In this episode, Raj Krishnamurthy interviews Shobhit Mehta, Director of Security and Compliance at Headspace, to uncover valuable insights into the evolving world of Governance, Risk, and Compliance (GRC). Shobhit shares his controversial perspective on GRC teams overburdening themselves, emphasizing the need for GRC professionals to expand their technical expertise and embrace a product management mindset.
The conversation dives into proactive strategies for GRC success, the importance of integrating privacy into compliance frameworks, and actionable tips for achieving High Trust certification on a budget. Shobhit also reflects on how his endurance sports journey has shaped his approach to discipline and resilience in both his personal and professional life.
Tune in to learn how automation, innovation, and strategic thinking can transform your GRC efforts.
Key Takeaways:
✅ GRC teams often overburden themselves with audits.
✅ Embracing a product manager mindset helps GRC teams drive security initiatives.
✅ Technical knowledge empowers GRC professionals to enhance security programs.
✅ Changing perceptions of GRC within organizations is crucial for success.
✅ Proactive strategies can elevate GRC’s role and reputation.
✅ Integrating privacy into GRC frameworks strengthens compliance efforts.
✅ High Trust certification is achievable on a budget.
✅ Automation can significantly improve GRC efficiency and reduce redundancy.
✅ Overlapping audit timelines minimizes disruption and streamlines processes.
✅ Discipline from endurance sports fosters focus, resilience, and growth.
Listen now to gain actionable insights and elevate your GRC strategy.
🎙️ Security & GRC Decoded is brought to you by ComplianceCow.
Learn More About How ComplianceCow Can Help Your GRC Team Today!
🚀 Enjoying The Show?! 🚀
Make sure to rate and review the show to let us know you’re enjoying the content!
Subscribe now for expert insights from industry leaders shaping the future of security & compliance.
Learn More / Connect with Shobhit Mehta
If you enjoyed this conversation and want to dive deeper into Shobhit Mehta’s insights on GRC, cybersecurity, and building effective security programs, connect with him directly:
💼 LinkedIn: https://www.linkedin.com/in/shobhitmehta/
🌐 Company: https://www.headspace.com/
uh-huh Uh-huh [Music]
Welcome to security and GRC decoded I’m your host Raj Krishna Morti and we are here to decode with the awesome show Ma
today Shvid is a director in security and compliance at Headspace Headspace is a mental uh health and wellness company
in San Francisco He’s an accomplished u security and GRC professional author
blogger and an endurance analyst and maybe shave you should tell us if there is anything more that I’m missing He has
an extraordinary story His story is nothing short of inspirational and his journey into cyber security So welcome
to the show Thank you Raj for the amazing introduction I I don’t think I
could have done that better myself Thanks for that Yeah thank you So maybe I’ll start let’s start with
something with maybe let’s do the shock and awesome thing right what is one controversial opinion that you hold on
security or GRC I have been in the industry for 14 years Raj and I think I have seen companies of all sizes and
shapes I have been with companies with 5,000 people team all in information
security and when I joined my current company it was just me and our CES at the time and through all that experience
I realized that there is always this opportunity to streamline the work that we do and more often than not GRC teams
tend to overburden themselves just for the sake of running through audits throughout the year So I would I think
that’s something that I have seen through many different forums I advise a few companies via this venture capital
firm that I work with and every now and then they have to work on five different audits and they have different timelines
for each of them and then I ask them why and they don’t have an answer and I think that’s something that that I have
as a controversial opinion that GC teams tend to overburden themselves which they
should not and there is always opportunity to streamline which they they can always always do in whatever
they are doing I I I think that’s a very interesting point and I really want to come back and talk about what they can
do right and and sort of what is the basis on which you’re making some of those uh statements and how we can help
them Uh let me uh why don’t we start about you uh maybe let’s talk about what
has been your journey into cyber security and GRC I did my bachelor’s in 2011 in computer
science and throughout my undergrad I was doing coding I was creating websites
for some of the best companies in the world and I was partnering with many many companies on building this websites
and when I joined this company called HSBC my goal was to do development but
it so happened that in India when you get hired you don’t have a choice that what you want to do and for the first
four years of my life Raj I did information security and I had no idea what I was doing I was creating metrics
and dashboards and like I mentioned in the past we had a team of 5,000 people doing information security all over the
world for ACPC And to me at that point it made no sense that what I was doing and I was pleading my manager to go back
to coding I just wanted to learn Java and I wanted to do like create this web applications on a higher scale but that
didn’t happen and I I was I was lost for the first four years and then I switched
gears I went to financial risk management which is the broader umbrella of information security I did that for
two years and then I realized that I didn’t like that either So I went back to the drawing board and that time I had
a conversation with one of my mentors that hey I feel I’m lost I don’t like information security even though I did
that for four years I don’t like operational risk even though I did that for two years What’s next for me i have
my entire career and life in front of me and he gave me this advice that I think you should probably go back to the
drawing board and maybe what you want to do is to pursue masters in something that you would want to do for the next
uh 20 30 years of your life and at that time I already gave my GRE GMAT
everything that I had to give for this admission and uh just as luck would have
it one of my friend at the time was preparing for this MS and information security and I applied for the same with
very little hope that I would get in but fortunately I got in and I did my
masters in information assurance and cyber security at Northeastern and that
really really opened the horizon that I had in my mind for information security when I was working for ASBC I was only
preparing metrics and dashboards and even though I was looking at all these number of incidents that were being reported by archer and I was working on
access management and I was working on this different audits and I was working on this segregation of duties project I
did not understand the business rational for it Raj and that even though I was learning all of that I didn’t really
make sense of how that’s enabling the business so when I joined this program
the the mast’s program in Boston at at northeastern that opened my horizon and
for the first year I learned so much about all the different facets of information security that it’s not just
about access management of segregation of duties but there is like red teaming and blue teaming and purple teaming and
threat modeling and bug hunting and I was exploring all of that and after one year I had the opportunity to work with
PayPal and then I did my summer internship went back to college throughout the second year I worked with
Fidelity Investments on one of their startups where I had the opportunity to build the entire security program from
scratch and I think that was my initiation into information security and that’s where I really learned how it
what it meant to build the entire security program from a scratch So that’s that’s like my
journey and I’m sure we have talked about this for such a long time in multiple forums that Hadspace has been
an amazing amazing place to build this program from scratch When I joined I had an amazing amazing mentor He is still a
dear friend and he taught me all these different uh aspects of security right from GRC to application security
infrastructure security privacy engineering you name it and I think I did pretty much all of that in my
current role so no that’s a fascinating journey engineer to maybe an operator of
some sort but he went into operational risk management financial risk management and then he just dived into
the different aspects of security and you know um security engineering security operations That’s a fascinating
story What is your view of security and GRC and the intersection i truly believe
that GRC is the product manager for the information security team and I’ll explain that why Um let’s let’s take
this in a broader company perspective product team they decide what features they want to build and then they decide
that okay this engineers are going to work on this particular project or features and they are like driving the
engineering team in some sense similarly if you look at it for the information security team GRC is doing audits all
the time they have this ability to go and speak to all these different individuals in the engineering team in
the product team in the legal team privacy team and figure out what’s going on across the company and they are the
ones who are interfacing with the auditor tors as well So I truly believe that GRC has this this immense
superpower that they can go to anybody ask them hey can you speak about this particular process for 15 minutes how
are we doing our socks audits or how are we doing our uh user access reviews for this financial application and so on so
forth and I I think GRC is like the product manager now they have been
through all these different functions they have spoken about all these different processes to this individuals
and they have a very good understanding on where we are doing good and where we are doing bad and I think it’s it’s on
the GRC team to figure out because of course they have limited capacity and bandwidth it’s on them to figure out
okay this is the project that I want to work on or focus on for the next year and I’ll give you an example let’s say
security awareness training if people are not doing security awareness training the GRC team has a view of that
that hey our employees are not doing their awareness trainings on time and we should be focusing on that a little bit
more They can make that as a project to kind of go and have reach out to this
individuals and say hey can you do this this trainings Similarly they are also managing all the vulnerabilities because
they run the vulnerability management program And if they see that engineers are not doing their job properly on
fixing that code or high critical vulnerabilities then they will be the product manager and they can reach out
to them saying hey I want to make sure that you are fixing this vulnerabilities in a timely manner So uh that’s my view
of information security and GRC Of course GRC has a superpower to reach out to all these different team and ask as
many questions as they can without worrying about the consequences of that happening later Got it So you’re saying
GRC has a holistic view into all things security all things application
engineering and and by by superpower they are able to look at this much more broadly and are able to act on it
Correct Okay Now that what do you think should be the how technical should these
the GRC team be what’s your opinion of that i always tell my team that your
engineers will love you a lot more if you go to them and tell them hey we need
the let’s say if there’s an audit request and the audit says you need the screenshot of firewall and you go back
to your engineering team and ask them that can you give me that screenshot I think your engineers will love you a lot more if you tell them that I need this
kind of security groups and they don’t need to worry about what the f that we’re talking about Similarly if you
know about GitHub branch protection and you can go and ask engineers exactly what you asked for that will be truly
amazing rather than you letting them know that hey we need some screenshot for branch protection and whatn not And
this is something that I I favor a lot that folks in GRC have to go beyond GRC
to flourish in their career And I take my own example for the first let’s say seven eight years of my career I only
did GRC I only knew GRC and that would have restricted me so much if I had done
only GRC only focused on audits It’s good to know five different frameworks but that has to stop somewhere They’re
like the requirements are pretty much the same except a few and uh it’s it’s on the individual to make sure that
they’re taking a holistic view of their career and going beyond GRC Raj I’m a huge proponent of continuous learning
and uh encourage everybody in GRC to look beyond what they are doing at the moment
and look beyond audits uh and make sure that they are learning about uh
GRC about different facets of security and not just focusing on GRC No I think
I I I love it So what you’re basically saying is not only does it make us the
the GRC professionals more productive it also helps to build the social capital within the company for them to go get
their job done right because you’re respected more you’re trusted more uh and maybe you can go faster um farther
You are absolutely right that that should be the goal for every GRC professional that how can I go beyond
the realm of GRC which I’m really comfortable with and even if they are doing 10 different audits the
requirements are going to be the same but it’s on them to push their career and learn about application security
infra privacy and so forth though so they can be a holistic GC professional
or security professional at the same time like you mentioned build some social capital and you speak the language of business or engineering when
need be no that’s beautiful now how Do you think others perceive GRC how do the
leaders perceive GRC how do the security teams perceive GRC how does the rest of the organization perceive GRC what is
your what is your take i’ll start with my own opinion When I started with GRC I
thought it’s just audits that GRC is equal to audits And I think that’s a perception that leaders have as well
When we go to this leaders and we say okay GRC I think there are few things that come to mind Okay do we have
software certification and do we have uh software testation and do we have the customer are we completing the customer
questionnaires on time or are we doing the vendor assessments on time and so forth But GRC really has this power to
reach out and ask engineers this questions where they are being a lot
more thoughtful and go beyond GRC and I I’ll give you an example as well I don’t think any audit as of yet asks for the
um secure SST or DST or software composition analysis or those type of
controls I don’t think any audit speaks about do you have a bug bounty program I
don’t think any audit talks about threat modeling that do you have a formal process for threat modeling I don’t
think any audit talks about your relationship with the wider forum and do you have a security insider program or
something like that in your organization and we have to change that perception
that we do audits that’s our bread and butter as GRC professionals but at the same time there is so much we could do
in terms of uh going beyond GRC and learning about threat modeling and doing
that learning about text reviews and doing that learning about product feature requirements that are coming up
and partnering with legal and privacy teams and I think we we need to change that perspective for the business as
well that when they look at GRC it’s not just about audits it’s much much more than that even though audit is the bread
and butter that we have to work on and we have to pass those audits to make sure that we are building trust with our customers and making sure that we are
having all this revenue streams open we are not being a blocker for the sales team we have to go beyond that and
change that perception that GRC is not just audits There’s a world beyond that
that we need to work on Yeah Now I think that’s a brilliant point So you’re saying GRC is just beyond an annual
audit ritual right checking the boxes once a year it doesn’t cut it Um and I
think you talked about some of the things that you can go do to change the perception but especially with the leadership team and the security teams
how do GRC prof are there other things GRC professionals can do to change those perceptions
there are few things we we have done in in my current talk that that I think any any GC team could do The first thing is
the security awareness training revamp and I’m pretty sure that all of us we have to do some sort of security
awareness training in our organizations and more often than not like you mentioned there are checkbox activities
Raj people don’t really pay attention those security awareness trainings they think this is an annual activity and
it’s there for everybody to do in that learning management system that you created but I wrote about this that each
organization is so different Raj for example when I was at PayPal the security awareness training at PayPal was exactly the same as Fidelity and
that made no sense because the business is so different Same is the case with HSBC that the training at HSBC was
exactly the same as Douche Bank but that made no sense If I ask or if I talk about the current org the security
awareness training at headsp space would be completely different for the security awareness training that compliance cow
and those are some of the things you could do proactively that okay we have to do security awareness training how
can we make it more effective how can we be more proactive in making sure that employees know what they are and they
aren’t supposed to do and not play the blame game later that hey you did this and that shouldn’t be the case for
example let’s Say if a company they don’t allow sharing PHI on Slack it’s very individual to that company and some
companies may allow it some companies may not allow it but the employees if I’m a new joiner I would know until
unless you tell me and the first thing that you need to do is to complete the security event training to learn what is allowed and what is not allowed So
things like that we could we could always always do to make sure that we are building that that repo that we are
doing a lot more with the entire company and we are of course the the leaders of
the company do that training as well and they can see that we are being more proactive I see Uh there is one more thing which is very close to my heart
that we started this uh process at uh at headsp space where we do product risk
reviews before a single line of code is written And what it truly means is we
started this project where not just a GRC team or the engineering team We have folks from the legal team the privacy
team the compliance team the application security team and infrastructure team Review all the PRDs review all the major
text specs that are being created and provide feedback even before a single line of code is written uh that uh I
haven’t seen that happen in the previous orgs that I work with but that is something that GC team could do and that
will help reduce the risk of having those those bugs or issues at a later
end when the code is returned when the features are developed and all of those you’re not just shifting security left
you’re shifting security privacy legal compliance care everything to the left which is the ideal secure threat
modeling in my my uh view No I think that’s a brilliant point So the way you answered this question is that you’re
saying how do we change perception of the leadership team and what I’m hearing you say is that the best way to do is
start doing things right do things that can be more proactive start doing things
that show up right where people notice a very palpable change right and that gets
you better uh correct is okay no that is that is a fantastic how do you you talked about privacy how do you see and
I know you’re a privacy practitioner as well how do you see privacy fitting into this security and GRC I think the realm
of GRC is over It has to be GRC and privacy Raj some organizations have this
luxury of having a separate privacy team and a privacy engineering team per se and some organizations are not that big
that they have a separate privacy team all together and again go back to the previous point that GC teams need to go
beyond what they’re doing day in day out and they have to be much more proactive and one of the the the ideal streams
from there is having privacy in the bucket of GRC So I would say for a
smaller company GRC and privacy go hand in hand they go in parallel and in my
view the privacy team or the privacy engineering team which I manage is like
the business analyst for the engineering team and I would phrase it in such a way
that let’s say if there’s a requirement from GDPR and CCPA that we have to delete the accounts in a certain fashion
the engineers don’t need to know all the privacy language at the same time privacy team may or may not speak the
language of engineering but GR RC team has this luxury of knowing all the engineering systems that are in used all
the data pipelines and systems where we store PIP PHI and at the same time they
can speak the language of privacy given their knowledge in that realm and they can translate those requirements from
the privacy team in a much more effective fashion for the engineering team So that would be my approach of
looking at privacy There are always so many things that are coming up from many
many different avenues App the Apple app
store they had a requirement couple of years back that all the applications which are allowing users to create their
account from the application should allow the users to delete account from the application as well Now who is uh
the primary team to drive that conversation i don’t know So it obviously falls onto GRC and we should
be driving that conversation Uh there’s this requirement from Google that all the data that we are collecting from the
application should be in the should be filled for Google Play Store And again who is responsible for facilitating that
converation if the GRC doesn’t do that I don’t know uh and there are always like
this this different changes or regulations coming up in HIPPA and GDPR and CCPA and I think it’s on the the
onus of making sure that all of things are being done is on the privacy engineering teams
okay that makes sense you are an expert on high trust um
and I actually have listened to your speech on high trust and besides SF I believe you gave it last year or the
year before I’m I’m not that was in 21 Raj I think that was the first time we met Yeah Yeah Yeah Yeah Yeah That was a
brilliant presentation and maybe we’ll put a link to that presentation um in the podcast as well So what was it like
to get Hyra certified what challenges did you face what would your advice be for anybody who’s aspiring to get Hyra
certified either either because they want to get Hyra certified like you are in the health business or because they
want to anchor use Hitrust as a harmonized framework right across multiple other frameworks What would
your advice be so I’ll answer your question in two parts First what the what’s the effort
that it took to achieve high trust and what it meant for us as a company and then secondly if you’re starting your
security program from the scratch should you look at high trust from the very beginning I’ll take the first question
first that it when we started this journey Raj I was at that time a manager
I used to ask him hey what’s our next goal this company is asking us for software audit and attestation report uh
we wanted to do high trust but do you think we’re ready for it and at that time I had no idea about high trust in
2020 I never heard of it and at one point of time we just decided that we are going to pursue high trust and
achieve that and there were some contractual requirements which required us to achieve high trust within that
year in 2020 when I joined the company and I I at that time we were only three
people in the entire team one person was doing it we Me and my manager at the time we were doing security And when we
looked at high trust there were like 350 odd requirements in 19 different domains
ranging from privacy to policies and procedures to mobile device management to portable devices and how you’re
managing those to your application security just name it And they had a requirement for that And I think that
was the most transformational part of my entire career I learned so much I did
the entire gap assessment what we have what we don’t have wrote all those policies with autoative sources and and
so forth and that that actually when I was speaking to peers in the industry
they were like it’s going to take at least half a million dollars for you to achieve high trust and you’re going to
take at least two years to complete it but with the amount of work that we did we were able to complete that within
100k including the cost of the audit by using a lot of open-source uh tools and
by using doing a lot of documentation early on and so forth and we completed the audit within 9 months So I I was I
was talking to the auditors and they were mentioning that hey you should be presenting it somewhere because the work
or the amount of work you did is not just hard work it’s a lot of smart work as well and people ought to know that
there high trust is I it’s it’s not a sprint is not a marathon it’s an
ultramarathon but you could do that if you persevere and be smart in your training so that was the the the idea
behind behind and presenting that in the conference and it was surreal I mean we
we unlocked so many deals we had to complete so many lesser questionnaires because of that because we had the
certification and everybody was able to uh accept the highest certification and
the second part of your question is if I’m a company which is starting their
compliance journey should I start with highest altogether and I would say I will probably do something different uh
if I have to go back in time I would probably start with sock 2 plus highrust because sock 2 has this flexibility
where they allow you to inherit the controls of high trust but not have the high trust certification which is which
is kind of odd some companies have the requirement that you need to have certification but there are other organizations which are okay if you do
sock two plus high trust or you have a sock to a test station from the auditor so I would rather advise companies to go
from there if they don’t have the the budget or if they don’t have the the manual capacity to do those audits
that’s another mechanism where they can start if they want to have high trust in their compl science uh repository but
not do the full Hydra certification and and is it because to do the full Hyra certification it’s going to cost you
more in terms of audit effort uh why
would you say that highest alliance so there are three things that that come into picture when
you talk about hyrarch first is you have to have your my CSF instance from
hyr amount they have different versions of my CS yeah tiers for my CSF but it’s
going to cost you at least 15 to 17k then even if you take the bare minimum high trust certification requirements
it’s going to be security controls plus HIPPA because the entire purpose of hyras is to show your companies or you
show your customers that you are complying with HIPPA requirements if you do that that’s going to be around around 300 plus controls in your highest and
the auditor will cost you based on on the number of uh or the scope of your
your certification So it’s going to be at least 60 70k at at the bare minimum
to have the the audit fee And then of course you will have to have a lot of tools in place if you want to do that
For example you need a mobile device management tool You have to have uh an ADR You have to have um something that
can block the the portable devices and uh USBs you have to do a lot of work on
privacy and you have to create all those policies So if you don’t have that background of creating policies and
having authoritative sources it’s you are going to hire a consultant It’s going to cost you So I would rather say
that if you are starting your compliance journey and you have the budget and you have the contractual agreement then go
with it But if not then probably uh there are better avenues to do that Okay
And I I remember I think if I remember right your your title was aptly I mean your presentation was aptly titled
achieve high risk on a budget isn’t that correct am I right yeah Yeah achieving on a budget and I think my first slide
was that we achieved higher certification under 100K and 9 months
and you may not believe that but I still receive emails from people and people reach out on LinkedIn asking for the
templates or asking for some guidance on because they are studying on their height journey and they want to learn
about all the opensource tools that we used rather than buying a tool that only
serves the purpose of audit It just doesn’t make sense I know you’re a blogger Is there a blog that talks about
what opensource tools you use to achieve high trust on a budget i think the B
sites team they posted the link of the entire uh talk and within that talk I think there there is a link to slides as
well and in the appendex I do have list of all the open source tools that we use uh for example we used defect dojo for
vulnerability management rather than buying some shiny tool at the time because we didn’t have the budget for that and we used many
different MacBook settings to achieve some of the requirements rather than buying uh a different tool which will do
pretty much the same thing So I I think I do have a list of appendix in the in the slides as well and if your audience
is interested they can always reach out to me on LinkedIn or just uh send me a note and I’ll be happy to help them with
the uh repository All right thank you I know that’s helpful Uh let me you
talked about um GRC going beyond audits Maybe I want to double click on that I
think you talked briefly about threat modeling security awareness training PR
reviews was a very interesting point that you made Anything that you want to add or add more color to that how do we
go how do we do GRC beyond just thinking about audits there is always this
opportunity to have continuous engagement with the wider team and I
think that’s something that GS teams focus on just building that culture of security and I’ll give you an example
the headsp space we have this program called security insider program and what essentially means that rather than
having us doing all the work for security for all these different teams we have this individuals from different
teams who are the volunteers and in some sense the extension of the security team and they are like your first point of
contact for anything that you need related to security So consider this You
join a new company or you join Headspace You have no idea about what you are or aren’t supposed to do Rather than
reaching out to the security team or sending a note to IT help what you can do is to you can reach out to the the
security insiders in your own company who are working with you day in day out and they should be able to guide you a
lot better and faster than getting a response from the security team That’s something that I think could be could be
done just to build that culture of security The other thing that I would highly highly emphasize all the the the
audience members that are listening to this is figure out do you really need to have so many different audit timelines
for each of those audits Sometimes it’s a compliance requirement sometimes it’s a regulator requirement or sometimes
it’s a customer requirement Then you have to have all the statisticians active all the time But you always you
can always always play with the with the timelines and and make sure that they overlap as much as they can So you are
not doing one audit in Q1 then going back to the engineering team doing another audit in Q2 and then going back
to the engineering team and asking for evidences in Q3 which are all going to be different Let’s overlap all of them
And there is always this opportunity if you work with your auditors and treat them your friends and let them know that
this is the the final output that you want to have They will help you achieve
those objectives So I think that that’s something that I would want um all your
audience members to think about that how they can they can overlap all those different audit timelines and and make
sure that they are not uh doing audits throughout the year Got it So do you
plan on an audit calendar early at the beginning of the year beginning of the fiscal year is that how you approach
this yeah Yeah we we do the same thing And uh sometimes you may have to have a bridge letter or sometimes you have a
shorter duration software report which is all all feasible You just have to be very open with your auditor that this is
the goal that you’re setting for yourself and you want to make sure that they overlap as much as they can So when
you create your audit calendar make sure that if you’re receiving some population from a
different uh team That population can be used not just for one sock to audit or
ISO audit They can be used for sock 2 plus ISO plus highrust plus cyber
essentials whatever audits you’re doing and it should it should be work really well Yeah Okay Um high trust also has
mapping as a harmonized framework has mapping for ISO has mappings for uh NIST
853 PCIDSS uh 3.2.14.0 Right right now
do you use highress as a common framework to accomplish or do you have to do separate work for each of these
attestations or certifications you can do either uh you can take high
trust and you can have all those authoritative sources in the scope of the audit but that’s going to increase a
lot in terms of cost for the entire certification And I think if you are
trying to do high trust it’s okay to have one or two authoritative sources But some companies for example if you
are doing a PCI audit some companies may want to see your attestation and they want to see your final certification
that you receive from the auditor and not rely on the high trust if you even if you have PCI as the alternative
source So it depends on company what they are trying to do and what are the customer requirements Um for example
HIPPA if you have HIPPA as the authoritative source in hydrris then you don’t need to do do a different HIPPA
certification you can just use the hydrust and leverage that but if you are using PCI or if you have to comply with
PCI then it might be better to have a separate certification altogether rather than trying to include that in high
trust Okay got it You talked about um a culture of security How do you see
automation fitting into this culture of security
it’s the most important thing that any JC team should be thinking about that
how do they they automate the amount of effort that they’re putting in into
um making sure that they’re not doing redundant work and again I’ll go back to this point and I have seen companies Raj
from my experience they are still using Google Drive to store all the evidences
and what they say this is like the real world scenario I’m advising one company at the moment and what they’re doing is
they have all this evidences for PCI ISO sock 2 in different G drive folders and
those folders are in the range of thousands and the engineering team every time they have to reach out to an
engineering team and ask for the evidences they ask so what did we provide last time and there is no way
that the engineering team should be thinking what we provided the auditor last time and think from the beginning
that okay this is the certificate or the evidence that I need to provide this time It’s so easy to have all of those
in a Jira or a spreadsheet or some some sort of project management tool where
the instant team can go and leverage the same audits Now with the automation
tools that becomes a lot more easier for two aspects First you can have cross
mapping with different compliance frameworks Rather than having three different certifications or uh
requirements for three different certifications you have just one requirement which is labeled for three audits and you produce just one evidence
for for that And secondly if you are using the tool diligently such as
compliance score or other tools in the industry it just helps to collect all those evidences automatically after you
integrate them and you can free up all your time to do the other stuff that you want to do as part of the GRC team So I
I think it’s essential for any company to think about all those automations that they can bring to the table uh
there are many companies right now I mean JNA of course we talked about this in a separate uh channel that uh there
are AI agents now which are bringing the the the evidences for you and you don’t
need to do anything there are a agents now who are fixing the gaps that you have and you don’t need to do anything
there are YC companies which are building their entire models on this this mechanism that you just give us the
instance access our AI agent will figure out and they will find the gap with the sock tools requirements and your
instances and they will fix it for you So I think all this this this different
automations and generative AI agents they enable the GRC teams to be a lot
more productive than they currently are and then focus on other stuff like building the culture of security working
closely with the engine and product teams and so forth Got no I I think that makes absolute
sense Um and how do you see um you talked about
early on that the GRC teams are getting overwhelmed and some of this is brought upon by themselves That was the point
that you made in your controversial statement I want to bring that back here So in some ways I’m interpreting that to
say that we can do a lot more than what we are doing right now Is that a fair statement to make absolutely Yes Yeah
And in some ways so how do you how do you um so in some ways you are creating a constraint and how do these
constraints maybe you can talk about a little bit how what sort of constraints would you create in your world to go
back to your controversial statement and how do you think that promotes innovation well if you have the GC road map and in
that road map you have just the four audits that you want to work on then
it’s going to be pretty easy for you to just focus on those four audits but if you have limited bandwidth which is the
constraint in this case limited budget but you want to do a lot more and explore different objectives then that
will create a lot more and this comes to this principle that the amount of effort
can be managed with the amount of time that you’re dedicating to a particular thing to do if I dedicate something to
be done in two weeks I’ll do that in two weeks if I’m dedicating same project two
days I’ll do that in two days and it’s the same thing if I have a team of four people who are doing only audits they
will do only audits But at the same time if I have this huge list of things that
I want to do and accomplish which are not just audits they would do all of that and we would do all of that So
that’s the the the constraint part that I would talk about and maybe think about the growth as a
professional as well um and not just focus on doing audits for for the
company Got it I think that reinforces the other point that you were talking about about
the culture of security right and automation So your point is that if we automate more and take care of the
mundane redundant stuff that allows you to focus on a lot more other things effectively right and think beyond just
audits I think that’s the core part of what you’re and you can do more with less which is obviously understandable
through automation but your point is that that has to be that pushes the perspective and perceptions on GRC and
that establishes and creates a better security posture for company as a whole
That’s correct Yeah I think you phrased it better than me This is all you’re saying This is all
you’re saying This is like you do automation you free up time and then you have all this available time to do
amazing other stuff that you could and uh enhance your skill set and grow as a
professional So I think you summarized it better than me Yep No this is that is
fantastic Um um let’s talk about I want to come back to your personal journey
because I think you wrote this um I think several weeks ago and if I remember right I read on your LinkedIn
you said you couldn’t speak one full sentence in English until you were age 20 I’m not going to ask you how old you
are right that’s not going to uh but but it is very fascinating and I really
really want to maybe can you double click on that I want to know about show and I want this to be an inspirational
talk right especially to those people who don’t have access right and they are not in the Silicon Valley they are not
in the New York city right and they may be somewhere in India they may be some other in sort of in a suburban or rural
place in the Americas right so the question is that how can what obstacles have you overcome and how what advice
would you give the young people listening out there I I’ll share a brief background about
why I wrote that post in the first place because I was looking at my own journey and many many people rather after I
wrote the book they reach out to me and they ask for my advice and I I was just thinking it through that it just started
the year I had an amazing 2024 but if I go back 20 years back uh I was uh born
in a middle-ass family my parents they didn’t have the education that they
desired but they focused on my education but I went to Hindi middle school and I people who are from India they could
relate that when you go to Hindi med school everything that you learn about is in Hindi and that was my mother
tongue And even in college I went to a tier n college in uh in Dor Uh and I
even in college we were not speaking in English It was just like we were speaking in Hindi And until I entered
the workforce uh in 20 uh 2011 when I was 20 years old I could not speak like
a full sentence in English and have a conversation in English like I’m having with you at the moment even though I
could like learn and understand and do all of that That was really hard for me
because my base was in Hindi and that actually gave me a lot of uh I put a lot
of restrictions on myself that I couldn’t speak to some of the people who were coming from like on-site people who
were coming to India and meet our team and I this is something that I developed
over a period of time and I I learned that if I put in the hard work and do the hard work then I can achieve
anything I want and I always People reach out to me and they tell me you are an inspiration I the way I say it is
inspiration is don’t look at me as your inspiration If I do something wrong tomorrow would I still be your
inspiration no Don’t look at me as the motivation or the motivational speaker
I’m not that either because if I don’t do something tomorrow would you stop stop quitting that as well no I think it
all comes back to discipline And I truly believe that my journey started in 2017
after I moved to the US And at that time I had no other option but to speak in English And I just I think that was the
most monumental moment in my career when I moved here And uh I was given all
these opportunities and I think that that changed me as a person not just in
a professional setting but also the personal individual that I was And in 2020 when I joined this company
headspace ginger we were like three people in the team and all the gyms
closed because of co and I started running in at embarcado in San Francisco
and uh that time I was I I had no idea that I’m going to do ultramarathons in
the future but I loved it so much and I got so disciplined that I started doing ultramarathons and so forth So it’s just
that you have to build that discipline and everything will fall in place That’s
the message that I wanted to give that no matter where you are in your life at this point of time you will be able to
achieve a lot more if you just be persistent and discipline in whatever you want to do That was the message I
wanted to leave with the readers after that post Yeah No that’s an amazing
story Um Now coming back to you’re an
endurance athlete and you talked about it I think that discipline I don’t know how you do this
but maybe what made you take up um ultramarathon and uh and particularly
how has it helped you with in your professional journey so like I mentioned when I was growing
up I didn’t do a lot of athletics I was perhaps the most dull boy in our school
at the time and I didn’t run and I didn’t do any athletics I didn’t play
sports and I tell this to to everybody now who reaches out that uh every body
part in my every part in my body is very fresh because I didn’t use them when I was younger So like like I said when I
was in in 2020 when everything closed down I started running on Embarko and I
just loved it so much that I did the San Francisco marathon and I was looking at all these different folks who were doing
ultramarathons at the time and I got into the running scene in San Francisco So I created this this small club within
the community and we started preparing for the shorter runs and uh we used to do this trail running and right across
my my apartment we had an amazing amazing trail It’s called Mount Sutra in San Francisco And I used to go there and
run And I discovered there are places where you could run on trails for hours
and hours and miles and miles And they had like ultra runs on trails and that
got me hooked as well It’s for the first time I felt the runner’s high and I’ve
been persistent with that The current format that I follow is for the first three quarters of my year I work really
really hard on everything that I want to do The next quarter I just relax I just
plan for the next year Look at my my calendar what I want to do in the next
year That that’s how I structure my life For first three quarters it’s all about
the professional personal setting as much as I can And then the last quarter is all with the the the family and
spending time with them as much as I can Yeah Oh that is very nice That’s very nice Um show I I think no podcast is
complete nowadays without talking about generative AI So what do you see as the
implication of generative AI and large language models and security and GRC
the way I think about Gen AI and security I divide that into three different buckets Uh first is the
security for Gen AI you are developing all these large image models and you
have to secure them from poisoning and from output validation and so on so forth That’s the the first piece that
how do we secure gen AI as a whole The second bucket is gen AI for security
that we are creating this amazing amazing technology How do we use that for security the example of that would
be creating the sock analysts We are seeing a lot of companies right now which are claiming that they be your
level one level two sock analyst And there are some companies which are currently doing threat modeling and they
will be like okay you don’t need to do anything You just give us your PD and text break and we will do the threat
modeling for you So that’s the second aspect of it And the third one is the security for gen AI threats And the way
I think about that is what would be the threats that could be presented with the amazing technology that we are building
Uh for example the defakes It’s so hard at the moment to figure out which of the
videos are real which of the videos are deep fakes Uh the second aspect of that would be fishing email the fishing the
the quality of fishing email has changed tremendously over the last year and I’m
speaking to all this email security vendors and they are still trying to figure out a common or good path to
prevent the companies from that so that’s how I think about security for
genai security from genai and then how we can use that for preventing threats
that are being generated from this this technology there are many things that are happening Right now I’m currently
contributing to this white paper with OASP Uh it’s for the AI agents So the
way it works is OASP already has the top 10 for LLM that if you’re building a top
10 or you’re building a technology which uses LLM then you should be considering all these different risks that OAS has
already highlighted The subsequent part to that is now you want to build an agent on top of that
LLM and how do you prevent that LLM agent to or not be malicious So that’s
something that we’re working on I think the the most common theme that comes across when I speak to different peers
is how we are doing the authentication and authorization of those AI agents
Let’s say in the near future you have an AI agent I have an AI agent and how they would be working together to fix the uh
to to not interfere in each other’s authorization Uh the second aspect of
that would be a privilege What can they do when they think about the AI agents
and if they do decide to let’s say go beyond their realm do we have a quilt switch for those kind of AI agents and
so forth so that’s still under consideration your audience can always reach out and
I’ll be more than happy to let loot them in the working group Uh there are many many industry peers and experts who are
working in on this OAS top 10 for AI agents which is still in uh in private
beta Yeah No makes sense It makes sense Now I think one of the challenges that I see is that traditionally cyber
security has been a very deterministic principle right i mean you it is evidence-based
analysis You you want to very specifically know which users have MFA enabled which users don’t have MFA
enabled right which systems have logging enabled logging and monitoring enabled which systems don’t But generative AI
typically has been a very probabilistic model It is right large models are inherently probabilistic So how do you
sort of so there is a myth and the reality of genai and what it can do and
I think the there is a it is the maturity is significantly improving but how do you see the balance between the
myth and reality what is myth and what is reality is there anything that you want to talk about
it’s very very easy to build an application on based on genai raj for a
team of five people or five individuals but it’s very very hard to scale those
applications And that’s something that people don’t often understand that it’s easy to create a wrapper on open AAI charge
model and you will be able to create an application that’s like when you read post on LinkedIn that I just created an
application for $30 that’s what they are doing create an application for themselves but it’s really hard to build
on those applications and make it usable and accessible and scalable for companies or enterprises with thousands
of employees of users That’s the distinction that that I want to make that that the myth versus the reality
It’s easy but it still needs a lot of inputs and guardrails Um one example
would be if you’re creating an application which is only for a few people you may not pay a lot of attention to guardrails which is the
foundation for security But if you’re creating an application which is let’s say a mental health coach per se you
have to put guard rails because there are millions of users who will be using your application in the near future And
if you don’t put the guardrails from the very beginning it’s going to be very hard for the genai to work properly and
it will be giving out malicious output and whatnot So that’s the distinction
that I want to make that it’s easy to make an application on gen AI for a
small scale or for a personal project but the scale of doing that for millions
of users is very different We are reaching almost at the end of our podcast Um
show you are an author and are there any podcast audio books books you read
listen to and you know please feel free to give a shout out to your books as well Anything that you want our
listeners to know i see a lot of security blogs uh right now and some of them are very
superficial but I really really love the blog by Bruce Schneider That’s like my
go-to blog I always he is one of the best individuals in security He invented
the brypt algorithm I had a chance to meet him once when I was in uh Boston and he came to our college to give a
lecture and um I think uh that’s the blog that I would recommend all security
professionals to to read Uh it’s it’s very foundational It speaks a lot about
different facets of security It’s called Schneider on security uh podcast I’m not
a huge fan of podcast and the this is again one philosophy that I have that the source of knowledge is books is
greater than blogs is greater than audio books is greater than uh the podcast the
podcasts are there at the very end I think it’s more of a uh tail end of my source of knowledge
but I would highly recommend this one book it’s called security architecture
in engineering I think uh by one of the British authors I forgot the name but that book really helped me a lot in
learning a lot about security engineering and what it really means Those two two resources I would highly
recommend to to the audience Yeah And hopefully this podcast changes your perspective on the picking order podcast
being the last I I did listen to the previous four podcast Raj and there was
so much knowledge from different folks There was Abhai and other people you had
on the podcast I listened to those and that really really got me hooked on how different companies are doing security
in GRC engineering at scale I think that was a very very nicely listen Yeah No
thank you Thank you Appreciate it Chid thank you very much and it was a
fascinating conversation and I uh no matter what you said you will continue to be an inspiration a fantastic
inspirational story into cyber security Uh thank you Thank you Raj
[Music]
Listen on your favorite platform and stay updated with the latest insights, stories, and interviews.
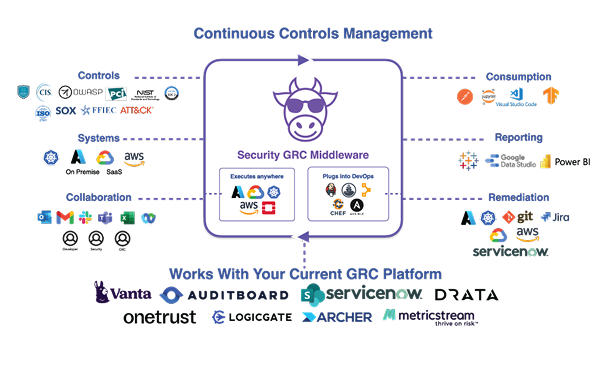
Want to see how we can help your team or project?
Book a Demo