ServiceNow GRC/IRM and ComplianceCow
Continous Controls Monitoring (CCM) of IT and Cybersecurity Compliance & Risk Controls in ServiceNow GRC/IRM
Table of Contents
- 1. Introducing Compliance Management
- 2. Definition of Terms
- 3. Implementing Policy and Compliance Management
- 3.1 Control Objectives and Requirements
- 3.2 Configuring Entities and Entity Types
- 3.2.1 Entity
- 3.2.2 Entity Type
- 3.2.3 Control Objective and Entity Type Association
- 3.2.4 Controls
- 4. Continuous Controls Monitoring (CCM)
- 5. Implementing CCM in ServiceNow
- 5.1 Indicator Templates and Indicators
- 5.2 Issue
- 5.3 Remediation Task
- 5.4 CCM Challenges
- 6. Integrating ComplianceCow with ServiceNow
- 6.1 Running an Assessment
- 6.2 Automating Evidence Collection
- 6.3 Integration with Indicators
- 6.4 Customizing Indicator Logic
- 6.5 Customizing Supporting Data
- 7. Summary
- Appendix A – ComplianceCow Middleware
- Appendix B – Agentic GRC Platform
Guide Summary: Enabling Policy-to-Control Automation in
ServiceNow via ComplianceCow
This technical guide explains how to automate and scale Continuous Controls Monitoring (CCM) within ServiceNow GRC/IRM using ComplianceCow.
It begins by outlining core compliance concepts (policies, control objectives, entities, and indicators) then walks through how ServiceNow manages them. The document then details how ComplianceCow integrates with ServiceNow to streamline evidence collection, automate control testing, and support CCM across hybrid and cloud infrastructure.
Topics include:
-
- Policy-to-control-objective mapping in ServiceNow
- Indicator templates, scripted indicators, and control issue workflows
- How ComplianceCow automates assessments and generates structured evidence
- Integration steps for pushing ComplianceCow results into ServiceNow indicators
- Customization of controls and supporting data
- Key challenges in scaling CCM, and how ComplianceCow addresses them
- Policy-to-control-objective mapping in ServiceNow
The audience for this document includes GRC engineers, ServiceNow administrators, compliance architects, and security teams seeking to modernize their compliance automation stack while leveraging existing ServiceNow investments.
1. Understanding Compliance Management: From Authority Documents to Controls
As the IT infrastructure becomes more complex, interconnected, dynamic and changing frequently with workload demands, user needs, and emerging technologies, managing security and compliance risks have also become complex.
Regulatory bodies publish authority documents defining compliance laws, regulations (such as SOX, NIS2), standards(such as NIST CSF, PCI-DSS 4.0), and guidelines that organizations must follow to manage the security risks. These documents serve as the foundation for the risk and compliance programs, helping businesses align with legal and industry-specific requirements.
Organizations develop policies that specify how their business units would comply with the requirements of the authority documents. These requirements are known as citations (a passage, expression, individual requirement within an authority document). For example, to implement the NIST CSF PR citation : Safeguards to manage the organization’s cybersecurity risks are used, the organization may implement data security, access control and platform security policies.
Once the internal organizational policies are established, control objectives are set up to implement the policies. The control objectives define exactly how to adhere to those policies and citations in the authority documents. For example: To implement the access control policy, a control objective may specify that Users, services, and hardware are always authenticated. To implement the encryption policy, a control objective may specify that the files and disks containing Personally Identifiable Information (PII) must be encrypted with industry recognized algorithms and protocols, such as AES (Advanced Encryption Standard). A control is a specific implementation of a control objective on an entity. A CRM database should be encrypted using an industry recognized algorithm is an example of a control. Encryption of another database containing customer complaints is another control.
2. Key Terms and Core Concepts in Cybersecurity Compliance and ServiceNow GRC
As the IT infrastructure becomes more complex, interconnected, dynamic and changing frequently with workload demands, user needs, and emerging technologies, managing security and compliance risks have also become complex.
Regulatory bodies publish authority documents defining compliance laws, regulations (such as SOX, NIS2), standards(such as NIST CSF, PCI-DSS 4.0), and guidelines that organizations must follow to manage the security risks. These documents serve as the foundation for the risk and compliance programs, helping businesses align with legal and industry-specific requirements.
Organizations develop policies that specify how their business units would comply with the requirements of the authority documents. These requirements are known as citations (a passage, expression, individual requirement within an authority document). For example, to implement the NIST CSF PR citation : Safeguards to manage the organization’s cybersecurity risks are used, the organization may implement data security, access control and platform security policies.
Once the internal organizational policies are established, control objectives are set up to implement the policies. The control objectives define exactly how to adhere to those policies and citations in the authority documents. For example: To implement the access control policy, a control objective may specify that Users, services, and hardware are always authenticated. To implement the encryption policy, a control objective may specify that the files and disks containing Personally Identifiable Information (PII) must be encrypted with industry recognized algorithms and protocols, such as AES (Advanced Encryption Standard). A control is a specific implementation of a control objective on an entity. A CRM database should be encrypted using an industry recognized algorithm is an example of a control. Encryption of another database containing customer complaints is another control.
| S.No | Key Acronyms | Description |
|---|---|---|
| 1 | CSF | Cybersecurity Framework. Provides guidelines for cybersecurity assessments. Example, NIST CSF, HiTrust CSF |
| 2 | CCM | Continuous Controls Monitoring. Refers to the continuous monitoring of Cybersecurity controls |
| 3 | ServiceNow GRC | ServiceNow IRM: Integrated Risk Management |
| 4 | Control Objectives | An objective, direction, or standard that acts as guidance for company interactions and operation |
| 5 | Entity | An Entity can be person, people, process(es), department(s), application(s),object(s),, server(s), external network device(s), data server(s), data warehouse(s) – essentially any asset that falls within the scope of compliance checks |
| 6 | Entity Type | A group of entities that have to comply with the same set of compliance standards. |
| 7 | Control | A control is a specific implementation of a control objective for each entity. |
| 8 | Indicators | Indicators monitor and assess controls to determine if an entity is compliant or non-compliant |
| 9 | CMDB | Configuration Management Database (CMDB) to build logical representations of assets, services, and the relationships between them that comprise the infrastructure of your organization |
| 10 | RDS | Relational Database System. Generally refers to the RDS service in AWS |
3. Implementing Policy and Compliance Management in ServiceNow GRC/IRM
ServiceNow’s Governance, risk, and compliance (GRC) (also called, ServiceNow IRM: Integrated Risk Management) empowers businesses to build effective governance frameworks. With the ServiceNow’s GRC framework, users can import regulations, identify policies, and establish policy lifecycles, assign, and test controls, create attestations, schedule regular tests, and perform issue and task management procedures to respond to compliance failures as they arise.
The following diagram illustrates the steps to be performed in ServiceNow to get started with Compliance Management in ServiceNow
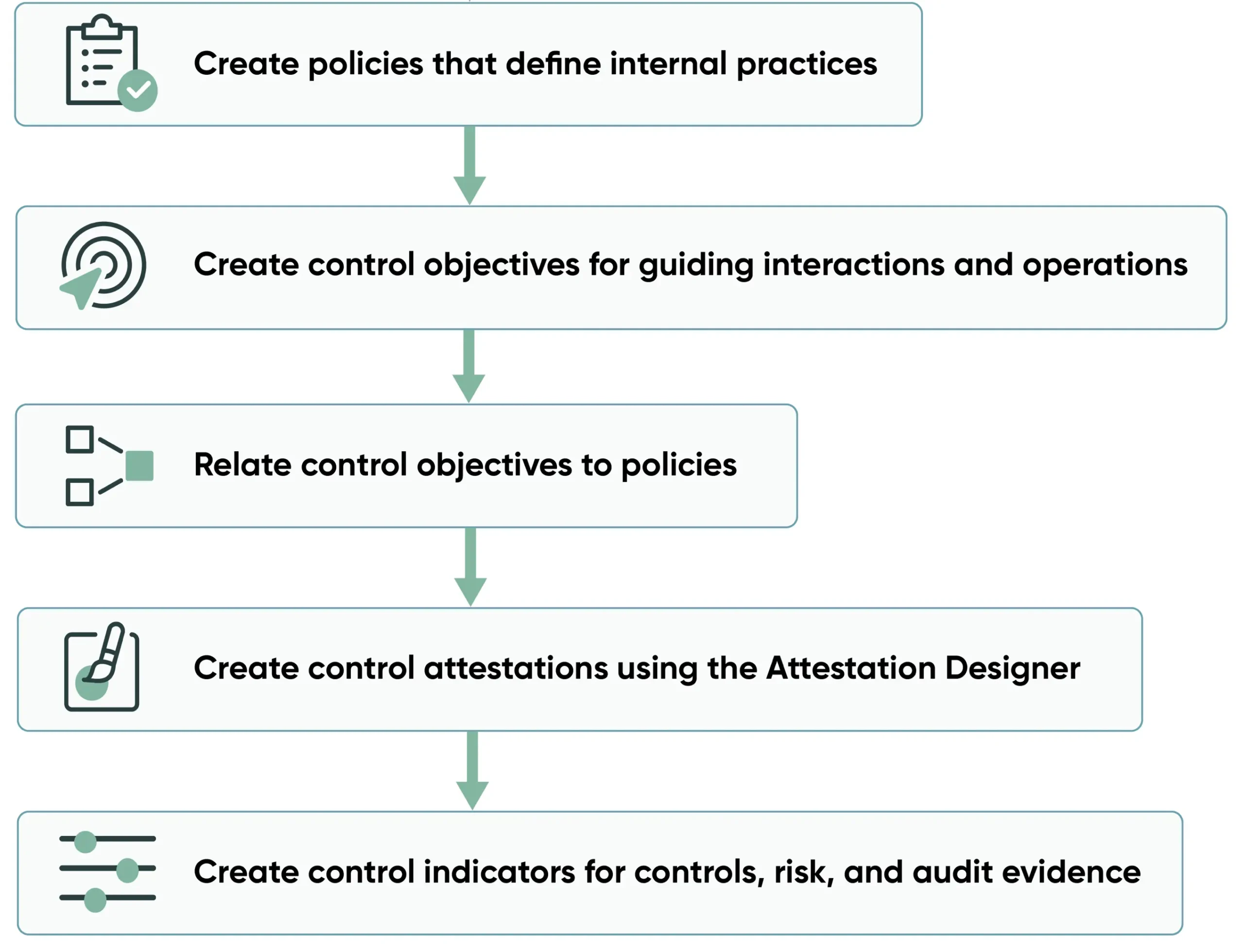
Image from ServiceNow
As discussed before, policies are internal practices that organization’s processes must follow to meet the requirements(citations) in the authority documents. Based on the policies, control objectives are direction on how to implement the policy.
Control Objectives and Requirements in ServiceNow GRC/IRM
This section describes how ServiceNow GRC/IRM can be configured for Continuous Controls Monitoring.
Control objectives are specific goals that the controls are meant to achieve. For example: To implement platform security policy, one of the control objectives could be – Log records are generated and made available for continuous monitoring
This control objectives can have next level sub control objectives such as
-
-
- Logging should be enabled
- Logs should be encrypted
- Log analysis is done periodically
- Log retention plan is maintained
- Log access is controlled
- Log file validation is enabled
-
Control objectives are often associated with control requirements. Control requirements are more granular and provide exact implementation details. They ensure that compliance with the control objective is measurable and enforceable.
For example: For the control objective, Log analysis is done periodically, the control requirement could be – System Log analysis period cannot be greater than 4 days or System Log analysis should be done by a security expert.
Configuring Entities and Entity Types in ServiceNow GRC/IRM
Entity
Entity Type
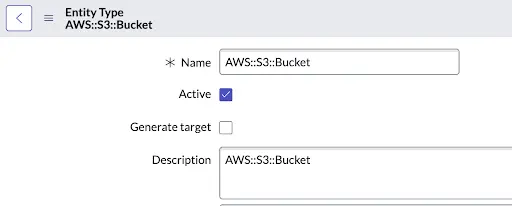
Entity type is a group of entities that have to comply with the same set of compliance standards. All instances of AWS RDS databases are an example of an Entity Type as all RDS databases need to be compliant with the same set of policy and compliance standards. Please note: An individual RDS database is an Entity in this case.
In the figure below from ServiceNow, the Entity Type is AWS:S3:Bucket (all AWS S3 buckets) and Entities are individual AWS S3 buckets.
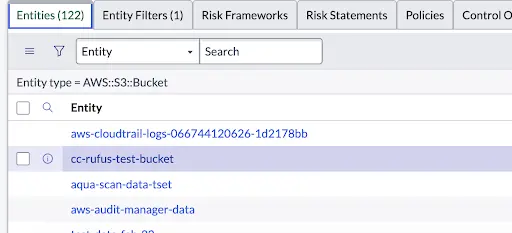
Control Objective and Entity Type Association
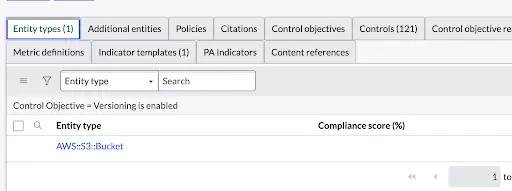
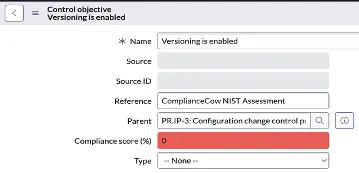
Controls
A control is a specific implementation of a control objective. Controls are automatically generated when a policy or a control objective is associated with an entity type. As a result of this association, a control is created for each entity listed in the entity type for the policy or control objective.
For example, when we associate the control objective: Versioning is enabled on an entity type such as S3 bucket, a control ‘Versioning is enabled’ is created for each S3 bucket (ie each entity)
In the figure below, we see that a control is created for each entity
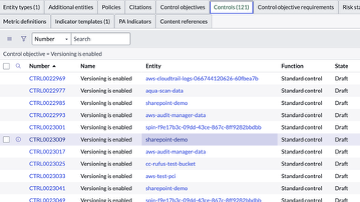
4. Why Continuous Controls Monitoring (CCM) Is Essential for Modern Cybersecurity and Compliance
Continuous Control Monitoring is an automated process that continuously assesses and validates an organization’s controls to ensure compliance, security, and risk management effectiveness. It uses automation to detect control failures, identify risks, and enforce policies without manual intervention across enterprise applications, cloud environments, and security tools.
The key benefits of Continuous Control Monitoring are
- Faster Issue Detection and Remediation
- Reduced Compliance Fines and Penalties
- Lower Audit Cost
- Optimized Resource Allocation
- Improved Decision-Making
- Decreased Operational Risk
- Improved Operational Efficiency
- Increased Customer Satisfaction
5. Implementing CCM in ServiceNow GRC/IRM
Configuring Indicator Templates and Indicators in ServiceNow GRC/IRM for CCM
Indicator Templates
In the figure below, we see that the control objective ‘Versioning is enabled’ is associated with an Indicator Template ‘ComplianceCow Dynamic Indicator Template’
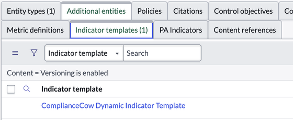

Indicator Templates are of the following types – Manual, Basic and Scripted. The figure below shows a scripted indicator
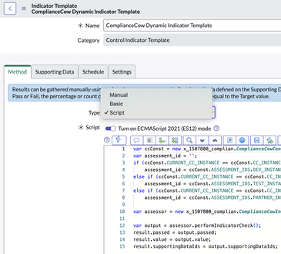
- Manual: Manual indicators are used for data that cannot be retrieved from a ServiceNow instance because it comes from an external system, such as customer data from a third-party sales system. A task is sent to the user to check whether the control is compliant, and the indicator can be marked as Pass or Fail.
- Basic: Basic indicators are automated indicators based on an indicator data source. The indicator source specifies a table and a frequency at which the scores from this table are saved.
- Scripted: Scripted indicators use a custom script to conduct the test. The data is collected automatically by the logic specified in the script. If the indicator task fails, then the control is not compliant, and an issue is created. If the indicator passes the test, then the control is compliant until the next scheduled test.
The ServiceNow’s out of the box scheduled job ‘GRC indicator nightly run‘ executes the indicators. When an indicator is run, we have the option to collect supporting data. Supporting data refers to the evidence that is collected when an indicator is run. Supporting data or information can be collected for the indicators through automatic data collection or manual tasks.
Issue
If a gap is identified while testing a control, then that gap is termed as an issue. Issues are created when a control test fails and is non-compliant.
Remediation Task
After an issue is confirmed, the organization identifies necessary steps to remediate the issue. To mitigate a risk you can create a remediation task to track the remediation work. If a triage was performed, the triage issue is converted into an actual issue or risk event. You can also track the issue as a recommendation or close it as a non-issue.
Challenges with implementing CCM through Indicators in ServiceNow
Continuous control monitoring with ServiceNow offers several benefits
- If a gap is identified while monitoring the control, an issue is reported. This issue can be shared among various ServiceNow applications such as the Policy and Compliance Management, Risk Management, Security Operations Vulnerability Response and Audit Management GRC applications providing an enterprise-wide view of risk and compliance to quickly detect effectively detect, access, remediate and correlate risk information in an integrated way across the business.
- Issue Management life cycle is facilitated by automated, cross-functional workflows for to create issues, assign control owners, triage, remediate, review and monitor the issues
- Dashboards to view overall compliance percentage and total issues, control failures by entity and policy exceptions.
Continuous control monitoring challenges with ServiceNow
However, the GRC teams still face an uphill task in implementing CCM in ServiceNow. Here are some of the key challenges:
- What data should be collected by the indicator? – Each IT asset or entity, whether a database instance or network router, generates a huge amount of real time data. The indicator has to collect the right data to evaluate the entity compliance posture
- How to access the data? – Indicators should access data from entities across geographical and cloud platforms. Data collection mechanism for each entity varies with the entity type and the cloud platforms.
- How to map the data to the required entity and control in ServiceNow – Each entity has to comply with various control objectives. Indicator has to map the collected data to the right entity and control objective to determine the compliance posture of the entity towards the control objective.
- How to evaluate and interpret the data? – The indicator should also assess whether the data fulfills the control requirements and objectives and determine the compliance status.
ServiceNow provides an open model for third party applications and data sources to integrate through methods such as APIs, connectors, custom scripts, and third-party plugins.
6. Integrating ComplianceCow to Automate CCM Workflows in ServiceNow GRC
ComplianceCow is a Security GRC Middleware providing better, contextual data to your ServiceNow GRC/IRM for Continuous Controls Monitoring. ComplianceCow integrates with complex infrastructure to perform control checks, gather evidence, analyze risks, and implement remediation measures. Customers can use pre-built assessments and controls automated for CCM for Cloud and On-premise applications, or customize or add new ones using our high-code, low-code and no-code automation studio.
For more information visit ComplianceCow, or schedule a demo.
GRC teams can rely on ComplianceCow to reconcile cloud resources with ServiceNow CMDB, conduct assessments, gather data in standardized format, create a dynamic compliance graph and ensure continuous monitoring to mitigate compliance and risks. They can also use ComplianceCow to automatically create tickets in ServiceNow and Jira, and remediate gaps, and take corrective actions.
The GRC (Governance, Risk, and Compliance) team teams can now focus on higher value functions such as establishing policies, frameworks, and standards to align business objectives with compliance and risk management, identifying, assessing, and mitigating risks that could impact the organization’s operations, security, and reputation, setting up control objectives to implement the policies, ensuring adherence to regulatory requirements, industry standards, and internal policies and educating the employees on compliance, security, and risk management best practices.
Configuring and Running Compliance Assessments in ComplianceCow
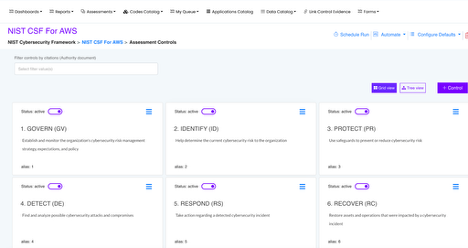
An Assessment is a collection of controls in ComplianceCow, executed for automated or manual evidence collection, evaluated for compliance. Users can run assessments on-demand or schedule as needed or simply invoke them through an API call. Users can use any of the pre-built industry assessments such as NIST 800-53, CIS Controls v8, PCI-DSS 4.0 or can build their own custom assessment.
The following figure shows a NIST CSF 1.1 assessment configured for AWS. The controls are nested, and each “Leaf” control maps to the control tied to the control objective in ServiceNow.
Assessments in ComplianceCow are run by providing the following information:
- Scope of assets (infrastructure, applications and services)
- Control period for which the controls are assessed
Automating Evidence Collection in ComplianceCow
An Assessment can contain manual, semi-automated or fully automated controls.
- Manual controls only rely on users to manually provide inputs and evidence for assessing the controls
- Semi-automated controls collect data from SYSTEMS and present them to humans-in-the-loop for review and approval. Once the workflow reaches finality, evidence for the control is created and is evaluated for compliance.
- Fully automated controls collect data from SYSTEMS and do not require human-in-the-loop feedback.
ComplianceCow supports all 3 types of controls. For the purpose of this document and CCM, we focus on fully automated controls.
In fully automated controls, ComplianceCow generates evidence data in standard and extended formats
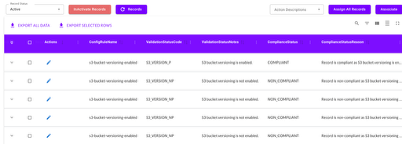
- The Standard Evidence presents compliance data in standard, uniform format irrespective of the type of assessment, entity or cloud platform. The Standard Evidence also contains other contextual data such as entity location, url and other metadata to enrich the compliance data. This enables GRC team members to apply rules to determine compliance, irrespective of the underlying entity: technology or infrastructure or application.
- The Extended evidence presents raw data collected from the entity. This evidence format is dependent on the type of entity, the data source and cloud platform. This data is useful when the GRC team wants to deep dive into the entity’s setup to investigate and triage a non-compliance issue.
The figure shows the standard evidence generated by ComplianceCow for AWS S3 bucket versioning.
How do the Control Evidence files from ComplianceCow integrate with ServiceNow GRC/IRM Indicators for CCM?
The following steps outline how ComplianceCow evidence is collected, mapped, and pushed into ServiceNow to drive automated indicator evaluation and issue lifecycle management.
- A custom scheduled job in ServiceNow triggers a pre-configured assessment in ComplianceCow. This job can also be run on demand.
- The ComplianceCow assessment connects to the entities and gathers required data to check for the entity’s compliance to the control. It also contains the metadata for the ServiceNow Indicator to map the compliance data to the required entity and control, and evaluate and interpret the data
- Once the ComplianceCow assessment ends and the evidence files are generated, ComplianceCow Platform API Service for ServiceNow pushes the evidence data to the custom tables in ServiceNow.
- The ServiceNow’s out of the box scheduled job ‘GRC indicator nightly run‘ executes the indicators.
- Script based Indicators read data from the ServiceNow’s custom tables populated by ComplianceCow
- ComplianceCow provides a custom indicator template that maps custom entity data to the appropriate control objective and requirements and determines the compliance status of the control.
- The ComplianceCow indicator communicates the compliance status of the control to ServiceNow.
- ServiceNow creates an issue upon a control failure
- If the next ComplianceCow assessment indicates that the failure has been remediated, then ServiceNow declares that the control is compliant and automatically closes the issue.
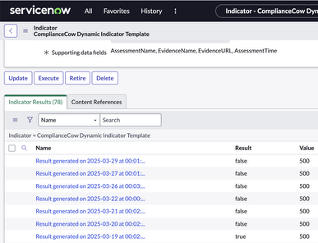
The following figure shows indicator results for each assessment in ComplianceCow.
NOTE: Indicator is attached to each entity. In this case, the figure shows the assessment result for the control test : Versioning in enabled for a specific S3 bucket
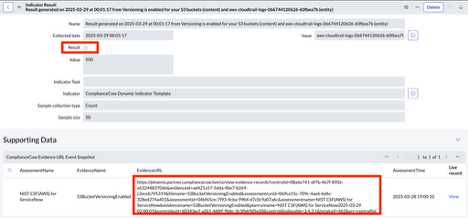
Customizing Indicator for Control objective
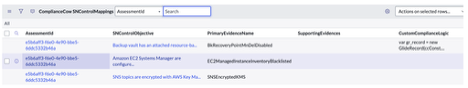
Customizing Supporting data for Control objectives
In such cases, the evidence which has the Complaint Status and Compliance meta data is configured as the primary evidence and the other evidence generated for the control can be configured as the supporting evidence. In such cases, the primary and supporting evidence are together displayed as links in the Supporting data section for the Indicator results

7. Closing Summary: How ComplianceCow Extends ServiceNow GRC for Scalable Compliance Automation
ComplianceCow is a ServiceNow Build Partner, and can help you maximize your ServiceNow GRC/IRM investment by making it super easy to automate IT and Security controls for GRC, and to continuously monitor them on an ongoing basis.
ComplianceCow integrates with 100s of Cloud Infrastructure Services and Applications, and allows you to easily customize existing automation or build net new ones for your On-Premise Applications and Services as well.
Your GRC team no longer has to herd emails to manually collect, curate and upload evidence into ServiceNow. ComplianceCow does all the repetitive evidence collection and controls testing tasks, so that you and your team can focus on higher value functions such as analysis and remediation.
ComplianceCow, through its unique Compliance Graph and Large Language Model and GenAI integration, allows your users to become significantly productive with analysis, remediation and response of your Cybersecurity Risk, Compliance and Governance estate.
Appendix: ComplianceCow Architecture and CCM Workflow Diagrams
– A – ComplianceCow Architecture and CCM Workflow Diagrams
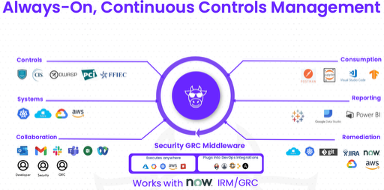
This architecture diagram shows ComplianceCow as a Security GRC Middleware
It integrates with:
- Security controls frameworks (CIS, OWASP, PCI, FFIEC)
- Systems (AWS, Azure, GCP, Kubernetes)
- Collaboration tools (Slack, Teams, Gmail)
- DevOps platforms
Outputs flow to:
- Consumption layers (Postman, VS Code, Jupyter, TensorFlow),
- Reporting tools (Power BI, Tableau, Google Data Studio),
- Remediation systems (Jira, ServiceNow, Git).
The diagram highlights ComplianceCow’s ability to execute anywhere and plug into DevOps workflows, while working natively with ServiceNow IRM/GRC.
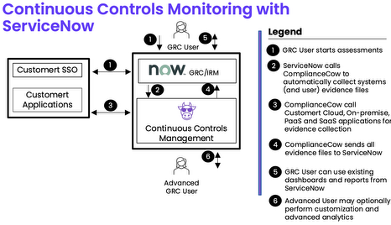
This architecture diagram shows ComplianceCow as a Security GRC Middleware
The process shows a GRC user initiating assessments in ServiceNow, which then calls ComplianceCow to collect evidence from customer applications (cloud, on-prem, SaaS, PaaS). ComplianceCow sends the evidence back to ServiceNow for compliance reporting. Advanced users can perform customization and analytics. Labeled steps include GRC user actions, system interactions, and evidence routing between platforms.
Appendix – B – ComplianceCow Powering Agentic Security GRC for the Enterprise
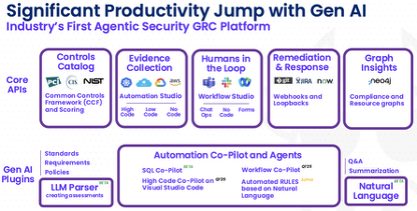
This Platform Architecture diagram shows ComplianceCow’s capabilities across Core APIs and GenAI Plugins
Modules include:
- Controls Catalog with Common Controls Framework (CCF)
- Evidence Collection via Automation Studio (high-code, low-code, no-code)
- Workflow Studio for human-in-the-loop collaboration
- Webhooks for Remediation and Response
- Graph Insights using Neo4j
GenAI components include:
1) An LLM Parser for standards and policy ingestion
2) Natural Language Q&A and summarization
3) SQL and Workflow Co-Pilots
4) Rule automation agents based on natural language input.
Designed for integration with Visual Studio Code and chat-based DevOps environments.