Getting Started
Welcome. You can get started with ComplianceCow in few simple steps. No user manuals.
You can also signup using Slack or Teams or Skype. We totally recommend it. Try out for a super cool ComplianceCow experience.
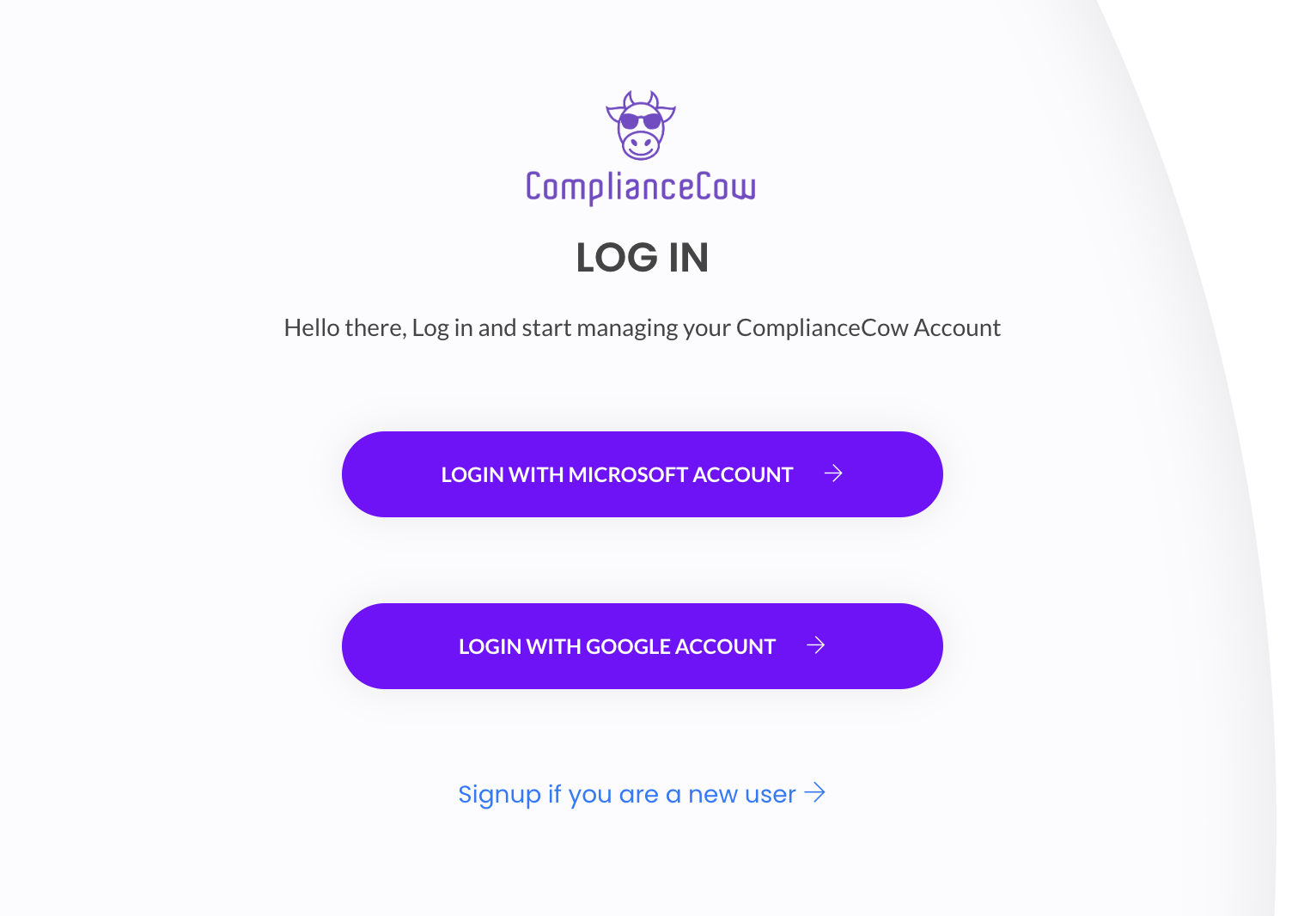
Step 1 – Signup with your Microsoft or Google credentials
To use the bot, simply click on the link for Microsoft Teams or Slack or Skype
Step 2 – Create your ComplainceCow Domain
ComplianceCow is a multitenant security grc platform. All transactions are isolated by customer domains. We will try to infer your domain from your email id. However, you can edit to create your own domain.
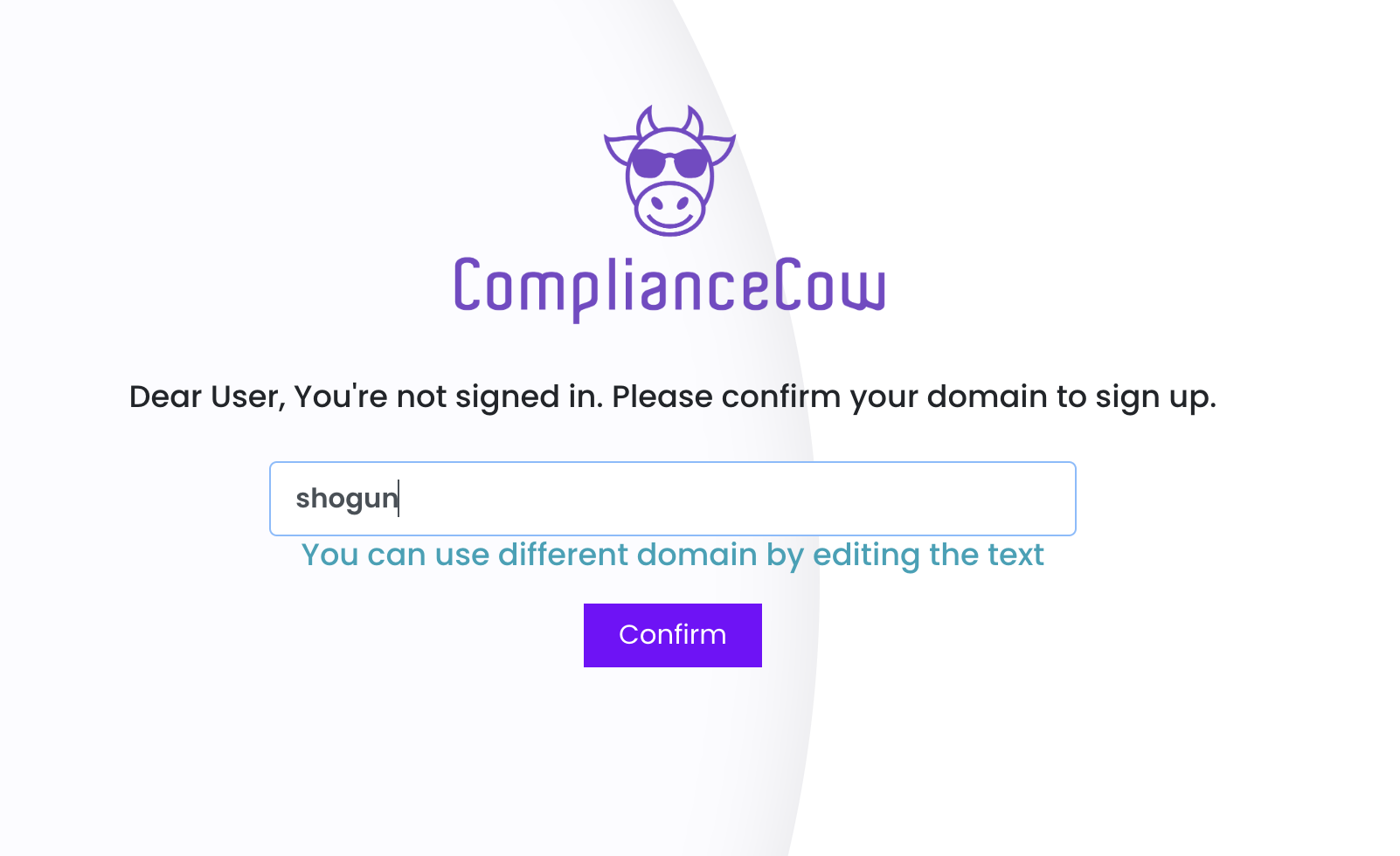
Check your inbox for confirmation email. Don’t forget to check your spam folder. Your user account and domain will be activated once you verify the email. If you are the first user, you are made the administrator, by default.
If your domain already exists, ComplianceCow will automatically notify current administrators of your request. One of the administrators will need to approve your signup request to activate your account.
If you have any questions, please contact ComplianceCow support.
Step 3 – Create your Security Assessment Frameworks
Create your assessment category. The Assessment Category is the grouping of assessment frameworks for easy management. Specify your assessment category and then upload your assessment framework.
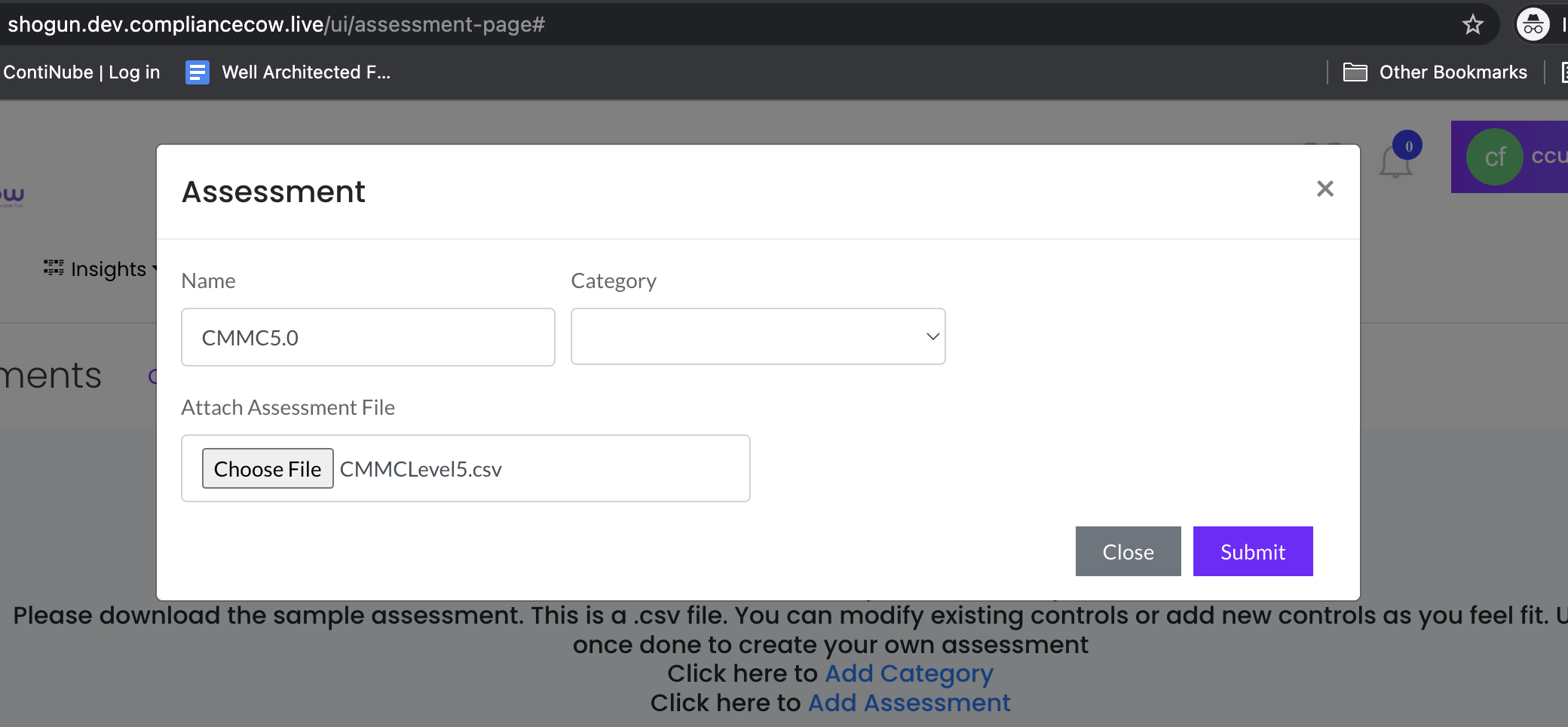
An Assessment Framework is a collection of controls or risk indicators. We provide you with a sample list of assessment frameworks that you can use out of the box. Make sure to scroll down to see these samples. When you click on any of the samples, such as PCI-DSS, you will download the .csv file. The file has the following structure:
- Control Id – The ID is a hierarchical notation. The numbering schema establishes the parent-child relationship for the controls. Each alphanumeric value before or after the ‘.’ specifies the parent or child relationship with the other. For example, control id 1.1 is the child of control id 1 and is the parent of control id 1.1.1
please note that there is a difference between 1.0 and 1 in the notation - Control Name
- Control Description
You can modify the .csv file; add, update or delete any of the records to create your own security assessment framework.
Steps 4 + – Just play around
Now that you have signed up and created your own assessment, feel free to play around. Explore how you can
- Configure your assessment for checklists, notes, attachments
- Upload your own evidences
Currently we only take csv files for evidences but that will change soon! - Assign controls, evidences to other team members
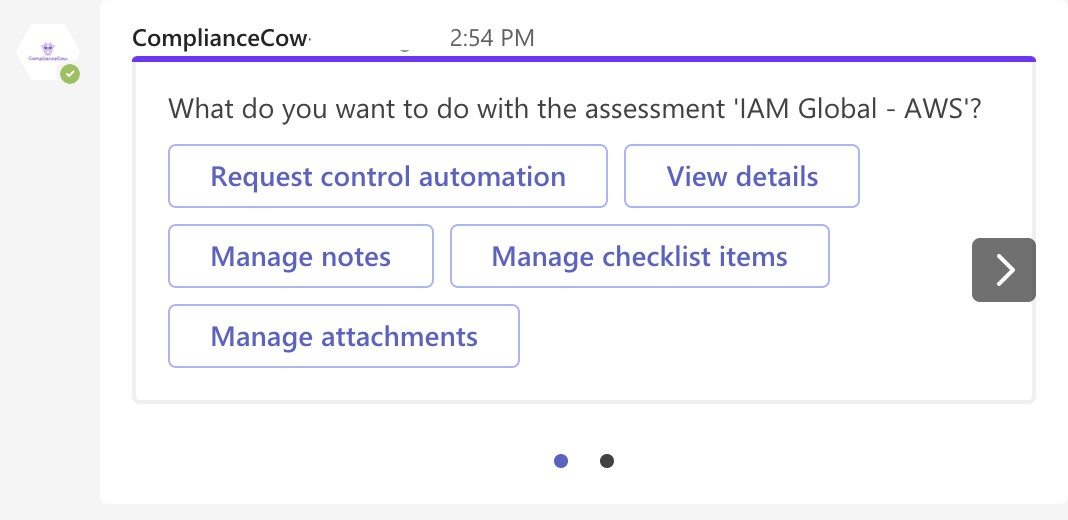
You can do all of this even easier and more productive through our Microsoft Teams or Slack or Skype bots. Give it a spin. You will love it!
A big part of what we do at ComplianceCow is automation of security controls. We have more than 500+ policy rules spanning Azure, AWS, GCP, Kubernetes and several SaaS applications such as Google workspace, Jira, ServiceNow, and other runtimes. These span several key frameworks such as CIS Benchmarks, PCI-DSS, NIST CSF and Well Architected Cloud and Kubernetes Frameworks.
Email us at info@compliancecow.com or call us at (650)996-2019 or just request for automation using the ComplianceCow bot.
Thanks much for trying ComplianceCow. We want to make security assurance meaningful and cool. Together, we will make a difference. And, don’t forget to give us your feedback