🚀 Welcome to the premiere episode of Security & GRC Decoded! Host Raj Krishnamurthy sits down with Mosi Platt, Senior Security Compliance Engineer at Netflix, to explore his unconventional journey into cybersecurity, governance, risk, and compliance (GRC).
🎙 What You’ll Learn in This Episode:
✅ Mosi’s unique path from IT audits to Netflix
✅ The biggest myths about security governance
✅ Why risk quantification remains a challenge in the industry
✅ The impact of SEC cybersecurity materiality rules
✅ How to shift from risk-based to trust-based security
✅ Strategies to convince executives to invest in GRC
🔹 If you’re a security leader, compliance professional, or tech enthusiast, this episode is packed with insights to help you navigate the evolving GRC landscape.
🔔 Don’t forget to LIKE, SUBSCRIBE, and TURN ON NOTIFICATIONS for more expert insights on security & GRC!
💡 Want to elevate your GRC game? Learn more about how ComplianceCow helps teams navigate security compliance efficiently!
⏱ Timestamps:
0:00 Introduction & Host
0:38 Mosi’s Journey (IT Training to Security Consulting)
6:50 Early Career in Compliance (IT Audits)
10:44 Defining Security & GRC (3 Pillars)
12:38 Myth of Security Governance (CISO Oversight)
14:48 State of GRC Today (Risk Quantification & SEC Regs)
19:30 SEC Cybersecurity Materiality Rules
24:12 Adapting GRC Strategies (People, Process, Tech)
30:10 Building a Security GRC Program (ISO 27001 Steps)
35:00 Risk-Based vs. Trust-Based Security
41:55 Getting Executive Buy-In (Truth vs. Fear)
45:28 Inheriting a GRC Program (Evaluate & Optimize)
49:17 Future of GRC & Digital Transformation
52:37 The Perfect GRC Solution (Automated Compliance)
56:00 Recommended Books & Podcasts
58:30 Final Thoughts & Key Takeaways
📢 Guest Contact Information:
👤 Mosi Platt – Senior Security Compliance Engineer, Netflix
🔗 LinkedIn: https://www.linkedin.com/in/mosi-k-platt/
📖 Books Mentioned:
📌 Investments Unlimited by IT Revolution → https://itrevolution.com/product/investments-unlimited/
📌 Emergency Skin by N.K. Jemisin (Audiobook) → https://www.audible.com/pd/Emergency-Skin-Audiobook/1978650841
🎧 Podcast Recommendations:
🔹 Enterprise Security Weekly → https://www.scworld.com/podcast-show/enterprise-security-weekly
🔹 Cybersecurity Where You Are → https://www.cisecurity.org/insights/podcast
🔗 Additional Resources:
✅ FAIR Risk Management Framework → https://www.fairinstitute.org/fair-risk-management
✅ ISACA Digital Trust Framework → https://www.isaca.org/digital-trust#1
✅ OSSTMM Security Testing Methodology → https://www.isecom.org/OSSTMM.3.pdf
🔥 Subscribe for more Security & GRC insights! 🚀
Introduction & Host
uhhuh uhh [Music]
hey welcome to security and DRC decoded I’m your host Raj Krishna morti I’m here
Mosi’s Journey (IT Training to Security Consulting)
today with the awesome mosy plat MOSI plat is 22 plus years in security and GRC industry and he’s currently a senior
security compliance engineer at Netflix MOSI welcome good to be here Raj You’ been
talking about this for a long time so it’s good to uh finally get it started thank you mosy and let’s get let’s
decode so mosy I want to start off was um maybe talking about you how did you start with security and GRC and what has
been the journey so far sure so it’s uh it’s a little bit of
a convoluted story but I’ll try to give you the short the short version so my um
I got first exposed to computers by my uh Aunt who was the first uh computer
teacher for the public school district in Trent New Jersey and so uh
she was the first and so she knew a little bit about computers from college uh but she didn’t really know much so
they gave her computers that she could set up in her own home lab so she could prepare her curriculum and her lesson
plans and she would use her her children and her nephews as her first test students so got exposed to that in
around 1984 and then uh moved to Arkansas uh my
father was in the Air Force so he was stationed in Arkansas and that was around the time that Bill Clinton became
governor and so Arkansas had one of the worst Educational Systems in the US at that time so he it was a big focus of
his campaign and his platform and so the elementary school that uh I was in also had a computer lab
in the gifted and talented classroom that was the only classroom that had it um and so I happened to being gifted and
talented and so got to you know learn basic continue learning basic there um
and play around the computer so that’s how I got exposed to it as a kid and then when I got older um I was
far removed from computers and uh I was working in a grocery store actually and my aunt’s
husband my uncle called me and says you’re not going anywhere in your life working in these Grocery Stores um this
was post 9911 and so he said uh you know country’s in a recession the government is trying to get out of it by training
IT workers you should get in this it training program and have an IT career
and so I I enrolled in the program in New Jersey it was being offered out of the merca County Community College it
was called the New Jersey It Centers uh enrolled in that and I was still working overnight at the grocery store and so I
would normally sleep through the first one or two classes uh because I had been up all night working and uh for the
security track uh it was split into two parts and the first part it was the first class in the morning and so I’m
sleeping trying to sleep in the back of the classroom and the instructor is asking a Class A question and he’s a
loud talker um you know him it’s John VAR from Pivot Point Security and
nobody’s answering the question every time he repeats it he says it louder and I just I can’t sleep because he’s so
loud so I answer the question so that he could just bring his voice down to a normal level so I can you know get my
rest for the rest of the day and so I answer he says oh wow I can’t believe you answered it correctly because you’ve
been sleep this whole time and so then he just walks over to my side of the classroom and just asked me every
question after that for the rest of the class and I can’t go back to sleep so from there we ended up hitting it off
and um when I finished the program in six months he uh offered me a job in his
uh information security consulting firm um which was called Pivot Point Security
so that’s how I got into it it was really just a a string of coincidences um interesting and so when
I joined I only had I was trained in Windows 2000 Network Administration so
and then I had a you know two security classes from John Barry I wasn’t really um going to be somebody you could
send out and build at a you know a high rate for a consulting firm so my first
few projects were related to like building out little you know networks for um small mediumsized businesses and
nonprofits um but why John hired me was because he had was getting a lot of work
from these nonprofits he had partnered with his brother-in-law whose CPA firm
they only specialized in um Catholic or religious
nonprofits uh Indian reservations and um fire
districts and so the aicpa back then had passed this new uh statement on
accounting standards that said that uh all Financial audits had to include an
assessment of it risk and and previously the CPA could just say that they assess
it as a maximum risk but the new standard changed that um where they actually had to do an audit of the it to
support their uh it risk assessment and so he partnered with John VAR and Pivot
Point to do that for his financial audits that his CPA firm was conducting so John was getting all this audit work
that he could no longer manage by himself um and so he brought me in to either help him continue growing the
security work for the business while he did the audit work or for me to eventually get into the audit work to
support that and so um those weren’t even really there was some security aspect for that but they were integrated
audits with financial audits so they were more like it audits um like how are the financial reporting systems um are
they configured properly to ensure the Integrity of the financial
reports that were being filed so that’s how I got started and uh
so we started with these big Catholic nonprofits and from there it was easy to
continue billing me out because I had experience from these this it was a low-risk environment like I remember
like John tells a story about one of his first audits with one of these nonprofits um he’s asking the CIO he’s
Early Career in Compliance (IT Audits)
going through like the security section of the audit and the CIO is just failing miserably like he can’t answer any
question this is back in like 2002 and uh then John hits a question asks
him about intrusion detection systems and the cio’s face just lights up he’s like oh oh oh yeah yeah we’re good there
we we have intrusion detection and John is stunned because like they didn’t have a firewall they didn’t have any access
control setups he’s like oh okay cool what do you have for your intrusion
detection system and the CIO responded we have ADT for intrusion detection
that’s and that’s gen was like oh man this is as bad as I thought so it was
really lowrisk environment to learn in um so it was great but having the experience with these uh integrated
audits with the financial audits when sarban Oxley got passed after the Enron Scandal it was easy to Pivot to doing
sarban Oxley it AIT work so I got into sarban Oxley it GRC I got into itgc that
way with sarban Oxley um for public companies uh because we had a client
who um they had ernston young that was doing their external audit but they
didn’t they didn’t have any it audit capabilities within their internal audit function they didn’t even have an internal audit function they outsourced
their internal audit and the internal audit from they outsourc to didn’t have it audit capabilities because you know
it was still new back then so um so they brought us in to do the this was when
you at at Pivot Point still yeah it’s in pivot Points this is 20 now we’re in 2003 okay um so that was my first
exposure there uh to doing like a really big it GRC project um and then from
there like sing oxy came out then PCI DSS came out and so this same client
that we did the sing zxy work for they um they owned a bunch of hotel properties um like they were real estate
investment trust and they manage these hotel properties um as part of the as
another part of the business and so when PCI came out they were like hey well we also got to comply with this PCI Data
security standard that’s new and so then I get into the security audits from or assessments from the PCI standpoint and
that that was my first uh security GRC project was pcidss compliance and then
from there you know building up uh reps of doing that for a couple years and then it expanded John had the vision
that hey you know it growth is booming all these uh companies need to provide
Insurance to their customers um and so they’re only going to have the two main ways to do that sock 2 and ISO 27,1 and
that was this is around the time like Thomas Freeman was publishing articles and books about the World is Flat and so
John’s like he thinks the sock 2 is going to be is not going to be sufficient if these comp if the world becomes flatter and so in order to
provide Global Assurance these companies are going to have to start pursuing ISO 270001 and so I pivoted into ISO 270001
and bu built out the the Pivot Point practice for that um you know like John
started started it with like the first two audits or helping the first two clients get prepared for a certification
audit and then I kind of took it over and built it out from there so that’s how I got into security GRC got it
that’s the long conv that’s a fascinating story um I’ve been on John’s podcast as you know but I did not know
this backstory that’s a fascinating backstory from a sleeping student to an IT Auditor to a security GRC auditor and
potentially inter Assurance I mean that’s a fantastic story and I stayed in GRC cuz when I was doing an audit John
said well when you going to try pentesting and I was like sure I was done with the audit work so I tried to pinest one of the clients and I was
terrible at it like I think I got something from like a I found a password
Defining Security & GRC (3 Pillars)
for um I found a password for one employee until I got into their email and that was it it was all I could do
after like six hours so I was like this is this is an awful experience house stay GRC side so mostly I I wanted to
sort of um so Security in GRC looks like it means many things to many people
right why don’t we decode that a little bit what is your definition of security and GRC security GRC can you talk
through us a little bit sure so my security definition is pretty vanilla
and straightforward um especially like when we talk about information security I’ll focus on that
um it’s the confidentiality integrity and availability of information uh very simple that’s what John taught me I
stick with it to the day that’s how isaka defines it so um that’s how I that’s what information security means
to me um the GRC is uh well everyone knows I
think it’s short for governance risk management compliance management and I think uh the governance
part I think a lot of people get they either get confused about um or they
misuse use it to serve their own purposes um and so you know governance
at a very simple level uh is just the evaluation Direction and monitoring of
Enterprise strategy right that’s that’s a really simplified version of the definition from
isaka um risk management is the identification
analysis and treatment of the probable frequency and magnitude of future loss
so that’s my own hybrid definition I’m kind of mashing up ISO 270001 definition
with a fair definition of risk management and then uh compliance
Myth of Security Governance (CISO Oversight)
management is really simple it’s just ensuring the adherence to relevant requirements and so you know the
Enterprise determines what requirements are relevant and so that would be part of compliance management that identification of what requirements do
we care about do we want to provide Assurance against um got it and then just demonstrating
that you said something very interesting you said governance many people misuse I
don’t know did you say most people misuse what do you mean by that can you double click on that so like you know
governance is something that comes from it’s top down and so you know there’s a lot of
discussion nowadays about uh how do cesos get to sit at the at the table with the board or with the you know
cesos have seen the title but are they really part of the SE suite and so you hear things about like security
governance but if the security Executives don’t have a seat at the
board or the board isn’t really um evaluating directing and monitoring
security strategy that’s that’s not really security governance and so people talk about security governance at a lower
level like from the Security executive down and and I know like the the iso
standard 27014 makes space for that but it’s not what it’s not governance in the
s in the traditional sense and how it’s really thought of in in a corporate sense right it’s not a governing body
right that is overseeing the management of security um when most people talk about security govern that’s not that’s
not how it’s that’s not how it’s discussed um because the governing body security Executives don’t really have a
lot of access to or or the governing body doesn’t provide that much oversight
to the security Executives okay so the way you described it if I were to rephrase governance is
about managing the percent risk management is about potenti managing the potential future and compliance is about
reporting is that a fair categorization the only the only thing I would change
on that is you know isaka does a very good job of distinguishing the
State of GRC Today (Risk Quantification & SEC Regs)
governance and management are separate processes yep right and so I wouldn’t so
just that just because of that I wouldn’t include Management in the definition of governance um cuz that
that could lead to confusion got it got it so what do you think is happening in
the security GRC industry today it has been a very mature industry right but what what what is your take on it MOS
what what do you see happening so I think we kind of touched on part one big problem I think one big thing that’s
happening is this security governance being more myth than reality I think there’s a lot of aspirational security governance where you know people talk
about cuz you know they say like work for the job you want not the job you have and so I think that kind of
influences a lot of what’s going on with security governance um people want to
uh they want to have a seat at the board or they want to be on the board right or they want to be in that se Suite um and
so they talk about security governance if it’s really happening that way even though it’s not so it’s more
aspirational uh that’s one thing that’s happening I think on the risk you know security risk management side I think
there’s a big struggle to evolve the state-ofthe-art from qualitative to
quantitative analysis so you know I mentioned I had my own like hybrid definition that you know mashes up ISO
27,5 and uh Fair um but that’s so that’s kind of even
exemplary of that um and so I I don’t know I I hope it’s going to resolve in
that we get the state-of-the-art consensus for quantitative analysis but I like I’ve talked with with vendors or
or even standard bodies that are ambivalent um or they don’t
know how the the smoke is going to settle on that Battlefield and so they’re just kind of waiting um before
they move forward um to see which way it goes and then uh and then you can even
see debates on uh LinkedIn like once you become like a fair member or you start following the fair Institute online you
just get all of these debates in your feed of people you know taking shots at
quantitative risk analysis or you know or it’s adherence like you know uh or
even creators or thought leaders like Jack Jones or The cenia Institute right
um or Doug hubber and Richard cson right and so it’s it’s a really it’s still
contested it’s I don’t think that debate has been settled yet and then on the uh security compliance management side it’s
undergoing digital transformation um but it’s a digital transformation that lags behind the digital transformation that
it and Engineering went through right in the last decade got it no you I think you’ve
talked about do you think the new cyber security SEC materiality rules put
greater emphasis on quantification on the this
quantification yeah so you
know I would have to say no because they explicitly state that you can’t just use
quantitative analysis to meet the requirements right um and so I I would
say they don’t but that hasn’t stopped uh risk quants from trying to leverage
it and capitalize on it um so like Fair came out with the fair materiality assessment model specifically intended
for compliance with the SEC materiality rules yep um but the rule itself is very
clear right like there was that’s another example of the debate right they was the debate about that when they were
working on the ru making and they settled on the final language that doesn’t stipulate quantitative analysis
um so so you’re still you’re saying that it’s still very subjective it has qualitative and quantitative aspects to
it yeah and you know and I understand PRI like there’s I you can’t just have a purely
quantitative uh analysis um for things like that right there’s qualitative aspect to the there’s qualitative
context that needs to be considered or to put the quantitative analysis in the context you need qualitative assessment
right or you need to look at qualitative results um so you know the SEC was kind
of in a tough spot there but I think the industry or the practitioners let me not
say the industry um the practitioners need to come to a consensus best practice on how those two go together
SEC Cybersecurity Materiality Rules
and I think that’s the tension that’s unresolved got it got it so I think you talked about some of the challenges with
security governance security risk management security compliance how in your view how do you
think the the security and GRC teams and the practitioners should react and adapt
to these changes or to these to these new challenges
so you know I try to I try to think about these things in terms of know people process
and technology and then it goes back to my training with John VAR um and so I think from a people
standpoint I think the professionals have to be versatile right and and by
versatile I mean they need to have a well-rounded skill set that covers you know governance risk management and
compliance management so they’ve got to understand governance they’ve got to understand you know quantitative risk
analysis and be able to put it in a qualitative context um they’ve got to understand how
to identify relevant uh requirements that not only create value not only I’m
sorry not only protect the value of the business but also create value for the the business or the organization right
that they’re working for or supporting um so that versatility I think is is crucial
and uh another part on that compliance management skill set is you know it’s Harmon izing internal and external
requirements right like how do we make an external requirement relevant internally and how do we make an
internal requirement uh relevant to external stakeholders uh from a process
standpoint you know I think it’s given
the problems with security governance you know being a little bit more aspirational than uh than reality a
concrete reality um and security governance is a big input to the risk management and
compliance management I think like any uh it or technology problem input
validation becomes crucial right like if your requirements are coming from security governance but you’re getting
bad security governance output you’ve got to make sure you distinguish the bad output um from the good output so that
you can actually create a relevant security program a risk management compliance Management program
um so that’s that’s I think that’s key um and then you know maybe even and I think
what ends up having with a lot of Security Programs is when you are providing your own governance input
because you aren’t getting it from a governing body to provide it um like who
who checks the Checker right like like if you’re if you’re self- serving your your governance well who’s saying
whether or not that governance is appropriate um and I think that’s another big problem with security
governance is being so immature right now um so imput validation right like somebody may have to tell the Security
executive that you know I have a colleague that uses this phrase a lot that their baby is ugly like hey this
strategy is no good um and then uh devops I think you know I
mentioned the security compliance management going undergoing a digital transformation I think we know devops
was a great tool for digital transformation um last decade um and I
think it needs to be just as vital a tool this decade for security compliance which means you know security compliance
got exposed to it in the last decade is they were trying to figure out how they could provide Assurance with this new
this new mode of operating uh but you know I used to have a saying when I was
a consultant like those who can do those who can’t teach and those who can’t teach
audit and so I think compliance professional need to make that transition from being able to audit
something to being able to do something when it comes to devops and I think that is the tough part of the digital
transformation security compliance right now and then from a technology
standpoint I think uh security compliance or security GRC programs they
need they need flexible platforms they can work on um because they have to cover the three lines right uh they’ve
got to cover the first line the second line there first line would be the operators the second line would be the
compliance professionals who are evaluating the output from the operations teams um to make to hold them
accountable and then the third line is providing Assurance to the the stakeholders right at the governing body
level which would be your board uh your executive management your external
Adapting GRC Strategies (People, Process, Tech)
stakeholders uh and those three lines work very differently right like first line is in the weeds second line you
know they have that 10,000 foot view you know tend to be more Jack of all trades know know a little about a lot um and
then the third line is very focused right they only care about what they need to care about like what do they
absolutely need to trust for the decision that they need to make with the Assurance they’re given and that’s all they care about um and so because of the
those different approaches is how they like to work in the GRC with GRC information is very different and so the
platforms need to be flexible enough to allow that got it got it so if if somebody
were to ask you how do you build a security GRC program today and add Assurance to it right how
would you build a program today then what is typically being taught or what is the common know what would your
answer be to that so my My First Response might be is
probably be like a muscle memory like a reflexive response um because I I did it
so much when I was a consultant and so it’s and it’s still my default um and so it’s really just a
simplified version of the the management processes that they outline in ISO 270001 standard and so the way I
simplify it is you’ve got to have for any any security GRC program needs to
have these seven simple business processes in order to provide assurance and build trust with stakeholders right
so you got to have context um so you got to understand what you’re securing and
why secondly you’ve got to you got to have
leadership right you’ve got to have a vision so of okay this is the thing we’re trying to secure how should it be secured right in
order to satisfy our why and so you know that typically gets expressing things like you know uh
security policies uh allocation of roles and responsibilities and things like that
right so now you know what you need to secure you understand how it should be secured
then you come in the next process which is planning which is
um how do we implement this vision for how we should secure our
information and right now where we are in our state of practice it’s uh it’s
typically risk-based planning right um I think that needs to evolve to be uh
trust based planning but there’s we’re immature in that we don’t have good um
we don’t really have a consensus best practices for doing that right now um so that’s that that that’s something that’s
in development but you’ve got to have either risk-based or trust-based planning process that identifies what
your objectives are for implementing this vision of security once you have your planning
your next process is support what do we need to have in place to execute this plan for the security GRC program right
and so that needs to cover things like what resources are required um for the people that are going to be executing this plan what competencies are
required uh what awareness do the stakeholders need to have of this program as we execute it as we execute
this plan uh what communication needs to be in place to keep the practitioners
and the stakeholders in sync and then what documentation or you know do we need to have as as records so everyone
can at any time come and get the information that they need as we ex as to execute this plan
you’ve got that in place then you can get into the operations of it this is simply the execution of the plan right
you know what you need to do to implement the security Vision um You’
got the re you got the support in place to execute it and now just go executing it right and that’s just your standard
project management yep right um after you your operation
process you have to have a performance evaluation process that says Hey how well did we do implementing this vision
for a security GRC that was set by leadership and then the final process is
Improvement which says where you fell short of implementing the vision you
have corrective actions or continuous improvements to close that Gap um and
then if things changed in the context from the time you started executing the plan to the time you did
your performance evaluation well what improvements do we need to make or changes do we need to make to account for the changes in
context and those are and then you know those seven processes are you know cyclical and uh sometimes they run in
parallel but if you have those seven processes I think you can uh you can build out a pretty
effective security GRC and insurance program
um and I think what one thing that’s different we already talked about is you
know we should try to shift from a risk-based plan to a trust based
plan um so and I maybe actually I’ll explain why I think that’s an important shift that needs to be made yep I think
think what really got me thinking about I was always thought about this there’s this open source security testing
methodology manual from uh Icom and Pete Herzog and so in uh I want to say it was
probably version three or four they introduced these trust principles into
the the uh Austin and and I thought it was
fascinating and then they came up with a trust score and the way they articulated it it made
so much sense like because Assurance is about trust but we focus on when we F focus on
risk the risk side of it we’re focused on making people we’re building people’s trust by giving them assurance that the
Building a Security GRC Program (ISO 27001 Steps)
bad things that can happen are diminished sufficiently diminished right or
controlled as opposed to tell them what which is kind of an indirect way of providing uh TR building Trust whereas
why not just have a direct way of building trust by hey what do you need to trust this
output and tell you whether or not that what you what you need is what you got um interesting and so and I think
that becomes really important now with artificial intelligence right
because if AI if like like so with these Genai models right
um if the large language models or the neural networks operate in sort of a
black box and it’s not really understood how the output is
created right but we need to trust the output well trying to focus on uh a
risk-based approach to that could be a never-ending
exercise but we can absolutely enumerate what we need to trust the output can you
can you elaborate on that why do you think it’s going to be a never-ending exercise well I mean because in order
if it’s if it’s a black box if you’re getting output from a black box how can you enumerate all the risks you won you
don’t know right right um and so it’s it
becomes to me it becomes insufficient got it um from a Security Management
standpoint right like you’ll never really know if you did a good job managing the risk um and so that puts so
how can you how much insurance can you provide right right they I think it’ll always be questioned um whereas if you
take that trust based approach and you just start with this is what I know I need to trust it and you can debate
whether or not that trust is whether you set the right level of trust right but that’s on the stakeholder not on the
trust provider right um so I I think it becomes more management I think it
becomes more realistic um and then the other thing I think that gets lost
when building out security gr building out or operating security GRC programs
is uh value creation I think it’s lost you know we Security in general tends to
over index on value protection um but uh
you know no business survives on protection alone right at some point the business needs to create value to
survive and security is no different um if security is not creating value
uh then at some point you know and sometimes you know some Security Programs struggle with this now right they be find themselves just you know
finding it hard to justify their existence right or at the very least their budget right um so you’re finding
ways to focus on value creation like and that and that goes back to that context process of understanding the why right
and if that why that that why needs to be focused on both value creation and
protection and if you have that then it should be easy Downstream to focus on value creation throughout those other
six processes got it and by value creation do you mean both internal and external so for example custom Val right
how do you create value for for all the stakeholders right and like I think a stakeholders in I got this from um
Harvard Business Review but you know you have uh sh you
know stakeholders could be you know shareholders right would be one set of stakeholder um the communities that the Enterprises
operates in is another set of stakeholders the vendors and partner ecosystem that all Enterprise need to
deliver their services uh would be another stakeholder the employees themselves is uh is one set of
stakeholders and then uh the fifth one I am drawing a blank on oh is the right
the the governing body right the board right the in in the executive management
so um oh no I’m sorry I left that customers
customers is the one that I left out um and so how do you create value for all those
stakeholders right um so because if you if you’re internal employees if you’re not creating value for them why are they
going to keep working to deliver the services to satisfy those external stakeholders right so I think you have
to have a balance got I think those are very interesting insights M trust BAS and not
just risk based I think there may be an intros section but your point is fundamentally shift your perspective on
Risk-Based vs. Trust-Based Security
how you how you want to manage the security GRC program two is focus on not
just value protection um which even then sometimes is very difficult to articulate today but Focus also on value
creation and not just for internal stakeholders but also for external stakeholders I think that’s brilliant uh
do you have any insights in terms of you know how you would go about sort of thinking about that TR based risk based
and value creation
so for trust based risk base um the trust based side is still immature um
but it is developing like isaka came out with this digital trust uh framework uh
I want to say two years ago uh they launched it and so I think that’s a start um like
you know the the OSS TMM has their uh trust assessments that they’ve created
um but I I don’t think we’ve gotten to like a set of consensus best practices yet and and I think both of those things
were created um while created to be flexible um we I don’t think we have
enough um I don’t think we’ve had enough practice yet to determine if they hold
up when applied to artificial int Ence right like are they actually giving
are they actually valuable in creating trust in these systems and these processes um that we need so I think we
need I think we need just need more time to apply apply them um and then fine-tune them right and improve them so
that we can actually get to some consensus um on the trust based versus the risk based thing but those are those
are the places where I would start um if I wanted to to apply a trust based approach God I I think those are
fantastic insights M and I think one challenge I think anybody listening to this program is going to be how do I get
the money resources time budget and all this right so how do you go about
convincing the Security leaders and Executives right on on how to go about
such a program any any advice on insights there how do you build a business case
yeah you know I think the first thing I always go back to when
it comes to building a business cases you know and this may seem very basic and simple but sometimes uh well you
know they like I have some family say common sense ain’t ain’t always common but uh is lead with truth and not
hyperbole um and I I learned that lesson a hard way uh in a Consulting engagement
we were Consulting for a um a municipal agency that uh they handled uh they were
the they provided the financial services for the municipality so they handed the financial service the fintech for the municipality right all the financial
services technology this agency was responsible for and so they were um
replacing the uh the financial management system for for the
municipality um and so uh we did a we came in and did
a security assessment of it in including a pintest um and the pintest we got root
on at every level of the stack um and in my in my compliance my
controls assessment I found like big- time deficiencies in the change management process and so we’re writing you know I
write up the audit report I had just gotten my uh cisa my certified Information Systems auditor
certification from my saaka and I so I’m fresh out of the classes and so every I’m cesa by the book and one of the
things they teach you is purpose of the audit report is to shock management into
action and so I write this inflammatory Auto report like and I had like even
even the fonts for each section they were like 24 Point fonts for for the section headings just to shock
management into action and so um John tried to tone it down a
bit um but you know I’m hitting him with you know cesa uh practice book chapter
and verse and he’s like okay all right all right we’ll try it we’ll try it and
um and even the contractor that brought us in because we were subcontracted they looked at it and they were like hey I
mean look the guy’s got a point I mean like look you had root on the admin desktops like this the system was owned
from in to end like this maybe this is what it needs to be and so we go into the meeting and
somebody at the at this ass the executives in this meeting opens up the report before the meeting starts and
flips to the table of contents and says oh this is going to be a fun meeting and
then someone else says you think the first page of the table of account is interesting wait till you see the second
page and uh and then one of the uh key stakeholders turns to the executive for
the agency I’m sorry the executive for the agency turns to one of the stakeholders uh for the project um the
one that was actually funding it and said you set me up because they’re the ones that brought us into the assessment
and so the meeting went terribly so after the meeting like it’s me it’s John
and it’s the uh the the uh the project manager who brought us in we’re sitting
and we’re having like Glenn levit Scotch to come up with a rescue plan like how do we rescue this engagement and uh I remember he the
project manager um wrote down on the napkin at this bar Glenn livet rescue or
Glenn livet plan um we sketch it out but and and it worked we ended up you know
getting things back on track they they ended up not kicking us out and they kept bringing us back for more work and
when I came in for the second engagement I was really nervous because I hadn’t really seen anybody since the first one you know had like kind of went down in
flames in that meeting um they got hostile and uh the
assistant executive director introduced me to the uh technology leader for this new project we’re working on and she
says I want to introduce you to MOSI and here’s what you need to know MOSI will always tell you the truth even if it’s
not in his best interest because his little firm came in here and they gave us a report that was
politically awful but they told us the truth anyway even it could have cost
them all millions of dollars in business with the municipality so you can always trust what they say is going to be the
truth so that’s the first step I think is lead with truth um is always you’re always going to be in Solid Ground even
Getting Executive Buy-In (Truth vs. Fear)
if it’s painful right um and in the end when people re when that truth resonates
right people will know what they need to do um and understand it so while I me my
execution of shock management into action could have been better in the end it did get management to take action
right so leave with truth um not hyperboy so that’s why I could have I should have toned it down a bit because I really like amped it up it was like
reading like tabloid headlines it was it was awful um no no need do you stay
exactly um so I think so leave with truth and not hyperbole um but the the
other thing is and I think what really saved this is we didn’t just go into that meeting with these
inflammatory headlines but we had solutions that we proposed y um for those identified problems and so like
you know so never if if you’re leading with truth and that truth may be painful to swallow
um don’t bring someone the problem without a solution right um and you know I hear from other
colleagues that uh that that happens a lot in these in these meetings where
people are trying to present to Executive teams um where the the you know the first question is so what what
do I do about it right and then the and the the response could be like hemming and Hauling and or the well it depends
right I think you got to have a clear solution that you propose um and then I
think you and then the final thing think you got to be able to demonstrate value creation for that from that solution
whether it’s direct or indirect so whether it’ll directly address some uh third you know some customer security
requirement right for a deal that you really want to close or that’s important for a group of customers a class of
customers or accounts that are important to the organization or if it’s indirect uh value where it will
um indirect value that will uh enable enable people to move up the value chain
right so like especially we talked about compliance going through this digital transformation and a lot of people try
to think about it in terms of automating manual processes right for the purpose of Saving Time right and eliminating
redundant task or tedious tasks and I don’t really think that the value there comes from
the elimination of time and it not that there isn’t some value there there is but I don’t think
anybody can really communicate very well because like none of us are really punching the clock right so we
don’t have good mechanisms for tracking time spent exactly um and I’ve tried a lot of them as a consultant who worked
on billable hours like like everything from having like things that monitor how long I had executables running or
windows open on my laptop uh to you know starting timers and J tickets right so
nobody has that so that date is not reliable um or it’s only reliable to a certain extent um but I think the value
of it comes from elevating people from to a higher
level of work so for example instead of just collecting like the the mundane task of collecting evidence from a
system elevating them from doing the collection to doing the evaluation of the evidence right so just instead of just
providing you know evidence that the information exists an evaluation of what
is the information telling us yeah right like where is the signal and all this noise got it and what should we do about
Inheriting a GRC Program (Evaluate & Optimize)
it and then that kind of reinforces the other thing of now maybe you can propose a better solution if you have a better sense of the problem that was identified
in the evidence you collected right got it no I I think that is that is very very interesting Mery so what would you
say to somebody who is who’s inheriting a program right I mean this has been there happening for some time now you’re
asking them to sort of change the tires while driving right how do you how they inter and how they go about this
I think um so one thing I started to realize and
this is you know this realization kind of started in uh conversations with you um it’s probably what 18 months ago now
is uh is I realized like okay the first a
tool I I needed a better tool or a better approach to identify where the
security compliance program is and where does it need to be and a lot of times
that looks like like a maturity model um but the maturity model wasn’t really sufficient for what for the answers I
was looking for the insights I was looking for like maybe the context I was looking for so as I was thinking about I
thought about it in this idea of these four quadrants of security compliance I think I’ve seen it before the the static
and the friendly and the adversary adversary and the friendly and the static and the dynamic assessments right
yeah so there’s AIS of Engagement and environment right and so how do
stakeholders how does the third line engage with the compliance program is it adversarial or is it friendly and then
what is the environment for the scope of the compliance program right is it a static environment or is it a dynamic
environment and thinking of it that way gave me and I it gave me a better way to
figure out okay this is what the program was designed for and is that still fit for purpose
and if not why not and what is and so I think a lot of
organizations uh their compliance programs were you know created in the time where the environments were static
right like I remember um like I was thinking about like that Municipal I
started out like Finance reporting systems right doing it audits with them and it was routine that the best
practice was you don’t update the revenue generating systems but once a
year right and everything was designed to not touch the revenue generating systems unless it was absolutely
necessary and so like a lot of compliance programs were built around that mindset is these are the uh
sensitive systems for compliance and so we don’t touch this environment the the
whole goal is to control it to the point that nothing changes because every change leads all this additional compliance work y um but now that we
went through digital transformation right we introduced these different concepts of working you know from
waterfall to Agile and and devops the environments become more dynamic they
went from being you know these controlled systems uh in someone’s building to these systems in someone
else’s building managed by their staff right um up to a certain point of the
stack you know the things have become more Dynamic and the compliance programs need to adjust for that and also um it
went from you know I talked about how when I first got into security GRC um
and the decision for the consulting firm was to focus on ISO 2701 because the world was becoming flat uh from a global
business standpoint and that also adds dynamism to the environment right so instead of just having to comply with
Future of GRC & Digital Transformation
domestic requirements for doing business now you have to comply with International requirements for doing business or if you’re looking to expand
into other markets what are the requirements for those markets or if you’re trying to grow your total addressable Market to different
customers well what are the requirements for those customers as compared to the you know the typical customer that the
business was created to serve so all that dynamism I think um you have to
understand that and if you and if you don’t then you’d be tough figuring it out or it definitely be tough to figure out how you create value if you don’t
understand why your why what trust people need from your program in the first place absolutely ABS I I think
there’s a lot of wisdom that you pack in there most and if somebody wants to look at that is there a place where they can
go look at the the four quadrant Matrix uh yeah so I did actually did a
presentation um with my boss at Netflix Charles naatu uh we did a a presentation
for uh cers um they do this engage speaker series and so uh you can go to
their YouTube channel and we’ll put a link on the podcast but thank you that’s that’s sort of actually fantastic most
you know I sincerely appreciate it um what would you
tell the younger self mosy or I think sort of differently put right if a new
for a new person who’s entering into the security and GRC program to the security compliance engineer to the GRC analyst
what would your advice be right um and where where can they get started especially in environment where they say
we have it all automated right to to the example that you were giving earlier right we we have you know we have the
intrusion prevention system system things like that how what do you what do you what do you advise them where do where can they get
started I would if they have everything automated and they passed the audit
right and as far as they’re concerned or maybe as far as their bosses are concerned right everything is good with
compliance um I think I would now you can take
things to another level right and now you can start to Pivot to some of these areas or these ideas that we talked
about that are less mature or less understood or practice like you know can you pivot from a value
protection model to a value creation model right so um how do you make your
program more valuable um how do you drive things forward for your stakeholders uh in terms of uh providing
value to employees customers you know suppliers and partners you shareholders
and communities and uh another thing I would do is if if you’ve got everything
automated and you’re passing the audits then maybe you can also try to make that
pivot from risk based to trust based right like if you got a good handled of controlling things from going
wrong how do you get assurance that things are going right
yep yep now I think that is fantastic mercy and
um we are approaching almost at the end of the program and given sort of all the wealth
of the experience that you have if you were to dream of a security
GRC solution what would that look like what would those attributes
be o so I think it kind of goes back to one
The Perfect GRC Solution (Automated Compliance)
thing I said earlier is at a fundamental level it would have a you know user interface and uh a user
experience that engages those key stakeholders where they like to work right so that first line second line and
third line that we talked about those you know employees shareholders communities suppliers um it would it
would it would start there uh customers and and that is an ambitious asking of itself I know that’s like a
utopian idea that you serve all those different populations in a way that makes them all happy um but that that
would be my dream uh so that that’s one thing um and then more specifically I I
I you know I think about it in the terms of those seven processes um and so like from a context standpoint I would love
to have like sensors that you know gather and process contextual information um maybe in a way similar to
what we see with threaten intelligence Services um they’re taking a whole this ocean of information and then it
distills it down into things that are relevant um so I would love to have something
automatically sense and gather context um and distill it for the separate the signal from the
noise separate the signal from the noise that’s right right
um and then uh but I mean but broader than just like thread Intel you things
like hey like we talk about those four quadrants like what are changes in the environment right what are some
regulatory issues that are going on or what is these customer complaints in this region um got where do we see
moments of Truth failing right and we want to change the trust narrative there right all that kind of context right at
a at a business or organizational level and Community level um so um from a
leadership standpoint I I would love to have a platform that had uh you know
workflows that made it simple for leadership to adjust strategy you know
make additions to the strategy based on that distilled contextual information that we got now from this dream platform
um and I would I would love it if we could even automate you know the recommendations for you know policy
positions or allocation roles and responsibilities right like hopefully from some Trust AI
Source um from a planning standpoint you know I
think as this is a dream but even my my dream is still limited anchored in
reality a little bit um I would love to have workflows in the system to support quantitative risk and Trust management
because you know I don’t think we’re settled there yet um I I’ll pick quantitative over qualitative um and you
know maybe in in my dream it be something to kind of mash together the fair controls analytics model and the
open- source security testing methodology manual trust principes approach or trust assessment approach
maybe something mashes those together um and of course you know automated
recommendations for you know like objectives and key results to measure the risk and Trust management I think
would be fantastic uh from a support standpoint I would want Integrations uh out the wazo right like
Integrations with the accounting system so that we can for our resource management um a procurement platform um
the hris um you know for that resource and competency management um whatever the
Recommended Books & Podcasts
communication platforms are for the like the email platform the uh chat Ops
platform or collaboration platforms uh the Knowledge Management platform so that I can cover the awareness U coms
and the document management right so I would want integration with those uh for operations I would want to
have an integration with the project management system right so that people if people have a way they like to work
the system doesn’t step on their toes for that right it it fits right in um and then uh for performance
evaluation you know we you know nowadays the talk is like data Fabrics so you know it’s got to have like a data Fabric
and some business intelligence for metrics and Reporting um because you know dealing with a lot of data and like
you said we’ve got to find a way to get signal out of all the noise um
and then from an improvement standpoint U you know just a workflow for
corrective action and continuous Improvement where it has but it’s got that human in the loop where maybe it’s
an automatically generated recommendation and Remediation where possible right if we really got our our
stuff together our asset management and configuration management together um but that human in the loop that says yes
this is what we want to do or tweak it as possible before we push those changes you know into operation
you definitely do have a dream I think you dream a lot m i mean I was not expecting a you gave me a scientific
breakdown of of sort of your dream from GRC Solution that’s fantastic I I love
it um it’s almost like you you want to build an autonomous GRC Solution that’s what it looks like or an agentic GRC
platform yeah right but with yeah agentic with you know with humans in the loops at these key checkpoints
absolutely absolutely no mostly I think this is been a lot of fun and I wanted to sort of end the um end the podcast
with this question I know you are a fantastic reader you’re a voracious reader are there any um podcasts Audi
books books that you read listen that you can share with our listeners and why
and what what is that that is I mean maybe if you can describe why you like them I think few of them that would be
super helpful sure so you know I’ve I think these days I’m more of a raous
listener than reader because a lot of my consumption is switch to audio
Final Thoughts & Key Takeaways
um but uh from a book standpoint uh I think you know we talked about security
compliance undergoing its own digital transformation and you know how that’s been influenced it needs to be follow
some of the lessons learned from devops I think there’s a it revolution has a great book on that um Investments
unlimited from the same group that published the devops handbook um the Phoenix project I think the invest
unlimited book is y excellent um and then on the from a book
stamp on the I have a fiction book that I always recommend to people um it’s a
short story by my my currently favorite uh sci-fi author in K Json it’s called
emergency skin uhhuh and it’s a short story about uh about a human who comes back to Earth
after uh her people have left the Earth because of climate catastrophes and just
general degradation of living conditions on the planet and they come back to the planet for resources and it’s a short
story about what they find when they come back and I I I won’t ruin it for anybody but it’s an it’s just an amazing
story about um what humanity is capable
of with cooperation and it’s also wickedly funny
because like and I that’s why I recommend the audio book because the narrator just the the the way they in
tone certain phrases it’s it’s I don’t know I think they had to intend for it to be comedic but it’s it’s hilarious
the some of the things that the it’s a the human that comes back they have an AI assisting them on their trip and so
like the things that the AI says to the human this just hilarious that you have this machines perspective and this human
perspective was this book written to you know oh this probably came out three
years ago maybe three or four years ago okay um it was um audible commissioned
these the series of short stories um and so that’s and so you know they they were marketing it and so they push it to me
in my audible uh app so I stumbled on it but it’s so it’s fantastic really the
the the the the jewel of it is the story about human what is capable when Humanity cooperates
so I think that’s an inspiring story um and then I say I do more listening
than reading so uh big on podcast and so uh I think the podcast I
from a security standpoint the podcast I probably get the most from is Enterprise security weekly which the the main host
is Adrien sarria and so they do a great job of you know reporting on the industry in terms
of uh startups Acquisitions mergers um but then they also summarize you know
articles about thought leadership um and and now they’ve expanded it with
uh I think Darwin Salazar is his name so now that he’s been added they they also
cover reporting on uh product or technology capabilities that announcements so like new products new
features um Darwin does a great job bringing that so I it’s a really comprehensive podcast um that really
keeps me up to date on where things are in the industry and from a practitioner standpoint
and then I think to compliment that is uh the center for Internet Security started a podcast which they have now
over a 100 episodes of is a cyber security where you are and you know I think I’ve talked
earlier about um meeting people where they’re at that where the stakeholders
are um and so that’s kind of the intent of that podcast and that’s how they talk about cyber security and I think they do
a fantastic job of it um got it Sean ainson is the ceso there and he’s one of the smartest people I ever work with
absolutely absolutely agree cyber security so absolutely I I I I think MOSI we will
get the links from you and we’ll put them on the podcast the the comment section mosie um thanks for being part
you know being part of the security and GRC and you have truly decoded security and GRC I think it is nothing short of
an inspirational podcast for me and I’m sure our listeners will agree as well so thank you very much for for for thanks
for letting me ramble on rer I appreciate [Applause]
[Music]
Listen on your favorite platform and stay updated with the latest insights, stories, and interviews.
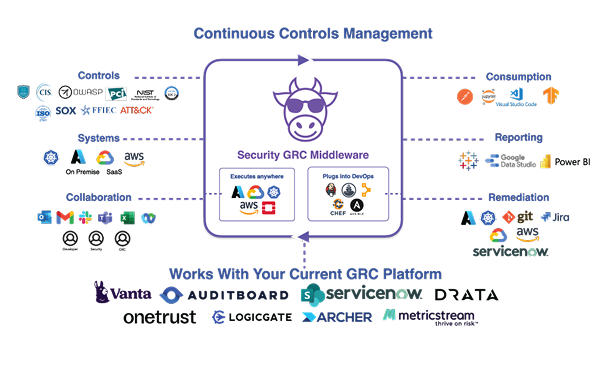
Want to see how we can help your team or project?
Book a Demo