We are releasing ComplianceCow’s Model Context Protocol (MCP) server this week. We are open sourcing our MCP code, which leverages our foundational APIs and graph primitives.
Check out our github repo!
ClickOps to ChatOps
At ComplianceCow, we have always believed that GRC is much more than an annual audit ritual. GRC plays a complementary role to Security. It is like Yin and Yang. However, unless we reduce the toil of evidence collection, controls testing, and even remediation from engineering and security teams, the divide between GRC and Security teams will continue to grow rapidly.
A few years ago, Cloud and ephemeral systems made this divide BIG. Now, Generative AI, with exponentially increasing software releases, is making this divide HUGE.
We can’t address this divide through better UI and dashboards, which most GRC tools seem to be obsessed with. We need to provide information seamlessly to the GRC Analysts, Security Engineers, Architects and even Application Developers in order to genuinely reduce the toil. At ComplianceCow, we see GRC fundamentally shifting from ClickOps to ChatOps.
GRC Engineering Primitives
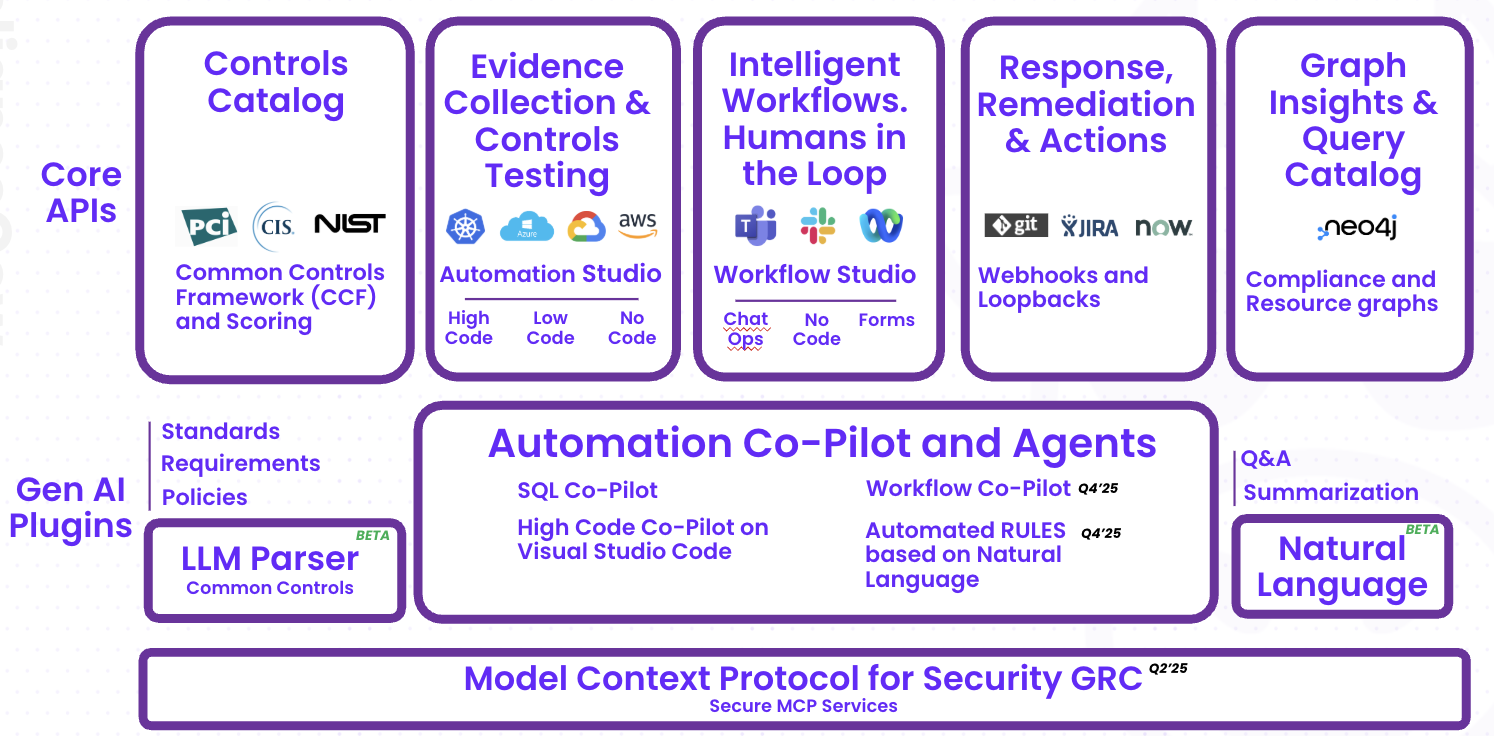
At ComplianceCow, we have been obsessed with eliminating the compliance toil. We saw 2 major challenges with existing tools with reducing toil and bringing GRC in tune with assurance:: (a) Keeping pace with the growth of software systems, and (b) Reducing friction with users, especially outside of GRC. We took a deep engineering approach to solve these problems through 5 primitives:- Declarative controls catalog – An expansive machine readable, YAML manifest bringing requirements, controls, user inputs, evidence schema and citations together
- Automation studio for contextual evidence collection and controls testing:
- No-code drag-drop studio purpose built for GRC analysts
- Low-code, SQL chaining for more complex queries for analysts and developers
- High-code, cowctl CLI infrastructure, vscode extension for golang and python developers for building complex multi-stage compliance checks
- Workflow studio for Slack, Teams and Webex, providing dynamic GRC workflows for all
- Contextual response and remediation actions such as creating a ServiceNow ticket for non-compliant access or automated pull requests for SecComp profiles for a kubernetes pod. These actions are also tracked either through real time webhooks or a scheduled batch process, providing a feedback loop for a 360° view
- GRC Graph Model providing a dynamic fluid data model for deeper analysis and reporting
But Model Context Protocol (MCP) has put this into overdrive.
What is Model Context Protocol (MCP)?
Model Context Protocol (MCP) is an open protocol to connect Generative AI models with other information service providers. It follows a 4 tier architecture;
- MCP Host = Claude Desktop, Goose Desktop, This is the brain that orchestrates across one or more MCP tools. For example, When a user asks, “What is the weather in Fremont today?”, the MCP host will automatically find the weather service, and based on how the tool is constructed, may pass the geo location (= fremont ) and a period (= today) as arguments
- MCP Client = Stub to connect to an MCP Server. The MCP host usually automatically creates (and calls) one or more MCP clients. MCP client maintains a 1:1 connection with the MCP Server, and connects through the MCP protocol.
- MCP Server = Provides specific capabilities using tools (resources and prompts). These tools connect with the application to fetch or push data. For example, the weather service can be exposed as a tool, that connects to https://weather.com (Application) through standard contracts
- Application = Implements the business logic for the service
What is cow-mcp?
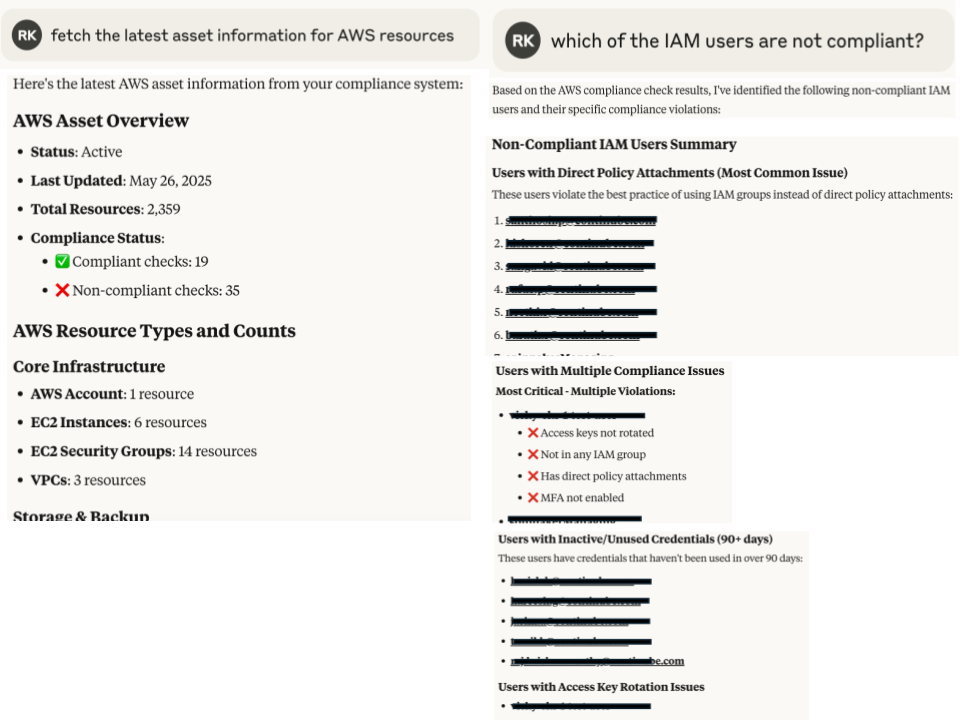
cow-mcp is a secure, open source MCP server for ComplianceCow. We currently provide more than 33 tools that allow tools such as Claude Desktop and Goose Desktop or CLI leverage our partner APIs and GRC Graph Model to provide greater insights into your compliance data. These insights go beyond reporting on control status and control coverage, and can report on resource level data for cloud, SaaS and Kubernetes systems for compliance. You can also take contextual actions, based on your access privileges in ComplianceCow. Currently, these actions are limited to creating tickets in Jira and ServiceNow, notifying users on Slack, Teams and Webex. We will actively work on cow-mcp to build more sophisticated capabilities such as creating complex automation for evidence collection, controls testing and remediation of compliance gaps.
cow-mcp takes a major leap in bridging the divide between Engineering and Security, and GRC teams.
Check out https://www.compliancecow.com/mcp for more details.
How is cow-mcp unique?
cow-mcp is an unique GRC MCP agent for the following reasons:
- Open source: We are taking a transparent approach by open sourcing our MCP Server. MCP is a maturing technology. MCP Hosts and AI Model providers’ (Anthropic, OpenAI, AWS Bedrock, Goose) have varying degrees of support. Customers are bringing their own (BYO) Large Language and Large Reasoning Models. By open sourcing, we provide our customers the choice and avoid any vendor lock-in.
- MCP tools are based on APIs and Graph: cow-mcp leverages ComplianceCow’s standard APIs and flexible graph model. This allows our users to ask deeper questions.
For example,- Give me a list of all non compliant EC2 instances from the latest run?
- What is the compliance status of the EC2 instance prod-west2-ec2-chucknorris-15?
- Users can perform Actions: You can take actions directly from your MCP host such as creating a jira ticket for remediation or sending a Slack notification through the ComplianceCow Actions Engine. Currently, we have limited capabilities for performing actions through the MCP host. We will continue to expand in the upcoming releases.
How does this work?
Pretty straightforward. Have a conversation with ComplianceCow on your MCP-host like Claude Desktop 😀!
What other questions can I ask cow-mcp?
Hmmm…. From compliance frameworks and requirements to assets in scope, you can ask many different questions.
Questions on Controls and Compliance status:
- How many controls are compliant for PCI-DSS v4.0.1?
- How many controls are automated for evidence collection?
- When was SOC2 last assessed?
- What is the compliance status/score by category for SOC2?
Questions on Workflows:
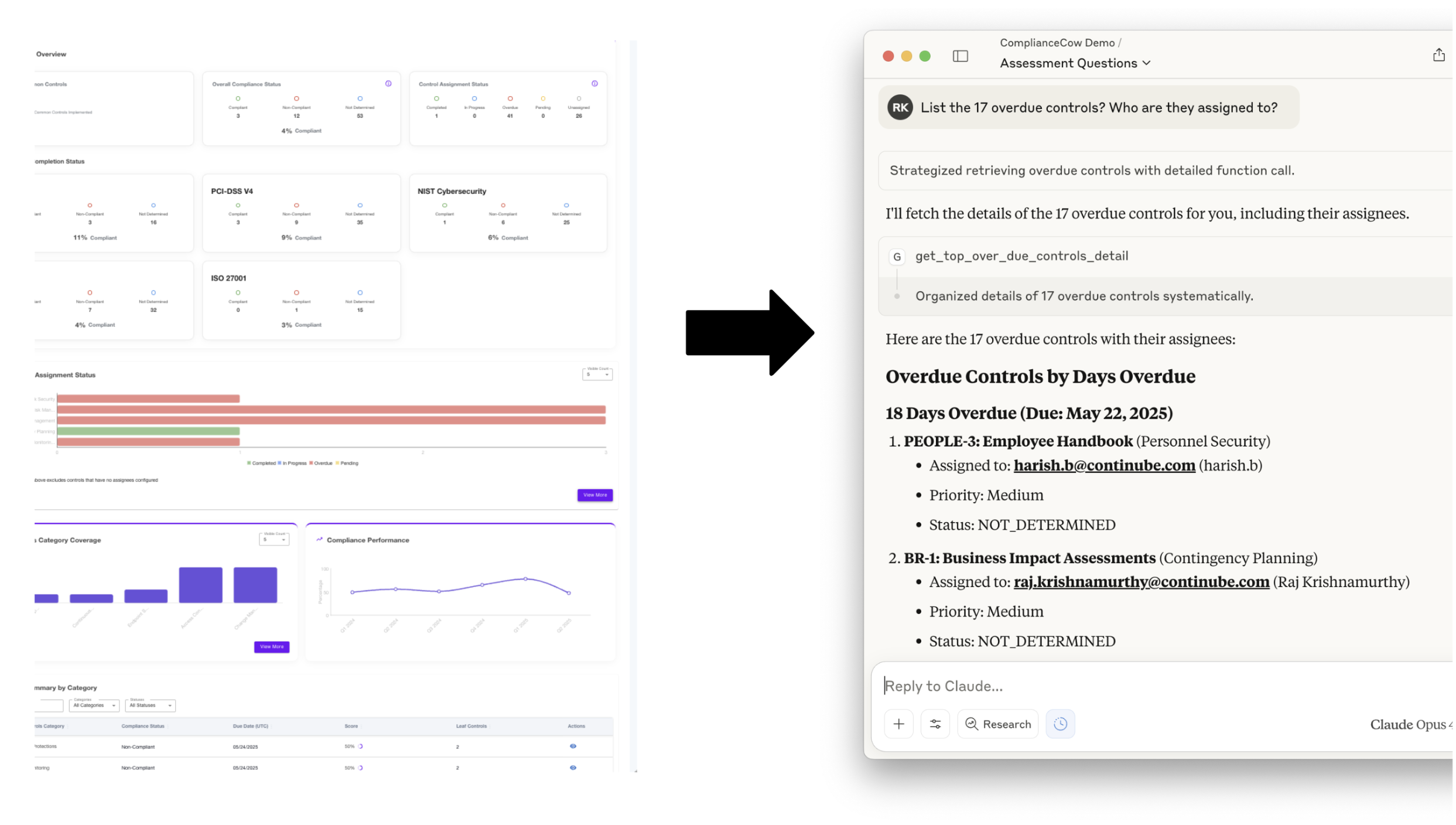
- Which controls are overdue?
- Who are they assigned to?
Questions based on Evidence and Assets:
- Which users are non-compliant for MFA?
- When was this <user> last assessed?
- What is the status of the jira ticket created for <user>?
Questions based on Controls, Evidence and Assets:
- What actions are associated with this control?
- Create a JIRA ticket for each non compliant user you listed as evidence.
- Notify the admin users on slack about the actions that I just executed.
What are the limitations with MCP?
- Hallucination: Language and Thinking (or Reasoning) Models can hallucinate. So, you may not always get an accurate response. However, because ComplianceCow uses a Graph Agent to provide responses from Natural Language Queries, you can verify that these are valid responses by executing them on the compliance graph
- Token limitations: Some of these datasets can be huge. We have architected our tooling to handle this through some techniques such as intelligent pagination, explain queries, summarization, and drill-downs. However, users will occasionally hit the response limits. Restart your MCP-host, if that happens. We expect this to get significantly better as time progresses
- Ambiguous user questions: We have anchored our responses based on context. However, we sometimes struggle to handle questions that lack context or have ambiguous context.
In Summary,
“AI is eating the world”. Users’ consumption of information is rapidly evolving from static user interfaces to dynamic conversations powered by Language and Reasoning Models such as Claude, OpenAI and Llama. Cybersecurity and Governance, Risk and Compliance teams cannot afford to be left behind. However, Security and GRC demand unambiguous answers; How many controls are non-compliant for SOX Change Management? Is this virtual machine compliant? Does this user have an MFA? etc. Generating such deterministic responses from probabilistic natural language user queries have been a challenge. ComplianceCow GRC Middleware + MCP can solve this challenge. We are launching cow-mcp in open source.
Model Context Protocol (MCP) standardizes how the models can process data to and from other information sources. It also provides an “appstore” like ecosystem for specialized agents to interoperate. For example, A ComplianceCow Agent can provide you with reliable GRC data, and a Tableau Agent can produce stunning dashboards.
So, Mission Accomplished? No more UIs? No more Dashboards?
Not yet. But we are getting there…
🔹 Want to see if ComplianceCow’s capabilities fit your situation? Book a Demo
🔹 Listen to other conversations with security GRC compliance leads. Click Here
