s called The Jungle. Okay. That novel became quite popular in Chicago. And you know, why? Because he wrote The Truth. And The Truth was there was a food adulteration going on. Okay. A of people were dying and getting diseases because of, you know, meat industry. They were not regulated at all.
And to the point that that novel became so famous, people literally came on road and there was a lot of marching. And within days, not even weeks, within days they had to kind of announce a new regulations called FDA now, right? Food and Drug Administration. And that regulation kind of, even today drives ⁓ how restaurants can cook food or how they can store food and hygiene and all of that, ⁓ which is at least some basic minimum standard that has been built. So I think governance plays that really important role.
where you can define rules and policies and there could be, know, discipline reaction attached to it, which kind of drives at least the foundational set of rules, you know, that should be governing how we operate, right? How we operate security, how we operate sort of controls, all of that. So I think governance plays that very, very important role. Then come obviously risks, risk again, you know, the whole idea I think behind risk is to how do we, ⁓ you know,
identify threats, assess them, then treat them in a way where we can prioritize them because risks are not going to go away. If I’m driving to my office and I have very, very important meeting to deliver tomorrow, I’m always carrying the risk that I may not be able to reach on time. But I want to make sure, what do I prioritize? I make sure my car is in a good condition. I’m sleeping at time. I have a good alarm set up. I’m taking half an hour, one hour buffer for the traffic. So all of that, managing those threats that can…
protect you and you meeting your business objectives and underlying security, I think is another important element, a risk. And when it comes to ⁓ compliance, I think compliance, actually I have another ⁓ example that’s striking me because last week my wife actually is trying to open a preschool at home. ⁓ And she used to carry, mean, have the same similar business in my last home. But the difference in this home is we have a pool in the backyard.
So they gave us two months in advance, they gave us a big rule book that, this is what you have to implement, this is your policy, do this. And ⁓ I made sure that we went through every single item one by one and set up the home like that. Whether it’s ⁓ in your kitchen, make sure there’s ⁓ no ⁓ chemicals under your sink and things like that. And pool also, you used to have a certain kind of fence and it has to be four inches from the side and two inches from the bottom and it should be five.
five feet high, should be self-latching, self-closing, all of that. So I made sure, I called a professional and made sure that, you know, that is implemented. But then comes the day of compliance. You know, the lady inspector visited and she checked everything. She’s like everything, everything looking great. But then there was a rule that there should not be any object where kids can climb near the fence that can then, they can jump in the pool. Okay. And ⁓ you know, there was a small tree that I had already cut thinking that this could be one object.
But then what she found was that you have this side fence connected to the backyard fence, basically. The pool fence was connected to backyard fence and there was a horizontal beam that was at least at a one feet height. So she said, know, kid can climb on this. And I was just thanking her, you know, that I’m glad that there is a rule book. I’m happy that there is a compliance check because otherwise I won’t even notice this issue, right? It will go unnoticed. And imagine the kind of liabilities it can bring to my business. This is a very sensitive business.
at the end of the day is actually protecting me and my wife and our business at home. So sometimes we think that compliance can be a burden, but this kind of compliance checks, audits, I think they help enable business and protect you against those liabilities or making sure that you’re ready to operate basically. So I think that’s how governance risk and compliance play the role.
Raj Krishnamurthy (12:20)
I love the perspective, and I think it’s a very, important perspective to share. But quite often, I think what we notice within an enterprise is that the engineering teams and the DevOps teams have a reservation. I’m being very polite. I have a reservation against security. The security teams have a reservation against GRC. And the GRC teams have a reservation against auditors.
And I don’t think it is not that they lack the understanding of this, but then why do you think there is this resistance and what can we do about it?
Vivek Madan (12:55)
Yeah, I think resistance is there ⁓ because
is how we present that at the end of the day, how we interact with those teams. I think being in a cybersecurity company right now, at least there is that good majority, that cybersecurity is what we are trying to achieve at the end of the day. So even in marketing department, sales department, R &D, DevOps, all those teams, they understand that security is important and why this function exists in the first place. And then I think it’s also a cultural thing, how you build your relationship
with all these teams, how can you convince them that actually it is a business enabler rather than anything else, right? So for example, ⁓ I’ll give an example. So one of the products that we had, for example, we were doing good in the US as a business, okay? But we wanted to explore that into other markets. And whenever you go in the other market, there was always a question, hey, do you have…
let’s say an asset 27,001 or any foundational certification. That’s the criteria to even go to the next step. Because you are at a level where you are competing with top companies in the world, right? And they expect you to have those foundational basic certifications, for example. And then we had to obviously create that use case and convince that, okay, this is now needed. In fact, we didn’t need to convince them. The sales team…
kind of convinced on our behalf that, hey, there is a demand and market for this product in this region. Similarly, you know, even in the regulatory industry, right, let’s say you want to do business in ⁓ car manufacturing sector, you know, they probably ask for your your TISACs or if you’re doing business in Italy, they’ll ask, you know, Italy government, especially they’ll ask you for an ACN certification, right? If you go to Australia and ask to work with defense, they’ll ask for your DIP certification, right? So to open yourself to those markets, ⁓
you know, ⁓ that use case is kind of created by our sales org. And as long as that message then from the top gets communicated to all the departments, including product teams, including R &D teams, they know that this piece is important, that this compliance piece is important because our ultimate goal is to grow into a business, into a new market. I think that also helps. So that’s another angle ⁓ I think that can help.
Raj Krishnamurthy (15:18)
No, I think that’s a great point. But I want to go back to the core of what you were saying. So one part is that as you enter into new markets, and delay in compliance causes a delay in launch, delay in revenue recognition, a cascading effect on both the top line and the bottom line of the company. And everybody understands it. But I want to go back to the core example that you talked about, the beautiful example that you gave about this daycare that you were trying to open. And there was this bar that was there.
Vivek Madan (15:35)
100%.
Raj Krishnamurthy (15:46)
And what you related to was the possible hazard, right? That one of those children could have gone over it and it could have had an adverse effect and you were able to empathize with that, right? And that is why you’re saying that you’re thanking the compliance, the person who walked in, right? The inspector. The question I’m asking is that at a core level, why are most operators, and I don’t want to sort of, I’m not trying to single out an engineer. I’m an engineer myself, right?
Why are we not able to empathize with this idea of compliance? And why do we mostly think of this as a check the box item in cybersecurity?
Vivek Madan (16:24)
Yeah, no, think definitely that issue is there. again, I can say what works for us the best, right?
First of all, we again try to create those nice relationships with all these people, right? From engineering background or R &D teams and kind of explain to them through those metrics and reporting dashboards that how this all is converting into ARR. This is not just a checkbox. This work is helping the business to grow. That’s one. Second, I think the reluctance can be if you just make rules without good guidance.
if you make rules without good story to tell, like why we are doing something, why has to be very, very important. And as long as you can explain through trainings, through those communication that, you know, this has happened. So for example, supply chain risk management, right? We see a solar wind issue. And before that, you know, maybe for supply chain perspective, the compliance may not have been, you know, where it is now, right? At least growing in that direction. We were very simply and easily able to explain.
to anybody who was part of the supply chain that look at this, what has happened. And now we need to do X, Y, Z and here are a set of new policies. And I think everybody was kind of ready to adopt to that new model or new design that we were proposing or new architecture that we were proposing, new processes, policies, all of that. So I think, most of the times, if you’re putting compliance as a…
sort of a road blocker that hey you have to pay this toll before you go versus if you can explain why paying a toll is important that it can help you keep the roads clean keep the roads moving you know there will not be any pits all along this way and you know you will be landing on the other side safely if you can build that story and and hopefully then they will empathize with you with you right and I think in our company again the difference is being a savage credit company everybody has that kind of mindset so
they understand that, you know, why we are doing certain things. Yeah, just wanted to say that.
Raj Krishnamurthy (18:37)
I think the GRC teams should take a very active role in storytelling because the idea of why I think is better communicated through better stories that people can relate to is, I see that point and I think that’s a very powerful statement that they are making. And the question then becomes, how do you connect with your auditors
Vivek Madan (18:54)
100 % yes.
Raj Krishnamurthy (19:04)
Because who are in many, let me rephrase the question. So you are taking the responsibility as a second line of defense, as the GRC team, to be able to communicate this internally on why this is important, right? How does that flow with the auditors? Do you have to take the responsibility to convince the auditors of why you have some of these controls as well? Or do they dictate to you what controls you should have? What typically happens?
Vivek Madan (19:30)
Yeah, no, I think.
depends what kind of auditors we are doing, right? There are, so for example, if you have something like Sarban-Soxley, right? Sox compliance, those controls usually are dictated by auditors. You have preset standard controls and they expect you to implement those and be ready and make sure their design is good, the effectiveness of those controls are good, you have the right evidence, you have good processes, all of that. Versus, you know, there are some frameworks that you…
end up choosing just because you want to grow into different markets. If you go for ISO 27001 or SOC to type two, then it’s up to you. And there is flexibility there, right? Based on what your business objectives are, what your assets are, what you’re trying to protect, you define your own set of controls, right? And that’s why these frameworks are a little bit flexible when it comes to ISO 27002 or even cost of principle. It won’t dictate control to the granular level. It’ll tell you, do ABC, sorry, do, you know,
things in certain way and as long as you’re meeting a business objective, you know, you can define sort of your granular underneath layer, right? So, yeah, I think when it comes to any regulatory audits, usually it’s dictated by the auditors, but on the other side, we are able to, for the most part, as long as the controls are industry standard, you you don’t want to create controls that it’s not effective or the design itself is really bad, as long as you’re creating controls within those parameters.
⁓ then usually you are able to dictate what your controls are going to be and how you’re going to protect your assets and convince the auditors that this is the true controls that are going to help meet the business objectives, if you will.
Raj Krishnamurthy (21:10)
Okay, I think the GRC teams have a very, very difficult job in my opinion. In my opinion, one of the most difficult jobs. The reason is that on one hand, you have to understand technology. On the other hand, you have to understand security as a domain. the third, that is. On the third perspective, you need to understand the business context and the threats and risks that are contextual to you.
And then you have to marry all of this to determine what is more common sensical for you to be able to put together these controls and communicate and ⁓ convince or sort of communicate and be in alignment with your auditors. Is that a fair, is that the fair way to put it? Do you agree?
Vivek Madan (21:48)
Thank you
for empathizing with us. Yes, absolutely. Yeah, you nailed it.
Raj Krishnamurthy (21:52)
And how do you… so in your experience, Vivek, how do you create that culture? How do you create the culture where you can build these amalgamation of skills, right, within the GRCD?
Vivek Madan (22:05)
Yeah, no, I think the building a team comes from, ⁓ I guess, first you need to understand, again, what your business objectives are. What is it that you’re trying to protect? What is it you’re trying to build? For example, ⁓ if you’re working with lot of third parties, if you have lot of vendor interactions, you want to make sure that you have a very solid third-party risk management process where…
You are understanding the exposure to those vendors. You have certain criteria. You build a very nice program around it and protect ⁓ any data exchange or any system interaction that you might have with those vendors and protect those. Similarly, if you ⁓ you want to also build something and start something with something very simple. You don’t want to, let’s say, create ⁓ all kind of risk matrix and quantification. ⁓
behind it and kind of confuse the audience what we’re trying to do, right? This all happens very slowly, I would say. ⁓ So something very simple where you can subjectively analyze, again, these are my assets, these are my threats, these are my vulnerabilities, these are my ⁓ controls that I would like to imbibe, let’s say from a certain framework, you define all of that in a nice way and you kind of build your risk register and your risk management framework. Similarly, on compliance side, depending on…
you know, where the demand is, you know, are you a SaaS platform? You know, does SOC 2.0 type 2 make sense to you because you are operating in US or do you want to operate globally and that’s why you have to expand into ISO 27001? Are you manufacturing hardware? You know, do you need to involve now maybe, you know, the teams that are managing SBOMs or supply chain risk management or, you your contract manufacturers, which are, say based out in China or some of those Asian countries and they’re building those, you know, ⁓ underlying hardware.
⁓ Are there any intelligent components that are being built outside your company? Maybe you have, I don’t know, some chips that are being designed, right? So all those different parameters ⁓ kind of drive what you want to build within GRC. And your compliance, the third bucket I was mentioning, of ⁓ rotates around that, right? So where are you operating? What is your go-to market? From compliance perspective, how do you want to…
what regulation regulatory requirements you want to meet right are you operating in Europe obviously there’s a need for GDPR or you know similarly you know other other countries so yeah so I think ⁓ building ⁓ a GRC you know obviously you need a good skill set ⁓ not just somebody who understand checklist and can tick the boxes you know you need somebody who has spent some time in implementing those controls understanding security controls what the underlying objective is
Somebody is not just saying, hey, data trust is encrypted. Yes, encrypted. OK, check the box. Somebody who understands, what does it mean? If you’re encrypting data, it’s not just your databases. Maybe it’s in memory. Maybe it’s in your backup drives or archive. So is it going through and through? So somebody who understands also is very, important. ⁓ In TPRM, for example, another example.
I have seen people who are building their career in that domain, but what they do is again, you know, just checklist, checklist based audit. You have 200 questions you assigned to the vendor and they are just, you know, saying all 200 compliant. They give a SOCT report. They give you an ISO report. You’re like, yep, all check boxes. They have a pen test report. There were five findings. They’ve already closed it. And you just check the box and say vendor is approved. Right. Is that really sufficient or do we need to do more? Right. I think anybody who has implemented these controls or understand all the
Sorry, all the OSI layers, right? How do they function, you know, at a very high level? ⁓ And sorry, not a very high level, but even granularly, how do they operate these controls? Anybody who understands can do GRC better. This is just one example. But yeah, so again, you need to have good technical skills ⁓ also along with, ⁓ you know, other skills.
Raj Krishnamurthy (26:08)
Do you use common controls framework? How effective are these in your experience from your past experience? How effective are these common controls framework?
Vivek Madan (26:14)
Yes, we do.
I think they’re pretty effective. Again, it depends on from what framework to what framework you’re going. If you’re going from SOC to straight to maybe, let’s say, NIST, I don’t know, 53, then there’s a lot of work to be done. Versus if you’re going from SOC to ISO, it works, I think, fantastic. think what we do, what we practice in our company is a 50-35-15 ratio. So what we do is we categorize 50 % of our controls as sort of all controls.
So any framework comes in, we just apply those 50 % controls and say, hey, you have to have a good set of policies. You need to have background checks done. You have to have trainings implemented, endpoint protection. That applies to across the board. Then we have 35 % controls where we usually say that this controls language will remain same. Let’s say you have 10 different products. We’ll say the control language should be same for all 10 products of you.
But the evidence obviously is being collected from all these different 10 teams, right? So those 35 % bracket is those controls. Things like, you know, encrypt your data at rest, you know, make sure data is encrypted in transit, for example, or perform quarterly access review, you know, those kind of things fall in that bracket. And we have a common control language for those. But again, since the evidence is collected from multiple teams, we keep them separate. Then there is last 15%, which is very product niche, you know, controls. Imagine somebody’s, you know, working in cloud.
and they have limitations on how much they can back up. The capacity is not a big challenge. Availability can be maybe up to seven days of RPO, let’s say. So they can rotate their backup every seven days or maybe every 10 days just to stay compliant with respect to their RPOs versus there could be another product where availability is a massive deal. You could be dealing with, I don’t know, financial data and whatnot. You have to keep it for six years. So those 15 % controls, they fall in that bracket where controls can be very niche.
So that’s how we kind of utilize the CCF. whenever we have to upgrade from one framework to another framework, we take that data, anything 50 % we just sort of map it, and then anything residual, we take it to the next step.
Raj Krishnamurthy (28:28)
And what CCF do you use, if you can share?
Vivek Madan (28:33)
So actually, our CCF is, I would say, sort of in-house. ⁓ We took a combination of ISO 27000 and SOC 2 as a foundational sort of model. We mixed them, married them together, and created a common baseline CCF. And anything that comes in after that, we kind of ⁓ used that as a baseline.
Raj Krishnamurthy (28:37)
Okay.
Got it.
I love the way you put them into those three buckets, the R controls, the app-specific controls, and the product-specific controls. That’s a brilliant way of putting this problem. So I think it is one of the most clearest explanations that I’ve heard, so thank you. ⁓ What percentage of those controls do you think are automatable or should be automatable?
Vivek Madan (29:05)
Thank you.
Yeah, it’s amazing how these new GRC players are proposing that they can automate up to 80, 90 % of them. We have been actually playing with automation, I would say, the last one year or so. And I think we are at maybe 10 % mark, but room to grow. Being a cybersecurity company, again, you could have very diverse environments.
few things that can be on-prem, which is your crown jewel. You don’t want to touch those with any third-party tools to automate and stuff like that, right? You only want sort of outbound aggress from those no ingress, for example, right? So there are some of those limitations can exist based on company, what they do. But I think, yeah, maybe I would say at least 30 to 40 % average controls should be automated is what I feel, through tools, through maybe your GRC platform.
Through maybe some API integrations how you build them. Yeah
Raj Krishnamurthy (30:14)
And do you distinguish between corporate security controls, for example, controls that you have on deploying your back office applications on AWS, Azure Cloud, or on-premise infrastructure versus product security? Fortinet obviously builds these network products, and you have your pipeline and process by which you build and deploy these products. you, as security GRC professional, as a leader, do you distinguish between what happens in corporate security versus what happens in product security?
Vivek Madan (30:42)
Absolutely, yes. Yeah, I mean, I think it all starts with the good asset security policy, right? And how you define your assets. So you need to have data classification standards and make sure that products or in-house applications or even other applications, business applications, they all align with that mindset that at the end of the day, what is it that we’re trying to protect? Obviously, we have to protect our customer data.
products that are processing those kinds of data sets. That’s very, very important. But at the same time, if you have your financials, if you have your HR data, there are a lot of regulatory implications. If you’re managing, again, some business applications that may have ⁓ even your source code repositories, for example, right? They may not very well be part of the external facing product, but they are the backbone of your product. And if that IP is broken, if that IP is leaked, it’s massive impact, reputational damage and whatnot.
So both of those sides are equally important, I would say. ⁓ But at the same time, I think ⁓ basic principles, confidentiality, integrity, availability, what is it that applies to these assets, internal or external? It’ll apply to both. If there’s an application, let’s say you’re building an application that provides your flight uptime at the airport, availability is a very important element to that. Obviously, confidentiality doesn’t really matter.
Versus if you have, and that could be very well customer facing app, but still, confidentiality controls will be maybe a little bit low ⁓ impact for those. Versus if you have an internal application, which is not at all customer facing, very limited people have access to that, very tight controls, but inside that you have your crown jewel, that’s also equally important to protect. ⁓ So yeah, think security… ⁓
And then security controls are based on those data classifications based on the business impact. If internal application is going to have similar business impact as a customer facing product asset, for example, you have to have similar set of controls at both sides, I would say. So security will apply to both, yeah, with the same principle.
Raj Krishnamurthy (32:52)
Got it. Got it.
And I think you made a good point about, even when you are trying to do a breakdown of the 50 % in our controls and 35 % in the app-specific controls, A lot of them, I think most security orgs would want to create a paved path so that there is a common infrastructure by which every each of these product teams can build applications and services. And what role does GRC team play in consulting, advising,
and creating this or maintaining this common path from a security perspective.
Vivek Madan (33:25)
Yeah, think GRC team plays a really important role, of course, ⁓ by setting up the governance itself in the first place. You set those policies and you say that this is how you categorize your assets and based on the assets and data classification and confidentiality, integrity and availability business impact parameters, you have to implement these set of controls. So security becomes the enabler for both sides, I would say. Our product engineering team, they will come to us.
if they’re launching a new application or there’s a new &A, they want to come and ask us that how do we now bring this to let’s say Fortinet standard. And at the same time, if there’s an IT department who is upgrading, ⁓ let’s say a database from version X to now moving to cloud, something from on-prem to cloud, big architecture changes, any new API integrations, even those business applications, the gateways again becomes us.
Similarly, know, vendors, right? Vendors on both sides, be it the business application or customers, all kinds of applications, we work with third parties. And again, we become that team where we analyze the risks that third parties can bring to both sides of applications. So, yeah, I think we played a good role on both sides.
Raj Krishnamurthy (34:41)
Got it. I think one of the challenges is that what we typically see, Vivek, is the cadence at which your first line of defense operates and the cadence at which your third line of defense operates are completely out of sync, right? You are releasing hundreds and thousands of pull requests or releases a week, a month, sometimes even daily. Whereas you’re auditing once a year, at best once a quarter in some cases, right?
As a GRC team, is your role? How do you look at this cadence mismatch? Or am I asking the wrong question?
Vivek Madan (35:18)
No, no, I think this is spot on. Good question. ⁓ I think we as a GRC function, again, we need to be sort of integrated into, ⁓ on both sides. We play that middleman sort of role. ⁓ Now, ⁓ you took example of, you know, again, thousands of lines of code and check-ins and releases that we might be doing throughout the year versus what auditors are auditing. In between, I think it’s not about just passing the audit, right? You want to…
increase or enhance the security of the company. That’s also your goal. making sure that there are a right set of tools and policies and processes to be able to scan those code or be in that pipeline internally is also equally important, right? So for example, our team plays a very critical role where we have these tools to scan, you know, using SAS, let’s say, or SCA scans, you know, we are part of the pipeline, you know, if there is a
major change in the application, we are very much involved. Any changes that are documented, let’s say in Git or Jira, all those platforms, security is part of that. So they have to kind of subjectively define whether there’s a security impact from that change. And then we come into play and we analyze that risk ⁓ and understand whether we need to do something additional before we clear this for a change. So we are very much part of that process throughout the year. And then audit, when the audit comes, obviously,
you know, depending on their ⁓ scope of work, they will pick and choose a subset. But on our side, again, we are making sure that this is part of the process. It’s not just one time thing that is happening on ad hoc basis, right? We want to be part of that process and governance and compliance throughout. So we actually have all kind of weekly, monthly reports, metrics around it, making sure that, you what is happening, our changes being reviewed, our changes being tested, you know, before they are released.
or are the scanning results that coming out, are they meeting the SLA. So we those kind of guidelines that kind of support before we hit the final audit.
Raj Krishnamurthy (37:23)
Beautiful. So you, as a GRC team, you’re focused on continuous assurance. You’re continuously looking at it while you’re buffering the audit to give them what they want so that they don’t get overwhelmed based on what they’re auditing. No, that’s beautiful.
Vivek Madan (37:28)
Absolutely.
100%. Yes.
Raj Krishnamurthy (37:39)
You talked about 30 to 40 percent of the controls being automated. And that is very consistent with what we typically see as well. But what that also means is that there are 60 percent of these controls that are either semi-automated or manual. What did you do with your training? you show me? There are a of things that, I mean, you can choose to automate, you may not choose to automate, but nevertheless, it involves control owners, especially outside of the GRC teams in some way, shape or How do you…
Vivek Madan (38:05)
Absolutely, certainly yes.
Raj Krishnamurthy (38:08)
and none of them have as much an incentive or an understanding of compliance or risk as much as you do, meaning within the second line of reference, you and your team do. How do you reduce the friction of what it takes for them to be able to provide those inputs to you?
Vivek Madan (38:24)
Yeah, so ⁓ first of all, you’re absolutely right. While this 30 % evidence collection, I’m saying go and grab from system and pull that evidence straight up, right? There’s no involvement of anybody in between manually. Remaining 70%, you have to have some sort of process automation. Even if you’re not collecting evidence directly, you have to have an automation around the process where there’s a periodic task, automatic cadence based on what the control frequency is. If there’s a policy that says it needs to be reviewed every six months,
Hopefully you have a task that is assigned to somebody automatically, it’s a cadence, and somebody is now validating that it’s being done and approved and ready to go before the final audit hits. So those remaining 60, 70 % non-automated control, actually processes always should be automated, I feel. There’s always should be process automation built for 100 % of the controls, some way or the other. And sorry, what was your second question?
Raj Krishnamurthy (39:20)
Now I think you answered, how do you reduce the friction of what it takes to collect?
Vivek Madan (39:22)
Okay, yeah, so
yeah, in terms of reducing friction, ⁓ our goal has been constantly asking ⁓ week after week, which control can be automated? That is the agenda right now for the team. Whoever is managing controls, hey, how do we automate this? How do we automate this? Can we automate this? And for example, ⁓ let’s say I’m ⁓
Even very simple thing, know, let’s say there’s a monthly matrix being sent and there’s a requirement and the control says that a monthly matrix should be produced and present to the board or present to the management where there are risks and incidents and all of that should be presented. So we have been doing this for two, three years and usually an email, you know, would be sent, let’s say to the management. You can just pick that email automatically, you know, have a script that is written and picks that email and pushes into your GRC platform.
and automatically, you know, whenever that record fails, you kind of feel the control. If it is coming along, there’s obviously manual dependency of still somebody sending that email, but at least the fact that somebody don’t have to now find that email and grab it. So that process, you know, is automated. So that kind of friction reduction, you know, is our mindset as a team also. And I think that should be for any GRC team. How do I automate, ⁓ you know, wherever I can?
Raj Krishnamurthy (40:41)
And is the compliance style on engineers a real thing? I’m especially talking about those folks that are outside of the GRC team. In your experience, is that a real thing? Do they spend more time than required, which in their opinion, I think they do. I think my broader question is that should GRC take an active role in reducing the compliance style?
Vivek Madan (41:05)
Well, think ⁓ it’s a very essential thing, even for the engineering department. Because at the end of the day, imagine that you have a bunch of developers who are writing code. Unless they have a compliance view on what vulnerabilities are there in their code, unless they have a view of the dashboard when they build something, maybe on weekly, monthly, or even real-time dashboards, what is my… ⁓
vulnerability landscape, unless they know that, they won’t improve, they won’t fix that in the pipeline, right? There are all kinds of, so again, as long as it’s giving value to those folks, and it makes sense, I think anybody won’t mind having those compliance dashboards in front of them when they’re working. Value, 100%.
Raj Krishnamurthy (41:54)
think value is the underlying word here. I think you need to communicate
that. What do you see? I mean, you’ve been a veteran in this space, You’ve been there for many, years. What do you see is the current state of GRC tools?
Vivek Madan (42:09)
GRC tools, okay, yeah. I think.
I see a lot of consolidation happening. ⁓ They’re getting less complex also. I feel like some of the legacy products were very, very complex. You have to have dedicated resources who understands the backend and they understand the logics and workflows and how to build customization, all of that. So I think many tools now that are coming are sort of plug and play, which is nice. But at the same time, that may not work for a…
a big industry like us, right? So there’s that mix. The important part is, think GRC tool on its own is really, really important. Once you mature as an organization, I think it’s a must tool to have where you can have a nice place to keep your risk issues, document them, reporting becomes very visible to the board, to the people making decisions, right? And even from the governance piece, having a GRC tool,
if you have a massive set of policies, it’s sometimes hard to just find the policy that you’re working on. If you are an R &D team and you’re working on, let’s say, identity access management or designing some authentication methods, if the policy is not front of you, sometimes it’s hard to find even the policy requirement itself if you have 20 set of policies. So having a GRC tool kind of helps search faster ⁓ and become more accessible in the governance space. Similarly on risk, I already mentioned, and on compliance side also,
⁓ I think GRC tool is playing a fantastic role. I remember back in 2005, sorry, back in my first ISO 27001 in Belfast, it was all Excel based. I had no idea there was a GRC tool existed and I had maybe 20, 25 Excel sheets maintaining each set of data. And I don’t know how to go from that one framework to another framework without having a good GRC platform. just fast tracks everything is what I feel.
Plus, you know, it kind of shows maturity, responsibility within the company, you know, where people have access. Again, I think I’ll take maybe two, three examples. So vendor risk management, right? Many companies do it on Excel and, you know, give a checklist and get the response. But the problem is the initial filtration, especially for a company that have 15,000 people.
You want to your team or sorry, or your employees, if you have, know, don’t know, thousands of vendors, a platform where they can interact, let’s say with an onboarding form, which is very simple. And based on that form, you can automate, let’s say some of the vendor assessments, right? 90 % of assessments actually that we do, or we have, you know, are automated today. Okay. So the vendor onboarding form is capable enough.
and has logics that understands what data classification, where the services are being hosted, what regulatory impacts it could have, whether there’s personal data involved or not, and based on that, it can assess whether there’s AI involved. Based on those parameters, it can assess and say, it’s a low tier vendor, there’s less risk, and you can really prioritize where your focus should be. So GRC helps with that. Another example could be, let’s say you have a… ⁓
Trust Assurance page, where your customers, they’re asking so many questions, massive amount of questionnaire sometimes. And we have actually automated that ⁓ to the most extent also. We have connectivity with our backend tools where it can look for an active customer. And we have created a knowledge base where customers can come in, they can kind of self-serve themselves. Like if you go to Google Microsoft today,
massive companies, they’re not feeling any questionnaire, right? I mean, they are creating the self-serving trust centers where you can just go and download your SOC2 type to your ISO, or they have an AI bot that will tell you what the company does for a certain practice. That’s where it is going right now, right? So having a GRC platform enables that automation, access to records where you can’t really find them in Excel word, I would say, yeah.
Raj Krishnamurthy (46:27)
Makes sense, makes sense. And from a, in product security, I think we used to say software is eating the world, right? And cloud became, and it exponentially increased the surface area of applications and services. I think generative AI is just exploding it further, right? By magnitudes. ⁓ So what is the effect of large language models, large listening models, generative AI techniques, right? In product security,
And how does from a particularly in terms of how it impacts you and your GRC team, what is the effect of the product teams using GenAI and its effect on the GRC?
Vivek Madan (47:07)
I think massive impact, all the cybersecurity products today, they’re going in that direction, right? Imagine you had before, let’s say a SIM solution where you’re ingesting a lot of logs from different systems, you have your network firewalls, you have your ideas, IPS, you have your backend servers, databases, all kinds of different machines. ⁓ And there’s a lot of threat intel sort of coming from those in terms of events and logs and whatnot. So imagine just,
throwing all of this data in a large language model and have a very simple interface that you can communicate in natural language and say, where is my biggest risk today? What am I doing with certain assets? You can create those kind of effective methods to analyze data in a much faster way and very efficiently.
So in product security, it’s across the board. You pick up any OSI layer, they are adding certain large language model either to analyze data, either to analyze threads. ⁓ But as a GRC function also, ⁓ feel AI ⁓ hopefully will help with lot of automation. That’ll be the number one goal. ⁓ Imagine you did a risk assessment and you found ⁓ a bunch of risks.
⁓ hopefully, based on that data, an LLM can present what kind of risk it is. Maybe do some quantitative analysis. Maybe the fair can come, become hopefully, finally, can bring something beautiful from that word and say, you know what, this, can quantify based on this, what is happening in the market, based on the trend, based on these kinds of markets. We have seen this much impact and here you go, this much impact it could have. That’s how I quantify risk for you.
And then not just there, but also I can say, hey, choose a framework, tell me what controls should be tagging along to mitigate this risk. How do I meet now NIST 800.161 or 171 requirement and to mitigate this risk? that mapping, I think, it can recommend you controls ⁓ or even something as simple as, again, in GRC, like I was mentioning, you have a vast set of knowledge base, you have so many policies that people don’t want to read.
It could be as simple as, hey, I’m working in R &D department and I’m trying to build ABC application. What is my set of policies that apply to me? Or how do I find ⁓ how often the password should be rotated? It could be as simple as that, digging into those knowledge base and bringing the data out.
Raj Krishnamurthy (49:43)
It makes sense. think that’s a beautiful way to put it. We are almost approaching the end of the segment. Vivek and. ⁓
When you’re hiring into your team, into your GRC team right now.
How do you, what is the profile of, can you describe a little bit about the profile of the candidates that you’re trying to hire? What do you look for in them? And to somebody who’s listening this podcast, right? What should they be prepared with? And I’m not specifically trying to make this specific to your job or hiring. I’m asking this to you as a GRC leader.
Vivek Madan (50:23)
Sure, yeah, thank you. ⁓ In fact, we are hiring right now. ⁓ yeah. What we, ⁓ again, depending on at what level the person is joining, but if it has to be a GRC analyst job, I would say ⁓ somebody ⁓ with at least three, four good years or five years of experience ⁓ under their belt. And I think the most important thing is understanding
Raj Krishnamurthy (50:26)
Okay.
Vivek Madan (50:52)
know, ⁓ OSI layers, like do they really understand why controls are or why frameworks are built in a certain way, right? ⁓ If FDA came with that idea of regulation, it’s applying to all the restaurants and you want to hire somebody who understands why, ⁓ you know, hygiene is important. At least that basic principle should be there. So somebody with basic understanding of security.
⁓ They know why security is important, that why it has to be very strong. then, you know, and I always look for technical understanding of controls, not just that they have worked for five years as a vendor risk manager and all the checklist based audits. Do you really understand how controls operate and why they’re implemented in a certain way? If we’re requiring you to implement MFA, why it is important? What risk it is mitigating? You need to understand that.
Somebody could just say, hey, MFA should be implemented. Great. But why is is I think important part that I always look for. Also, I try to usually understand, you know, their perspective that if I give them, let’s say a completely new compliance framework, you know, you are, you’re based out in U S and there is SOC 2 type 2 and somewhere down the line, there’s a new completely new compliance regulation or framework, you know, announced.
Right? How would you go from that old compliance standard you had to now this new compliance framework? Right? Do you understand what it takes, you know, what all different things it takes to build a compliance, you know, sort of journey or a program, right? Again, controls are important. Your risks are important. Your threat landscape, you understand that you have to understand processes, how you interact with people, because it’s usually cross department function. You interact with lot of people and you want to make sure
in a very polite way, but at the same time, in a very responsible way, how do you ask for what you need, ⁓ you know, before you any audit or, you know, how do you communicate? I think all those values are important. Yeah.
Raj Krishnamurthy (53:02)
And somebody who’s listening to this says that I meet all that criteria and they want to reach you. How do they reach you?
Vivek Madan (53:08)
Yeah, just ping me on ⁓ LinkedIn or just go to Fortinet Career website and they can apply for this job, ⁓ IT and compliance analyst. Or yeah, just ping me, send me your resume, ⁓ hopefully on my LinkedIn and happy to take a look.
Raj Krishnamurthy (53:21)
With that, Vivek, this was a fantastic session. Thank you for joining us on the show. Thank you.
Vivek Madan (53:27)
Thank you,
Raj. The pleasure is all mine. think, yeah, you were great. And thank you for all the questions.
Listen on your favorite platform and stay updated with the latest insights, stories, and interviews.
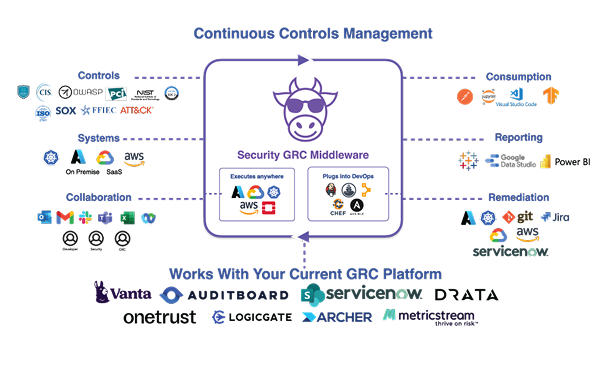
Want to see how we can help your team or project?
Book a Demo