In this episode, Raj Krishnamurthy sits down with Kieran Pierman, GRC & Security at Whatnot, and a former security, risk and compliance leader at Cruise and Dropbox, to explore fresh perspectives on Security & GRC (Governance, Risk and Compliance).
Kieran opens with a bold stance: data breaches, while critical, aren’t the top threat they used to be. Instead, he argues, maintaining availability and service uptime is now paramount. Drawing from his unique experience building the foundational GRC program at Cruise, a pioneering self-driving car company, Kieran reveals how managing cybersecurity risks took on profound urgency—literally life-and-death implications—when securing autonomous vehicles.
Throughout the conversation, Kieran shares actionable insights on:
✅ Why availability and uptime are today’s most critical security priorities.
✅ How building GRC at Cruise required an uncompromising security posture due to the potential consequences of vehicle security breaches.
✅ Why GRC should be seen as an engineering discipline rather than a checkbox function.
✅ Practical strategies to shift GRC from a cost center to a profit-driving role.
✅ The importance of automation, technical fluency, and proactive risk management.
✅ Balancing preventative and detective controls to optimize both security and business agility.
✅ Tips on working effectively with auditors to enhance, rather than hinder, security maturity.
Tune in to learn how adopting a proactive, engineering-minded approach can elevate your GRC program from compliance-driven to business-critical.
🎙️ Security & GRC Decoded is brought to you by ComplianceCow.
🚀 Enjoying the Show?! 🚀
Don’t forget to like, comment, and subscribe to ensure you don’t miss out on expert insights from industry leaders shaping the future of security and compliance.
Learn More / Connect with Kieran Pierman
💼 LinkedIn: https://www.linkedin.com/in/kieranpierman/
🌐 Company: https://www.whatnot.com/
uh-huh uh-huh [Music]
hey hey hey welcome to another episode of Security and GRC Decordered i’m Raj Krishna Morti your host and today we
have the fantastic Kieran with us today as our guest kieran is responsible for
GRC and security at whatn not and has led security and compliance engineering and assurance programs at companies like
Cruz Dropbox and Ernstston kieran welcome to the show thank you Raj
pleasure to be here really uh looking forward to this conversation today and uh thank you for having me
so let’s start with something we we ask our guests all this question all the time let’s start with something controversial right what is one
controversial opinion that you hold on security and GRC security yeah my
controversial opinion is uh that the data security or data protection um side
of security has become a lot less relevant uh over time and uh and I say
that meaning that I think the like platform protection sort of availability
side of security uh has become a lot more critical you know when I like when
I think about risks that a company faces the
things that get the most attention from executives and um you know have the most
like immediate revenue impacting uh uh potential are around like the site or
service being down and and customers not being able to use it and
um I feel like that’s really become priority number one whereas like all of our data don’t get me wrong
I think it’s important but you know the reason it’s a controversial opinion is like all of our data has been through so many breaches at this time that we’ve
become a little bit um you know like immune or or um you know the the
notifications have become so commonplace that it’s almost like who cares right
when you get another notification you know who cares that your email uh is is breached again or that you know an old
password that you’re using for some site is breached like um it uh I just sort of delete those
emails and move along right uh but when a site is down if I can’t use something or you know if a company can’t generate
revenue that’s um like that’s what draws attention that’s what um like security teams I think really need to be
protecting against no that’s a very interesting viewpoint it is definitely controversial so what what I’m hearing
you say in fact we had one of our other guests that came on the call and he said the exact opposite of what you’re saying
right but what I’m hearing you say is that in a world where we assume breach
right data is out there and you’re not saying it is not critical what you’re saying what you’re saying is that it is far more important that we understand
the nuances how we build these systems from an availability and resiliency perspective rather than this very
religious focus on data yeah exactly i think you know I think a
data breach is absolutely going to affect you know every company and that’s not definitely you know I’m not saying
that it won’t but um uh it definitely like affects companies
to different degrees particularly if you are like a critical service that companies can’t really move off of very
well like I don’t know I’ll pick on Workday as an example like you know it’s a big HIS that if they had a breach I
just realistically don’t see that many companies like ripping out workday and replacing it um but uh but if workday is like down
you know suddenly your like onboarding systems don’t work terminations don’t work
um there’s I mean there’s a lot of things you can put in workday different companies do it different ways but like payroll might be in workday right it’s
um suddenly a really big deal if the service isn’t available you know similarly I don’t know if you look at
like Amazon that’s more of a BTOC um example but like Amazon if all of my like order history
on Amazon was breached and like made public I’d be like “Okay whatever.” Um but
uh if the if Amazon.com doesn’t work and I can’t buy things uh even for you know
10 minutes that’s you know millions and millions of revenue impact uh for a company of Amazon size so yeah I mean
that’s that’s kind of my point is like that’s where I think the like real scale and impact comes in is is when your
service isn’t available because of some um cyber security issue and that’s um that should be given a lot of weight
when doing like risk assessments got it um let’s talk about you Kieran how did
you start your career in security and compliance yeah I feel like I sort of wound up here
by accident but I’ve had a lot of fun doing it over the years so I’ve you know leaned into it and and kept doing it i
um in college I studied in in um information systems business information
systems and wound up working for EY uh one of the big four doing um like a lot
of sock 2 audits socks audits this sort of stuff um and while like I enjoyed doing the external side it definitely
wasn’t what I wanted to do forever so um I looked for an opportunity to jump internal
uh at Dropbox spent some time at Dropbox which was like an awesome experience and
Dropbox had a relatively mature security program um security compliance program at the time so you know a lot of that
was just like seeing how a well put together program runs and like getting the opportunity to to contribute to that
um wasn’t too long till I felt like I really wanted to like build something myself which is why I jumped to Cruz pretty early on in Cruz’s journey and
was able to really build their security GRC program from the ground up um and then you know similarly doing something
uh uh here for whatnot and yeah just as it’s as my career has progressed uh I
found that I really enjoy GRC as like um an intersection of people problems and
like technology or security problems and like that’s that’s what I have fun doing is like kind of solving that that inter
intersection of of people and and technology um and uh yeah and it’s truly
been like a a fun career so far okay you said something also interesting at Dropbox right i you did something around
incident response management am I saying this right is that what you did what what was that about and how did that
intersect with GRC yeah that to be frank like was there wasn’t a ton of overlap
um but what it was was I was running Dropbox’s um business incident response
uh program so when you know there was some engineering issue where we needed
to reach out to customers um to tell them about the issue uh you know either
we accidentally deleted some data or there was a corruption in in some file or uh I don’t know there’s a freeze on
their account you know whatever it might be um I like kind of ran the team or program that was responsible for
coordinating the response from legal and marketing and comms and uh customer
support and all these different functions to make sure that we you know are reaching out to the customer and um
kind of treating it with a with a unified voice and and making sure everyone you know was in the loop there
um and uh yeah it sort of wound up on my plate as a a function within legal um at
Dropbox the GRC team was actually within uh legal rather than uh within like security engineering um but yeah wound
up on my plate and and had a lot of fun doing that uh it was really cool but uh not like there wasn’t a ton of overlap
with with like traditional GRC work uh there um yeah I I would say what I
really appreciate about that experience though is like now at whatnot we’re such a small team that I find myself uh you
know on call for like frontline incidents again um and uh and that experience is really
helpful because you know I’ve I’ve been through that incident process for you know customerf facing incidents uh quite
a bit and you know was able to just pick it up very easily here um cuz I’ve I’ve
done it a lot in the past so does that help you uh as you said there is no
overlap but GRC tends to be mostly an insidefacing function and given your
experience around instant management does that has that helped you or does that help you in any way on how you
think about GRC yeah I mean I think it keeps you really grounded with uh the customer with the
customer experience what the customer faces the like real life problems that
you know subsets of customers are running into um and that’s all just I
think just helpful probably in any role but like you know within GRC as you’re thinking about like you know risks
um uh it’s helpful to keep in mind like what the customer experience uh really is and um yeah and also as you’re
thinking about okay where do we want to like take a compliance program what might be important um if you know
customers are complaining about a lot of availability incidents maybe that’s a good like segue or pitch into adding
like availability criter criteria into a sock too um so you know I think those those sorts of angles are I I I have a
very strong feeling that the controversial opinion that you start to do this very much informed based on what
you have seen in the field right um and I think that is very interesting so this
creates customer empathy and I don’t know who talks about customer empathy in GRC but that’s a very fresh perspective
yeah yeah absolutely i think um you know again I know I’ve said it I
I don’t want to say that protecting data isn’t important because customers you know I think customer empathy and caring about the customer still very valid and
important for their data you know safeguarding their data is is very important but um yeah it’s like the true
frustrations come out when uh when they can’t use your product at all so yeah as
a as a compliance engineer and leader what is your view of GRC governance risk
and compliance yeah I feel like GRC a couple things i
feel like GRC should be like one and the same with security like I don’t think they should
be viewed as two separate functions uh you know I mentioned earlier Dropbox had GRC on the legal team uh and while there
were some advantages to that mainly that being like um when compliance or GRC asks for
something when it sort of has like the weight of legal behind it um it’s often easier to get things done um or like you
can you know align priorities more quickly that was nice but you know
having been on teams where it’s within legal and within security I prefer for it to be within security um because I
think GRC and security work really well like hand inand GRC and security to me is like GRC is the um kind of like
scaffolding that all the other teams can use to um mature level up build their
organizations you know GRC I think is the one function that truly sees um
across all the other domains of security right like GRC is the function that has
um requirements or controls or processes to understand you know how apps should function how detection and response
should function infrastructure security you know uh corporate engineering and and employee endpoints right all these
sorts of things um whereas you know all the other groups sure like they have a
you general knowledge of all of security but um tend to stay within their own areas and so yeah I see like GRC as the
kind of like glue or like a connector bridge across all these different um
subdomains of security that kind of has the holistic picture of what a security program should look like and and when
you lean on GRC like properly they really can um like you know use the
scaffolding example again be be the scaffolding for the other teams to to reference and and you know work towards
so got it and how do you think others perceive GRC others in the organization
whether it is your leadership team whether it is the other business units that you deal with how do they perceive
GRC yeah well I think it can vary wild wildly based on the organization uh you
know I’ve seen GRC be perceived as um a like necessary thing but very evil
or like a pain essentially necessary evil yes a necessary evil um but not one
that you know anybody enjoys or like really wants to deal with um and uh you know I’ve seen people’s
attitudes be like they’re essentially like useless uh paper pushers and uh you
know and they exist because you know some legal requirement or like a cert uh
uh insurance you know agency requires it this sort of stuff and uh and I
understand you know where those those trains of thoughts like comes from and how those originate absolutely because I
think you know in its worst form um GRC can be like that but
um but it also can be so great right like GRC can be um like truly a hub of
like knowledge and best practice and um like hands-on work to help all the other
like security domains help like product uh implement security better all of
these sorts of things um and so yeah so I’d say Like I’ve also seen
security be viewed or uh GRC specifically right be viewed as a uh
huge value ad for for security and for the organization um
and you know maybe we’ll getting we’ll get more into this later but I think when you can position it as a uh you
know as a valuable thing tied to business development or or business objectives that’s really where you start
to see that value um and ensure that the GRC teams are you know
uh valued or or uh seen how you know for their best yeah okay i in fact I was
going to ask you the question in terms of how do you think we can change the perspective for the better i think some
part you already answered but anything more you want to add yeah I mean I think the like core idea underpinning it that
is um making sure GRC is seen as a um
profit center and not a cost center essentially right position GRC to be seen as a function that drives new
business not as just a function that you have to pour money into to keep the business afloat and you know what I mean
by that is like working closely with um sales or business development um to
understand like what target markets the company is trying to target um what
customers the company might be trying to go after and understand
um what compliance um you know objectives may help them unlock uh that
market you know that may be something like SOCK 2 or ISO but you can get more specific you know like uh the German
automative automotive market is based off of T-AX right and so um you know maybe that’s something sales has come up
against but they’ve always been shot down because nobody’s considered TAX before um so you know it’s a good
example of like okay work with sales and see if uh you can essentially unlock a new market to for the business to to
target um I use you know PCI is probably the easiest example there where uh you have
to have PCI if you want to be able be able to accept payment cards um you know that’s a clear revenue driver of like
GRC has unlocked or like maintains the ability for the company to collect credit cards that’s a huge uh like
revenue driver revenue enablement um function and um anyways I think all of that is
important is important because the more you can show that GRC is tied to revenue growth then you know you unlock much
easier time of getting budget um getting headcount uh just getting you know
visibility that you need uh at the company to to make your uh initiative
successful okay and and when you and I think that’s a very interesting point you’re saying so you’re saying it is not
a cost center it is it has to be looked at from a profit center perspective which helps you with unlocking deals
right getting into new markets penetrating so on and so forth but what does that mean for GRC practitioners
Kieran do they do enough for compliance so that they can uh they can they can
sort of unlock some of these opportunities are there more things that they have to do from a security perspective uh that can more add more
value to security as an apparatus Yeah I think GRC or I should say like
any security standard out there um let me add some more copouts most
security standards out there should be seen as like the minimum bar for for the company to achieve right
um companies that get breached have a litany of uh you know security standards
uh that they can attest to or have audited and you know that having having security standards does not make you
secure um so I think making sure that it’s understood that like yeah the
standards that GRC is putting forth can be tied to like business development but that is not where security stops like
security needs to continue maturing um and I think when you know when you
look like at a standard like suck 2 it’s very flexible by intention and like in
its worst form it is a terrible check the box exercise where you like explain
away most of the requirements and get an auditor that doesn’t care that much um you know and you get a meaningless like
report um but in its best form it has like great controls around ongoing risk
management where you need to be constantly assessing your security program and putting in controls that
don’t exist anywhere in the wording of SOCK 2 but if you are following the spirit of what SOCK 2 is trying to get
at you know you’ll be constantly finding these risks and putting in like net new controls that yeah may never be tested
in the audit but like continue to mature your program the way they they need to be so little bit of a roundabout answer
to your question but I you know I think that’s really like continue added value comes comes after um you know after you
kind of get the initial certification or report or whatever it is is like really following the spirit of what these
standards are asking for and continuing to protect your company do what’s right for the customer um by advancing and
maturing your your security got it and I want to double click on this uh risk is
contextual and I wanted to maybe if you can double click on your experience at Cruz as you built you were one of the
foundational you built the GRC program at Cruz what how did you what did you
think about from a from a risk perspective at Cruz how was that thought process yeah so Cruz you know for just
broader context was um self-driving cars and the when I joined it was very much
an R&D research and development shop um where any vehicles out on the road you
know had a safety driver behind the wheel um so our risk profile like evolved over
time but the important thing or I think like the biggest takeaway is the number one thing that we were always focused on or what we knew the top risk was um was
a remote takeover of a vehicle that would cause the vehicle then to you know be used as a weapon drive it into a
crowd of people something like this and and that was always the like number one
risk on our minds that we were trying to to protect against and so with that you
know you’re literally dealing with human lives and uh at the scale that Cruz was looking to get to um a you know remote
takeover of numerous vehicles at once could be like a serious large-scale terrorist attack essentially
um and so with that came yeah just a
like um lower risk tolerance for anything connected to the vehicle itself
um you know crew still wanted to like be agile and and move as fast as possible
and you know that was we did our best to do that in in areas where we could but you know when it came to connections to
the vehicle things like our remote assistance um uh service to to help vehicles you know out of like
complicated construction zones or or things like this or um you know the the vehicle network that was hosted uh in
the cloud they you know just had a very low
toler tolerance for um for security risks and we would focus a lot on like
network segmentation and zero trust and the CI/CD pipeline for deploying to those services
um yeah and that you know is very different from my
experience at whatnot where we you know security is extremely important we have
a lot of user data we have a active um you know service that hundreds of
thousands of people are using all the time and um but we don’t have people’s lives like
on the line right so we can take um we can take a different set of risks um at whatnot um you know we can rely on more
uh detective controls in some instances uh rather than preventative if that makes more sense for the business um and
I think like I think that context is is really important when you’re doing that risk assessment right
because you have to match the like controls to the company um the preventative controls you know have
the potential to be more disruptive if they’re going to like block something from happening whereas detective controls you can allow a process to
happen and like check after the fact to see um uh you know see if it happened as
expected or not and so yeah just important um important context to match match the
control to the company make sure it makes sense to sort of Okay okay and I I think that’s an interesting uh switch
from Cruz which is a software definfined vehicle company to whatnot which is a retail large scale I mean high-speed
retail company and what were some of the learnings that you were able to apply from Cruz into whatnot
yeah definitely some of the learnings were from like early on in my cruise
days when it was still an R&D company there was still this like sense
of you know we need to make sure that processes are mature or are secure um
and you know coming from Dropbox seeing a like relatively mature program I knew
what those processes needed to be um and so early on you know I tried to sort of
force maturity into cruise um but didn’t
take the time to like really understand the risk uh at that time what I mean by
that you know is like when it was an R&D company there were safety drivers in all the vehicles and so we didn’t need the
full suite of security controls turned on on day one because you know even in the worst case scenario of a like remote
takeover of a vehicle the safety driver just like pulls the vehicle over and turns the car off right uh and and
you’ve mitigated your risk um so you know one one simple example is just like access reviews right uh a typical like
security control that that you you must do for you know any any security standard really but um they can be like
really ownorous timeconuming especially early on in a company when um access has
been given like pretty widely and uh you know trying to get crews to like
immediately start pick up picking up and like doing access reviews for a lot of
their applications um just got a lot of push back and you know when you take the time to like sit down and think about it
like yeah it wasn’t like there wasn’t right justification for why we need to do these like full access reviews right
now given the broader like risk profile um so anyways that’s definitely like one
of the learnings I’ve taken forward is you know match these security controls to the maturity and risk profile of the
company um don’t force maturity when the company isn’t ready yet like maturity is
a journey and like you know if you look like a a maturity model there’s steps one to three or one to five you know
whatever maturity model you’re using and I generally don’t advise companies to
try to like skip from one to four or something you know like they’re steps for a reason even if you know what four
should look like step four of majority should look like you should probably go through two and three u first to um to
get there because it it’s just part of the journey the company needs to go through to like learn and um and be
ready so okay and what were some of the unlearnings what did you have to unlearn
from from cruise into whatnot yeah
um I think forgetting um forgetting some of
the I’ll say like size I guess um was important like even when I first
joined Cruz we were roughly a 30 person security team I think
um and so you know at that scale you have at least a few people in each
domain of security uh focused on their area and that’s great but what it means
also is like there’s less there’s just less sharing of resources right you don’t need necessarily need the GRC
person like doing uh helping out with detection response or like um helping work on like cloud security
um and so but I wasn’t all that’s very different right we’re like a team of um
six and we share resources across um all the different security domains um I help
out it I help out uh you know in cloud security in in detection and response
and so um yeah just making sure that we’ve breaking down the you know silos
kind of has a taboo but you know for lack of a better word like silos that that crop up as you as you scale as you
grow to bigger companies and like um moving back to like a flatter uh flatter structure okay and I’m assuming that to
your earlier comment because you you see GRC as an oversight function and it can
look at a holistic I think you use the word scaffolding i think you are in the best possible position to look at this
holistically as well yeah yeah i think um you know one of
the one of the things that we often did at cruise that I would like to do like differently at
whatnot is um teams the different like subdomains within security were really
like completely responsible for setting their own road map and then would sort of like share that out with the broader
team and um and I don’t think like GRC had as big of a role as it should have um or like
what I came to like realize in hindsight uh over time and you know to be clear I think teams
need to be in charge of their own destiny you know no team or nobody understands like better the risks in front of them or like what needs to be
focused on than the subject matter experts so you know I’m not saying like GRC should dictate the road map of appsec or or infra or something but um
we do understand like what the maturity of those different domains look like Um
and I think GRC should have like strong input into uh those road maps and like
that’s definitely part of what I want to do at whatnot is um be much more plugged in with those domains working with the
um like leaders of um of each area and you know helping shape uh that that road
map over time proactive GRC yeah what do you see as some of the
organizational challenges that typically we you see GRC teams facing that they
need to overcome yeah um I
think budget like is always budget can always fluctuate right like based on how
the business is doing um the like both headcount or like
headcount budget and like tools budget uh fluctuates but
maybe this might this might you know overlap with it with another area a bit but you know what I see is like
shortterm um prioritization over long-term scale being a challenge so
what I mean by that is like and I’m guilty of it myself uh an easy thing to
do is like as as a GRC practitioner is like keep your head down pass the audits
make sure the controls are successful and like don’t cause problems for uh for
leadership and then like and then you’ve done a good job right um and that’s great but what that often winds up winds
up with is like manual controls or just kind of like sticking things together to like pass the the next audit um and it
causes processes that like really should have been automated to stay manual like way longer than they should
um and I just I see both like in programs that like I’ve run and in in
talking to other partners a um hesitancy for GRC uh to ask for like
engineering resources um and I think there’s maybe a few different reasons for it uh but yeah you know I think JRC
should be like encouraged to ask for either just like an engineering contractor for like 6 months or like borrow see if we can borrow an engineer
from another team for uh you know a quarter or a trimester to like automate several controls if there’s concern you
know that there’s not enough um work for a you know true full-time engineer fine but that shouldn’t then like preclude us
from asking for a contractor for a certain amount of time or you know or borrowing resources because
um yes just like as you scale to set up processes where people are not going to be frustrated where people are going to
like be like wow this was like well designed by GRC and like thought out you need the automated controls um and
uh yeah and you know just putting like a dedicated engineer on it is is like is what’s needed so what I’m hearing you
say is that you see GRC as as much an engineering discipline as is it is a
functional discipline yes yeah absolutely like I think and I think it’s starting to become more and more popular but like having an engineer a full-time
engineer or or multiple even you know within the GRC team is uh is like
absolutely important and like um uh yeah it can bring a lot of value to getting
GRC teams out of uh manual processes yeah and which goes back to your earlier statement which is that you have to look
at the spirit of what these standards are and these controls are right rather than the letter yes yes okay that makes
sense what do you see as GRC team’s role with respect to auditors and how should
how should we think about it how should we approach it yeah um I think the relationship between like
GRC team and auditor is uh undervalued or overlooked sometimes
um you know and I come at this from the perspective of having been the auditor as well so a couple things one like be
friends with your auditor right like you and your auditor are on the same team is is really how you should be thinking
about it and looking at it um and I mean that even just down to like treating
your auditors as like good people uh you know take the time to like do an offsite
with them go out to dinner um and spend a little time with them because one like
auditors have some of the widest breadth of experience for uh how controls or
processes have been done uh across companies like similar companies and
so you know being able to like tap in and leverage that expertise to help you
uh help your own company like understand how can a given a controller process be done like well what has the auditor seen
in the past um is is really important and then um you know the other thing is
just like having that transparent relationship or like positive relationship with your auditor lets you
be more transparent about like issues that might come up and um and honestly
like it even just like makes like push back uh in an audit from uh you know potential finding go so much easier um
you know yeah when you’re like discussing a potential deviation or finding um there is like some implicit uh trust
that is built when you have like a positive relationship when you’ve been transparent in the past and auditors are
much more willing to work with you help you solve the issue to like come to a uh
you know to avoid a finding or something rather than sort of just like you know giving the you the default like this
failed here’s your here’s your finding so you had mentioned to me when we were
talking that um I think you would be prudent in auditive selection am I reading too much into it how do you do
it yeah 100% so you know I mentioned this a little bit uh earlier as well about you know
SOCK 2 can be a wonderful standard with um you know that that does a great job
guiding a security program or it can be like a paper exercise that doesn’t mean much and the auditor has a huge piece in
that um I I think our like industry as a whole
is actually like um coming up against an issue where suck 2 is getting watered
down more and more um a lot of these more just like uh you know check the box
reports are coming out that don’t mean that much and yeah in my opinion that like comes back to the auditor right
because auditors have a lot of discretion around what is like
considered um acceptable in terms of meeting the points of focus within SOCK
2 and the rigor to which those controls are tested um you know I’ve seen sock 2
reports where they called it a type two but when you like look through the testing like testing steps they just did
a test of design for every single one like there was no test of effectiveness there was no sampling and so I’m like sitting there scratching my head like
what like what happened here like what’s going on um
so I mean ultimately I would actually I would love to see the AICPA come out with like stronger standards um that
auditors are held to um because you know I think anybody you know asking auditors
even to self audit themselves just isn’t going to happen or isn’t realistic but um yeah all that to be said you know you
can you should pick an auditor that is going to uphold some level of like rigor
um you know will push back on you sometimes because you if you are just getting sock 2 for the sake of like
putting the sock 2 seal on your website you’re doing it wrong like just you like you know you’re watering down like the
whole industry and like you’re making it worse for all of us um and uh getting
push back from others is is a good thing right like that’s helping you mature your security program um you should be
looking for an auditor that challenges you well said our audience um has GRC
security engineering and possibly it as well maybe it’ll be helpful to define
test of design and test of effectiveness briefly yeah yeah absolutely so yeah test of design versus test of
effectiveness is basically the difference between a type one report uh sock two type one and sock two type two
so test of design is a point in time test of a control so just like on the
day the auditors show up can you prove like we pick change management for a reason you know can you prove that all
your changes were actually like peer-reviewed and approved and tested correctly sorry I shouldn’t say all your
changes one change you know one change that is uh picked uh can you prove that that one change was um was actually
approved and and tested as expected um and that’s tested design like did you design a control uh according you know
uh well according to to the control stated test of effectiveness is did that
control actually work effectively operate effectively over a period of time and that’s type two right so if
you’re doing 3 months 6 months year report whatever it is the auditor is going to sample a bunch of changes over
the last um you know over that time period 12 months and you need to prove every single time for every single
sample that it actually worked as expected um which is much much harder to do right um setting up a process that uh
that always works um rather than you know cherrypicking a good example uh to to prove that it works you know in
theory by design so what do you see as some of the technical challenges that the GRC teams face
yeah um I think a lot of like traditional GRC
practitioners don’t have like a ton of um software engineering background um
you know even myself I’m I’m not a software engineer by trade but I’ve um learned a lot over time where I can uh
you know spend a good amount of time in in GitHub and uh you know be be figuring things out myself now but um yeah you
know I think one of the technical challenges is literally just like technical ability right uh I think the
the ability to recommend good controls that are automated can scale that like
fit well into the overall architecture requires really like a comprehensive understanding of
um software engineer engineering fundamentals from like okay you know is
what does your infrastructure look like are you on Kubernetes and like if so um what’s the like uh you know container
image that’s being used for that versus um versus like if you’re on your own uh
uh stack and you need to control all the way up from like bare metal um you’re looking at a very different
like set of controls um and even just like taking the time to
understand how different systems like interact with each other uh you know like at whatnot we use um Snowflake as
one of our data uh warehouses but understanding like okay how does our data actually get from our backend
systems into Snowflake um and like do we need like checks or like controls on
that ETL pipeline um is important otherwise you’re like only kind of looking at like an input and output and
missing how you know how the data gets from from one place to another okay I I think you said something very
interesting when we spoke uh last Kiran you said you don’t buy into this argument of speed versus security um you
don’t think that they don’t have to be at odds you don’t think security is a gating function can you explain that a little bit yeah I think the com or the
like classic security uh and business like dichotomy right is that security is
going to make the business go slower um and while it’s obviously possible that’s
why it’s like you know one of the classic issues I don’t think it has to be that way or it shouldn’t be that way when security is done uh done right or
done well and so you know thinking about when we’re thinking about controls I
think thinking putting in place controls that are as low friction as possible um
or even make things more efficient for the business is really really important
and so you know a couple examples there is like um MFA it’s a you know it’s a very basic
security control it’s going to be non-negotiable we’re going to need MFA and like if you do it wrong it’s going
to be a pain for everybody and so that might be you know if you’re doing like one-time passcodes or like SMS uh uh
texts uh codes uh even like pushes to your phone are like both less secure but
also like annoying for people to um to answer uh and so like that’s going to
create uh just friction in the process but if you put MFA in place where you’re
using like biometrics or some form of like some form of fishing resistant um web a or you’ve got like a Ubi key or
your fingerprint or face ID um it becomes like both both mo more secure
and way easier for users um to authenticate when you know they just use
their face they’re already looking at it um and they can get in um that way uh
yeah you know another um another example might be with like uh change management
i think getting peer reviews you know is a pretty ubiquitous control even apart
from security you know pretty much every company does peer reviews on changes just because it’s uh good practice but
um making sure you have a really uh easy and like accessible process for people
to push emergency changes uh that don’t require peer review and that you can
just you can get alerted and like check after the fact if um you know if something gets pushed that way is
another example of like you’re still covering your risk uh by having a detective control in there but you’re
also letting the business like move fast when they need to and not being a blocker or disruptor um by uh you know
by allowing changes to be pushed um without an approval um yeah you know
there’s access examples as well of like setting things up to be self-service with preset rules about who can be
pre-approved for different um different access even like beyond arbback right arbback is a great start but um yeah
even beyond that you can set up like automatic rules so that like an example would be for an admin break glass
function we have it tied to a page duty rotation at whatnot so you know these
people don’t have access to admin all the time but the pager of duty uh schedule for the person that’s on call
can grab the admin access if they need it um to solve a problem super low
friction you know addresses the security risk of just having a bunch of admins all the time um yeah no that is very
interesting and I think you have also been a big proponent of using GRC beyond the natural sense of controls like right
sizing access can you can you talk about that a little bit about for our for our users audience yeah I think GRC
particularly at um you know smaller companies although I I think it should hold true as you get larger um although
I understand that like a lot of GRC’s time just gets taken up with audits uh as you get to larger companies but um
yeah GRC can really be a function to help mature these basic security
controls um across the company so you know something like arbback um at a you
know startup they may have heard the term but like it’s unlikely to have been implemented well yet uh and that’s
something that like GRC has a lot of experience uh with knows how it should look um you know has possibly like set
it up before and so like that’s something I think is great for GRC teams
to do is like integrate closely with it and like help set up arbback uh at the company and you’ve like it it does so
much good right arbug arbback done right creates so much efficiency for the company because people have the access
they need on day one there’s no like just so much less people like running around trying to figure out what they
need and how to get it um and at the same time like drastically reduces overprovisioning of people just saying
like uh yeah here have admin because we don’t actually know like what um access makes sense uh and so yeah just you know
it’s something that works so well hand in hand and uh like I’m a huge proponent of using some GRC time GRC time to not
just consult on these best practices but like use it and and do them do them ourselves yeah well that actually that’s
brilliant because I don’t know if you know this Kubernetes has this command line utility called can audit it started
as an open source project where they are basically looking at your access logs and trying to determine whether the
roles are right sized right when the user accesses so actually that’s a brilliant way to think about this
problem um I think this brings me I mean this analogy that you’re talking about speed versus security is also very
interesting because it brings to my memory DORA the DevOps uh research and assessment where they are basically
challenging those this notion of velocity versus stability and they’re saying they don’t have to be at odds at
each other right I mean you can achieve both from a de
Yeah yeah exactly i think um I think when done right right they
should they should work together like you can you can have security and um and
speed you can uh you know have a good DevOps process that uh that works well
quickly um but it does like you Yeah I mean you have to take a
sec to like think about it and um uh and just like be willing to like
be creative right like sometimes you have to move away from some of the like most traditional uh implementations of
of a control but that is a good segue because you also earlier talked about balancing between preventative and
detective controls i want to double click on that how do you think about this k yeah so you know yeah I mean
every company is unique obviously and like you’re going to have your own risk profile but um
the not in in the hierarchy of controls right preventative are the best like
most um like generally strongest controls you stop something from happening entirely um and detective
controls are uh generally like on the weaker side because the issue or
whatever it is would have already happened and and you’re finding out after the fact but um but that doesn’t mean that like
preventative is always the control you want to push for um right when you do a
risk assessment you can you determine your like inherent risk there and then
figure out you know what your target risk is or what your um you know what your residual risk that you want to get to is and if you know two um detective
controls get you to your risk target like there’s a good chance that that winds up being better for the business
um than like one preventative control and so um yeah you know uh if we use uh an
example like it might be um something like uh you know Terraform
configurations where we could put a preventative control in
place that stops somebody from like pushing a change without approvals from you know uh three different teams that
you know that all have their hand in this um and yeah fine but like that creates lots
of opportunities for things to slow down you know people are out and um there’s a lot of back and forth etc
um whereas you can have a detective control and you’re able to like still be
notified that something happened something changed and follow up if it is of interest but nobody is nothing’s
being blocked because somebody was like out for a long weekend or like out on PTO um you know or like wants to have
like an in-depth uh uh like conversation about some like semantic point of it
like that conversation can still happen but while the business is able to move forward with like with the change that
needs to happen that’s a beautiful example the terapform example is a beautiful example but in order to do
this what type of culture do we expect to create yeah you definitely need and
you know I I understand that you can work hard to create like a culture of GRC of trust within the GRC team but
like there’s a broader company culture that you have to deal with as well but anyways I think what’s really important is like um a culture that is not afraid
of failure or like encourages failure and iteration right um I think like one
of the best ways to like quickly understand what the right control is and how to rightsize your response to a risk
is um iterating quickly you know put a control in and based on the feedback you
get whether it’s um you know too ownorous or you know nobody complains um
you get that feedback very quickly but um but the company has to be very like open to uh open and okay with things
going wrong or like failure essentially uh and not hold that against you
um you know like I’ll use an example where I uh last week turned off access
um for a permission and I wasn’t like basically it would would have probably taken me like weeks to fully understand
all the imp implications of this role and everything that was going on but I knew it was like way overprovisioned and
so you know rather than spending like weeks looking at all the access logs and where everything is going and how all the permissions correlate um I started
like taking away access and Uh then someone from marketing like very quickly pings me and was like hey like I don’t
have access to approved push notifications anymore and I’m like oh you know sorry like this was me and um
but their response was like you don’t need to be sorry like we’re super happy to like help you test um and like you
know thanks for like addressing this quickly and like that sort of response where like culture lets me iterate on
these controls rightsize that access in like you know I was able to do it in like 20 minutes instead of spending
weeks trying to find you know what the right solution there I I I would love to get a poll out to our audience on that
question in terms of how they feel i’m sure it’s going to it’s going to be all over but that’s a fantastic and an
interesting sort of experiment right i I think what you’re basically saying is the culture of experimentation culture
of risk takingaking right as long as you can act on it and the intent is right you know can Yes yes and I mean like
again you always have to use caution you know like I probably wouldn’t do a do a permission change like that if I knew it
was going to affect you know like our frontline customer support agents ability to like give refunds or
something because you know that’s just like a high volume thing that they need to be able to do i don’t want to mess
with that but um but yeah you know like this permission I was like okay like the worst that can go wrong is I disrupt
like uh push notifications that are scheduled in the future anyways so I’m like okay like let me go for this and
like see um see where we are you talked about earlier about GRC being a profit
center versus a cost center and for the GRC manager who is trying to build a
business case right and learning everything that you’re saying here and today and they want to build a GRC program how should they think about
building that business case yeah I mean as I mentioned earlier I would go directly to the sales or like
business development team to understand where the business is trying to go um understand from leadership or
you know internal company resources whatever it is what the larger business um objectives are definitely talk to
legal as well and compile basically all the different
um I don’t know what the word catalysts uh uh for where GRC is needed and you
know so on the sales or like business development side that may be like new customers or like markets that you’re
trying to address um on the business objective side that may be um you know
generally about like customer trust or um going public right like then socks
would matter there’s different there’s standards for if you are running ads on
your site um there’s MRC now I forget what it is like media ratings council or
something i forget exactly what it stands for but like um yeah in order to like get advertisers to uh be
comfortable running ads on your platform MRC is going to matter so like yeah like if you see okay we’re going to start
running ads on the business objectives if people aren’t already aware that like MRC is probably going to come up and we
should get a head start on that you know that’s where you need to plug in and then on legal side right um uh third party risk uh often ties in
like closely with legal um socks again is like relevant for legal um and
so the compiling all these things and and tying dollar numbers to it right um
the total addressable market uh value from the new business development uh the
oh sorry I completely spaced on the privacy regulations in the in the legal sphere uh right uh GDPR CCPA etc like
are huge for um from the legal perspective that we need to focus on so like understanding what the potential
um costs avoided there would be right in terms of fines um and anyways then you
can put together like a very clear business case of like doing XYZ gets us or saves us this amount of money um and
yeah and then you’ve you know sounds very nice in theory definitely harder in practice but
you’ve essentially put together like your pitch of like this is the profits revenue that like GRC can help the
business generate okay oh that’s beautiful what would you if there is a dream GRC solution what would that look
like okay yeah
um I want a GRC solution that is as
customizable as possible um to automate
not just evidence collection but a lot of times the like operation of controls
right so like um if we are using change management as
an example again you know I want a solution that is not only going to
monitor for when a change is pushed in GitHub without an an approval but I want
it to then follow up with that PR um uh author and be like hey in Slack
ideally or you know wherever we’re working uh you know meet people where where they are um you know hey I saw
this uh PR was pushed without an approval like was this intentional and
essentially like you know have a call in response with them to to address that finding um I don’t you know I don’t just want
like a screenshot or something of the change to like say you know this change got pushed um yeah you know I want that
automation and at the end collect the evidence for me um you know if I’m if I’m continuing
with the uh examples uh you know a GRC solution where if um
uh for access right if we are looking at uh an access
review it should be able to like connect in with octa assuming you know octa is
your SSO and tell me the last time people signed into a given application
um so that as part of the data for the access review you understand who’s
inactive right and be able to provide that information then to the reviewer um like hey you have these 16 people to
review five of them haven’t actually logged into this application in uh you know in 45 days and they should have
that context as part of their review um yeah anyways these are like these are
my dream things i think what you’re saying is very interesting what you’re basically saying is that you are not you’re saying GRC beyond sort of telling
what we do into more a conversation that you’re having with the control owners and the rest of the organization you’re
basically helping them to move from from the baseline get better from the
baseline as much as possible incrementally step by step is what I’m hearing yeah yeah improving from the
baseline step by step and like um and meeting people where they are I
think is the other thing that I would say is really important you know I um teaching people or like trying to get
people to use yet another tool um is difficult and uh and you’re probably
going to wind up spending more of your time right chasing people down uh than getting like results out of them so yeah
you know something that’s built into Slack or email or whatever it is where uh they can just answer like yes or no
and like give you the evidence you need or you know perform their control right there like that just saves both parties
so much time and um and it’s better for security because you’re like getting the control to happen like more quickly and
more efficiently so no absolutely it sounds like a compliance code marketing pitch but that’s another discussion uh I
think we are almost at the end of the segment um Kieran and I want to ask you
are there any podcast books you read people that you follow anything that you
want to share with our audience today yeah um I think uh I don’t know maybe maybe
you’ll have them on at some point if you haven’t you should but uh uh Troy Fine on LinkedIn um I recommend that you know
everyone should follow he has uh he has great content about the security GRC
world um and also like often it’s it’s funny um he didn’t pay me to say this uh
I just think you know his content is worth following and it’s often like very timely about uh you know new standards
that have come out or um you know rulings from uh or guidance from SEC or or whatever it might be so um honestly I
think yeah he’s he’s a great source um I don’t have like one specific book I
would say like I have tried reading a bunch of different books about like risk management and cyber security
um definitely have learned some great things as I have issues uh with a lot of them um but I would say maybe my broader
recommendation is um I was actually able to get like a whole bunch of books like
probably like three dozen uh security related books from Humble Bundle um one time um for like a very very reasonable
price um and that was the first time I realized that like Humble Bundle does more than just video games um so anyways
just a general like shout out for that uh you know always be monitoring what’s what’s available there and I think you
know when you have an opportunity to um to to use that to to get a bunch of like resources you definitely should no
that’s nice i I’ve never heard of Humble Bund this is the first time so Oh okay nice yeah yeah it’s um Yeah it’s an
online like site where they donate like most of their proceeds to charity but um they work with like game publishers or
books to offer uh bundles of of games or books at uh like severely reduced prices
uh yeah and anyways um but but they have a lot of like just great content that that goes through it so well this was a
fantastic conversation Kenan love the conversation so I I think you took us through sort of beautifully the GRC
world and uh I’m hoping we have a better appreciation of the forest and the
trees uh so thank you very much for coming on the show yeah yeah thank you for having me Raj uh this is a lot of
fun uh hopefully hopefully people are able to learn uh learn something take something away from it um and I think
more generally you know I just say my door is always open i love like connecting with people um chatting so uh
you know always happy to for people to reach out and and talk [Music]
Listen on your favorite platform and stay updated with the latest insights, stories, and interviews.
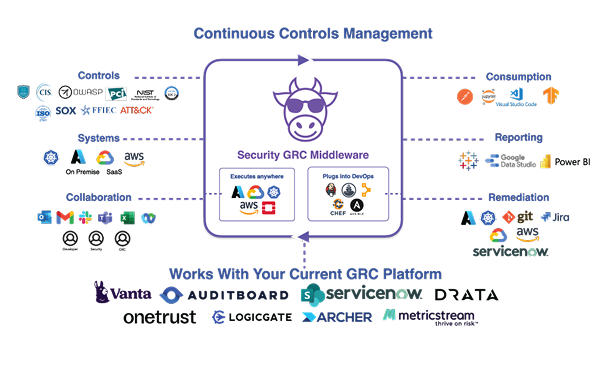
Want to see how we can help your team or project?
Book a Demo