Introduction
MCP servers are designed to process structured requests from AI agents, perform domain-specific operations (such as querying databases, applying business rules, or generating summaries), and return context-aware responses. Our implementation allows seamless integration with MCP-compatible hosts like Claude Desktop and Goose Desktop, enabling secure, modular, and intelligent interactions tailored to the needs of modern enterprises.
The tools and resources within the ComplianceCow MCP server are specifically designed to accomplish the following:
- Get Dashboard and Insights data
-
Get Auditable responses through Compliance Graph
-
Perform actions such as creating tickets, fixing policies, pushing data to external tools, etc
Glossary
| Keyword | Description | Example(s) |
| Control | Refers to compliance or security control that needs to be implemented by an organization to ensure adherence to relevant laws, regulations, industry standards, and internal policies. | Ensure that MFA is enabled for all users |
| Assessment | Assessment is a collection of controls, organized hierarchically. This can be an industry standard or a cybersecurity framework. | PCI DSS 4.0 |
| Assessment Run | An assessment run is the verification of the controls in an assessment for a given time period and for a set of inputs. This verification may include evidence either by manually collecting from users or by automatically fetching data from resources such as applications and servers. | |
| Check | A rule or a verification for compliance or conformance. | Check if MFA is enabled for all AWS users in a given AWS account |
| Resource Type | Category or class of resources. | AWS EC2, AWS S3 |
| Resource | Instance of resource type for which we have checks performed. | Specific EC2 instances, Github repositories |
| Asset | A group of resources, of various types. | AWS services (spanning multiple accounts), Kubernetes, Github |
| Evidence | Data aggregated through checks against one or more resources, for a given control. | A CSV file containing the list of AWS users, their details including their MFA status and compliance details (such as score). |
| Action | Any activity (automated or manual) that can be run to respond or to remediate based on conditions. These actions are bound to some specific resources such as assessment, control, evidence or resource in ComplianceCow. | Create a JIRA ticket for a non compliant EC2 instance with SLA not met for remediating a critical vulnerability. |
Architecture
We support the STDIO transport mechanism to allow seamless local integration of our server with your MCP host. At the core of our backend is the Compliance Graph, which continuously ingests data such as assessment runs, evidence, and more. Additionally, our server actively pulls information from diverse sources including vector stores, relational databases, and file storage systems.
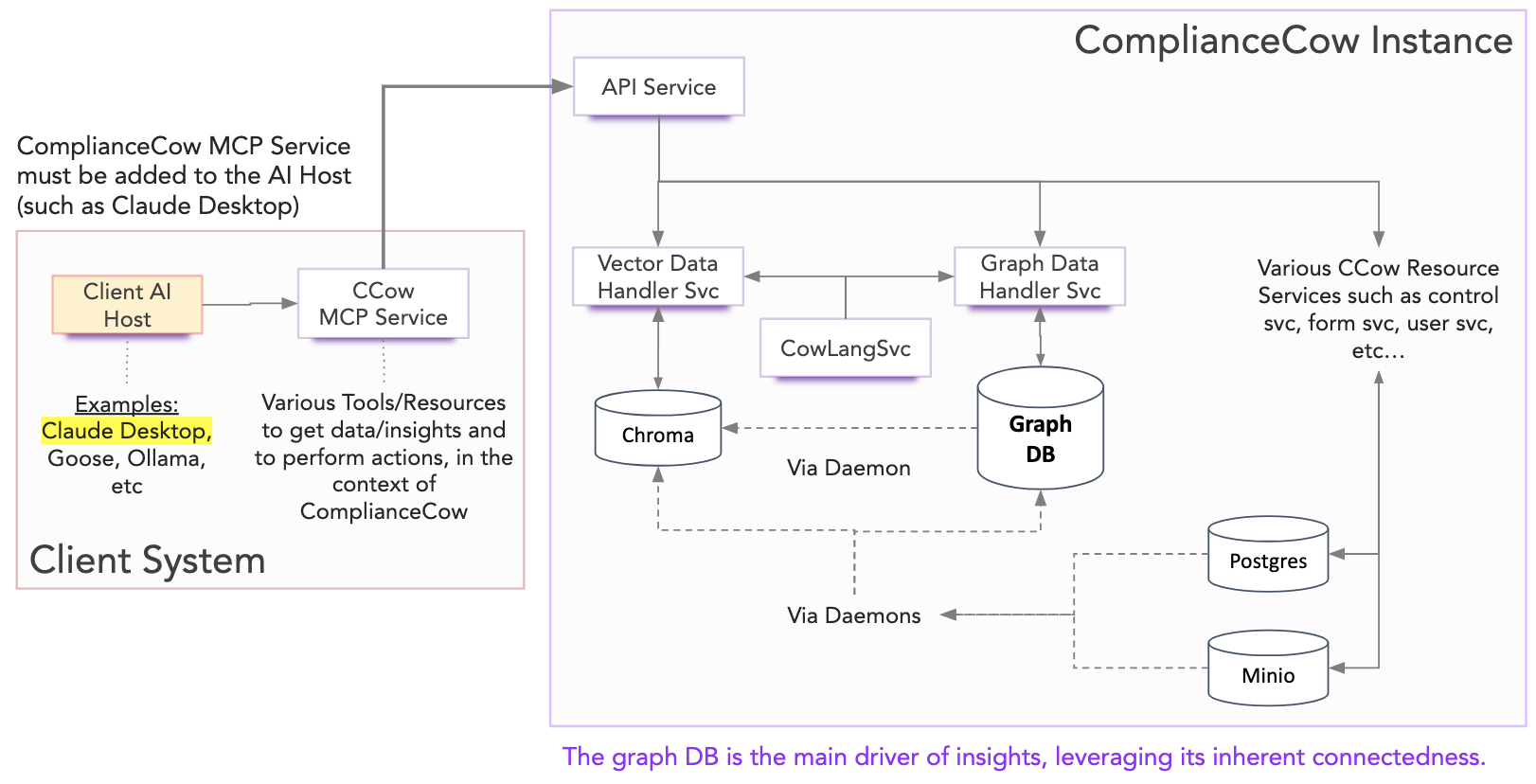
Getting Started
Dependencies
1. You’ll need an MCP host like Claude Desktop, Goose Desktop/CLI, or similar. Below are the installation links for Claude Desktop and Goose.
2. Python and uv (package manager) are required to run the MCP server.
- Visit this page to download and install python for your operating system. Recommended version: 3.11 or higher.
- Visit this page to download and install uv.
Authentication
The MCP tools and resources of ComplianceCow can be accessed through the OAuth 2.0 mechanism with client_credentials grant type. Follow the instructions below to get yourself a client ID and a secret.
- Sign up for an account (if you don’t have one) by visiting this URL: https://partner.compliancecow.live/ui/signup. Replace the hostname with your own if you have a dedicated ComplianceCow instance deployed.
- Click on the ‘Manage Client Credentials’ option in the top-right user profile menu.
- Fill out the form to obtain a client ID and a secret.
Server setup
1. In your terminal/console, go to a folder of your choice and clone the git repo.
git clone https://github.com/ComplianceCow/cow-mcp.git
2. Switch to the repository’s main folder.
cd cow-mcp
This directory will be referred to as PATH_TO_THE_MCP_SERVER_REPO_CLONE in the subsequent sections.
3. Run the following commands to install the dependencies. Only then, the MCP Host will be able to start the MCP server successfully.
uv venv .venv
source .venv/bin/activate
uv pip install .
Server configuration
Below are the key details required to configure our MCP server on your host.
command
We use uv as the package manager. You can specify the uv command along with its path, which will be referred to as UV_BIN_PATH in the following sections. For example, on macOS: /Users/UserXYZ/.local/bin/uv.
args
−−directory <PATH_TO_THE_MCP_SERVER_REPO_CLONE> run main.py
PATH_TO_THE_MCP_SERVER_REPO_CLONE: The folder/path in which you have cloned the ComplianceCow MCP Github repo (in a step above). Example: /Users/UserXYZ/Documents/code/cow-mcp
env
Our MCP server needs the following environment variables set:
- CCOW_CLIENT_ID: Please refer to the “Authentication” section above.
- CCOW_CLIENT_SECRET: Please refer to the “Authentication” section above.
- CCOW_HOST: The hostname of the ComplianceCow instance, which could be a dedicated one for you or a default one such as ‘https://partner.compliancecow.live’.
The next section provides examples of how to use the above configuration values with Claude Desktop and Goose Desktop. For other hosts, you may refer to these examples as a guide for configuring accordingly.
Examples
The steps to configure MCP servers may vary across different hosts. You can use the configuration data provided above by following the host-specific instructions. Instructions for two such hosts—Claude and Goose desktops—are provided below.
Claude Desktop
Update the following json in the Claude desktop config file ( <Claude desktop installation path>/claude_desktop_config.json). Before saving the configuration, make sure to update these placeholders (as described in the section above) in the json: PATH_TO_THE_MCP_SERVER_REPO_CLONE, UV_BIN_PATH, YOUR_CCOW_HOST, YOUR_CCOW_CLIENT_ID and YOUR_CCOW_CLIENT_SECRET .
{
"mcpServers": {
"ComplianceCow": {
"args": [
"--directory",
"PATH_TO_THE_MCP_SERVER_REPO_CLONE",
"run",
"main.py"
],
"command": "UV_BIN_PATH",
"env": {
"CCOW_HOST": "YOUR_CCOW_HOST",
"CCOW_CLIENT_ID": "YOUR_CCOW_CLIENT_ID",
"CCOW_CLIENT_SECRET": "YOUR_CCOW_CLIENT_SECRET"
}
}
}
}
Goose Desktop
Follow the steps given in this link to add our MCP server as a Goose extension.
Running Locally
To verify that the MCP server is properly set up with all dependencies and can be started by the MCP host without issues, you can run the command to check if the server runs correctly in a local environment.
uv run main.py
API Endpoints
Please click here to view the API endpoints and their details, including name, purpose, inputs, and outputs.
FAQ
1. How do I signup for ComplianceCow?
Visit our product site to create an account using various sign-up options, including Google, Microsoft, OTP, and more.
2. What value does ComplianceCow deliver?
ComplianceCow is designed to help with automated security compliance evidence collection, analysis and remediation challenges faced by large enterprises and compliance, GRC and security teams. We are a security GRC controls automation studio for your custom controls and workflows. For more information, please visit our corporate site.